You need to identify the time-to-live (TTL) value for domain referrals to the NETLOGON and SYSVOL shared folders.
Which tool should you use?
A. Ultrasound
B. Replmon
C. Dfsrdiag
D. Frsutil
ANSWER: C. Dfsrdiag
Q2. Your company recently deployed a new Active Directory forest named contoso.com. The forest contains two Active Directory sites named Site1 and Site2. The first domain controller in the forest runs Windows Server 2012 R2.
You need to force the replication of the SYSVOL folder from Site1 to Site2.
Which tool should you use?
A. Active Directory Sites and Services
B. DFS Management
C. Repadmin
D. Dfsrdiag
ANSWER: D. Dfsrdiag (Dfsrdiag PollAD switch command)
Explanation: D. In Windows Server 2012 R2, Windows Server 2008 R2, or Windows Server 2008, you can force replication immediately by using DFS Management, as described in Edit Replication Schedules. You can also force replication by using the Dfsrdiag SyncNow command. You can force polling by using the Dfsrdiag PollAD command.
Q3. You have 20 servers that run Windows Server 2012 R2.
You need to create a Windows PowerShell script that registers each server in Windows Azure Online Backup and sets an encryption passphrase.
Which two PowerShell cmdlets should you run in the script? (Each correct answer presents part of the solution. Choose two.)
A. New-OBPolicy
B. New-OBRetentionPolicy
C. Add-OBFileSpec
D. Start-OBRegistration
E. Set-OBMachineSetting
ANSWER: DE. Start + Set
Explanation: Start-OBRegistration registers current computer with Windows Azure Online Backup using credentials created during enrollment.
Set-OBMachineSetting sets a OBMachineSetting object for the server that includes proxy server settings for accesing the internet, nwtwork bandwidth, and the encryption passphrase required to decrypt the files during recovery to another server.
Q4. You have 20 servers that run Windows Server 2012 R2. You need to create a Windows Powershell script that registers each server in Windows Azure Backup and sets an encryption passphrase. Which two Powershell cmdlets should you run in the script? (Each correct answer presents part of the solution. Choose two.)
A. New-OBPolicy
B. Add-OBFileSpec
C. Start-OBRegistration
D. New-OBRetentionPolicy
E. Set-OBMachineSetting
ANSWER: CE. Set + Start.
Q5. Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2. The volumes on Server1 are configured as shown in the following table.
A new corporate policy states that backups must use Windows Azure Online Backup whenever possible.
You need to identify which backup methods you must use to back up Server1. The solution must use Windows Azure Online Backup whenever possible. Which backup type should you identify for each volume? To answer, select the appropriate backup type for each volume in the answer area.
ANSWER:
Folder1: WAOB
Folder2: WAOB
Folder3: WAOB
System State; Windows Server Backup
Explanation:Folder2: WAOB
Folder3: WAOB
System State; Windows Server Backup
Q6. Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2. The volumes on Server1 are configured as shown in the following table.
A new corporate policy states that backups must use Windows Azure Online Backup whenever possible.
You need to identify which backup methods you must use to back up Server1. The solution must use Windows Azure Online Backup whenever possible.
Which backup type should you identify for each volume? To answer, select the appropriate backup type for each volume in the answer area.
ANSWER:
You have 3 server named Server1 that runs Windows Server 2012 R2.
You are asked to test Windows Azure Online Backup to back up Server1.
You need to back up Server1 by using Windows Azure Online Backup. Which four actions should you perform in sequence? To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order.
Sign up for a Microsoft Online Services account.
Download the Windows Azure Online Backup agent.
Run the Windows Azure Online Backup Agent Setup Wizard
Run the Register Server Wizard
Q8. Your network contains an Active Directory domain named contoso.com. A previous administrator implemented a Proof of Concept installation of Active Directory Rights Management Services (AD RMS). After the proof of concept was complete, the Active Directory Rights Management Services server role was removed. You attempt to deploy AD RMS. During the configuration of AD RMS, you receive an error message indicating that an existing AD RMS Service Connection Point (SCP) was found.
You need to remove the existing AD RMS SCP.
Which tool should you use?
A. ADSI Edit
B. Active Directory Users and Computers
C. Active Directory Domains and Trusts
D. Active Directory Sites and Services
E. Services
F. Authorization Manager
G. TPM Management
H. Certification Authority
ANSWER: AD. ADSI Edit + Active Directory Sites and Services
http://social.technet.microsoft.com/wiki/contents/articles/710.the-ad-rms-service-connection-point.aspx
![clip_image001[50]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00150_thumb.jpg)
![clip_image001[84]](http://examgod.com/l2pimages/f98e0646ba5b_79CB/clip_image00184_thumb.jpg)
Q9. Your network contains an Active Directory domain named contoso.com. A previous administrator implemented a Proof of Concept installation of Active Directory Rights Management Services (AD RMS). After the proof of concept was complete, the Active Directory Rights Management Services server role was removed. You attempt to deploy AD RMS. During the configuration of AD RMS, you receive an error message indicating that an existing AD RMS Service Connection Point (SCP) was found.
You need to remove the existing AD RMS SCP.
Which tool should you use?
A. Active Directory Users and Computers
B. Active Directory Domains and Trusts
C. Active Directory Sites and Services
D. Authorization Manager
ANSWER: C. Active Directory Sites and Services
Q10. Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. You are creating a central access rule named TestFinance that will be used to audit members of the Authenticated Users group for access failure to shared folders in the finance department. You need to ensure that access requests are unaffected when the rule is published.
What should you do?
A. Add a User condition to the current permissions entry for the Authenticated Users principal.
B. Add a Resource condition to the current permissions entry for the Authenticated Users principal.
C. Set the Permissions to Use following permissions as current permissions.
D. Set the Permissions to Use the following permissions as proposed permissions.
ANSWER: D. Set the Permissions to Use the following permissions as proposed permissions.
Q11. Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2.
You are creating a central access rule named TestFinance that will be used to grant members of the Authenticated users group access to a folder stored on a Microsoft SharePoint Server 2013 server.
You need to ensure that the permissions are granted when the rule is published.
What should you do?
A. Set the Permissions to Use the following permissions as proposed permissions.
B. Set the Permissions to Use following permissions as current permissions.
C. Add a Resource condition to the current permissions entry for the Authenticated Users principal.
D. Add a User condition to the current permissions entry for the Authenticated Users principal.
ANSWER: B. Set the Permissions to Use following permissions as current permissions.
Q12. You have a server named Server1 that runs Windows Server 2012 R2. Each day, Server1 is backed up fully to an external disk. On Server1, the disk that contains the operating system fails. You replace the failed disk. You need to perform a bare-metal recovery of Server1 by using the Windows Recovery Environment (Windows RE). What should you use?
A. Run the wbadmin.exe start sysrecovery command and specify the -backuptarget parameter.
B. The Get-WBBareMetalRecovery cmdlet and specify the -policy parameter.
C. Run the wbadmin.exe start recovery command and specify the -recoverytarget parameter.
D. The Start-WBVolumeRecovery cmdlet and specify the -backupset parameter.
ANSWER: A. Run the wbadmin.exe start sysrecovery command and specify the -backuptarget parameter.
Q13. You have a server named Server1 that runs Windows Server 2012 R2. Each day, Server1 is backed up fully to an external disk. On Server1, the disk that contains the operating system fails.
You replace the failed disk. You need to perform a bare-metal recovery of Server1 by using the Windows Recovery Environment (Windows RE).
What should you use?
A. The Wbadmin.exe command
B. The Repair-bde.exe command
C. The Get-WBBareMetalRecovery cmdlet
D. The Start-WBVolumeRecovery cmdlet
ANSWER: A. The Wbadmin.exe command
Q14. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Network Load Balancing (NLB) feature installed. The servers are configured as nodes in an NLB cluster named Cluster1.
Cluster1 hosts a secure web application named WebApp1. WebApp1 saves user state information locally on each node.
You need to ensure that when users connect to WebApp1, their session state is maintained. What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: B. Affinity-Single
Q15. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. You add two additional nodes to Cluster1.
You have a folder named Folder1 on Server1 that contains application data. You plan to provide continuously available access to Folder1. You need to ensure that all of the nodes in Cluster1 can actively respond to the client requests for Folder1.
What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: L. The Scale-Out File Server
Q16. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 hosts an application named App1.
You need to ensure that Server2 handles all of the client requests to the cluster for App1. The solution must ensure that if Server2 fails, Server1 becomes the active node for App1.
What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: J. The preferred owner
Q17. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2.
Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1.
You add two additional nodes to Cluster1.
You need to ensure that Cluster1 stops running if three nodes fail.
What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: C. The cluster quorum settings
Q18. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. You add two additional nodes in Cluster1.
You have a folder named Folder1 on Server1 that hosts application data. Folder1 is a folder target in a Distributed File System (DFS) namespace.
You need to provide highly available access to Folder1. The solution must support DFS Replication to Folder1.
What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: E. A file server for general use.
Q19. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Network Load Balancing (NLB) feature installed. The servers are configured as nodes in an NLB cluster named Cluster1.
Port rules are configured for all clustered applications. You need to ensure that Server2 handles all client requests to the cluster that are NOT covered by a port rule.
What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: G. The host priority
Q20. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. You add two additional nodes to Cluster1. You have a folder named Folder1 on Server1 that contains application data. You plan to provide continuously available access to Folder1. You need to ensure that all of the nodes in Cluster1 can actively respond to the client requests for Folder1. What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: L. The Scale-Out File Server
Q21. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1.
You configure File Services and DHCP as clustered resources for Cluster1. Server1 is the active node for both clustered resources. You need to ensure that if two consecutive heartbeat messages are missed between Server1 and Server2, Server2 will begin responding to DHCP requests.
The solution must ensure that Server1 remains the active node for the File Services clustered resource for up to five missed heartbeat messages.
What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: D. The failover settings
Q22. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 hosts an application named App1. You need to ensure that Server2 handles all of the client requests to the cluster for App1. The solution must ensure that if Server2 fails, Server1 becomes the active node for Appl. What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: J. The preferred owner
Q23. Information and details provided in a question apply only to that question. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Network Load Balancing (NLB) feature installed. The servers are configured as nodes in an NLB cluster named Cluster1. Port rules are configured for all clustered applications. You need to ensure that Server2 handles all client requests to the cluster that are NOT covered by a port rule. What should you configure?
A. Affinity-None
B. Affinity-Single
C. The cluster quorum settings
D. The failover settings
E. A file server for general use
F. The Handling priority
G. The host priority
H. Live migration
I. The possible owner
J. The preferred owner
K. Quick migration
L. The Scale-Out File Server
ANSWER: G. The host priority
Q24. Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You have a failover cluster named Cluster1 that contains two nodes named Server1 and Server2. Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed.
You plan to create two virtual machines that will run an application named App1. App1 will store data on a virtual hard drive named App1data.vhdx. App1data.vhdx will be shared by both virtual machines.
The network contains the following shared folders:
- An SMB file share named Share1 that is hosted on a Scale-Out File Server.
- An SMB file share named Share2 that is hosted on a standalone file server.
- An NFS share named Share3 that is hosted on a standalone file server.
You need to ensure that both virtual machines can use App1data.vhdx simultaneously.
What should you do?
To answer, select the appropriate configurations in the answer area.
ANSWER:
Location of App1data.vhdx: Share1
App1data.vhdx disk type: Dynamically expanding
Q25. You have a file server named Server1 that runs Windows Server 2012 R2.
You need to ensure that you can use the NFS Share - Advanced option form the New Share Wizard in Server Manager.
Which two role services should you install?
To answer, select the appropiate two role services in the answer area.
ANSWER:
File Server Resource Manager
Server for NFS
Q26. Drag and Drop QuestionYour network contains four servers that run Windows Server 2012 R2. Each server has the Failover Clustering feature installed. Each server has three network adapters installed. An iSCSI SAN is available on the network.
You create a failover cluster named Cluster1.
You add the servers to the cluster.
You plan to configure the network settings of each server node as shown in the following table.
You need to configure the network settings for Cluster1.
What should you do?
To answer, drag the appropriate network communication setting to the correct cluster network. Each network communication setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:
ANSWER:
Network1: Allow
Network2: Allow
Network3: Dont allow
Q27. Your network contains two application servers that run Windows Server 2012 R2. The application servers have the Network Load Balancing (NLB) feature installed.
You create an NLB cluster that contains the two servers.
You plan to deploy an application named App1 to the nodes in the cluster. App1 uses TCP port 8080 and TCP port 8081.
Clients will connect to App1 by using HTTP and HTTPS via a single reverse proxy. App1 does not use session state information.
You need to configure a port rule for App1. The solution must ensure that connections to App1 are distributed evenly between the nodes.
Which port rule should you use? To answer, select the appropiate rule in the answer area.
Q28. Hotspot Question
Your network contains three Application servers that run Windows Server 2012 R2. The Application servers have the Network Load Balancing (NLB) feature installed. You create an NLB cluster that contains the three servers. You plan to deploy an Application named App1 to the nodes in the cluster. App1 uses TCP port 8080 and TCP port 8081.
Clients will connect to App1 by using HTTP and HTTPS. When clients connect to App1 by using HTTPS, session state information will be retained locally by the cluster node that responds to the client request.
You need to configure a port rule for App1. Which port rule should you use? To answer, select the appropriate rule in the answer area.
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0028_thumb.jpg)
Q29. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Network Load Balancing (NLB) feature installed. The servers are configured as nodes in an NLB cluster named Cluster1. Both servers connect to the same switch. Cluster1 hosts a secure web application named WebApp1. WebApp1 saves user state information in a central database.
You need to ensure that the connections to WebApp1 are distributed evenly between the nodes.
The solution must minimize port flooding.
What should you configure? To answer, configure the appropriate affinity and the appropriate mode for Cluster1 in the answer area.
ANSWER:
Affinity: Single
Mode: Multicast
Q30. Your network contains two servers named Server1 and Server2 that run Windows Server 2008 R2. Server1 and Server2 are nodes in a failover cluster named Cluster1.
The network contains two servers named Server3 and Server4 that run Windows 2012 R2. Server3 and Server4 are nodes in a failover cluster named Cluster2.
You need to move all of the applications and the services from Cluster1 to Cluster2.
What should you do first from Failover Cluster Manager?
A. On a server in Cluster1, click Migrate Roles.
B. On a server in Cluster2, configure Cluster-Aware Updating.
C. On a server in Cluster1, click Move Core Cluster Resources, and then click Best possible Node.
D. On a server in Cluster2, click Move Core Cluster Resources, and then click Best possible Node.
ANSWER: B. On a server in Cluster1, click Migrate Roles.
Q31. Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role installed. Server1 and Server2 are configured as Hyper-V replicas of each other.
Server2 hosts a virtual machine named VM5. VM5 is replicated to Server1.
You need to verify whether the replica of VM5 on Server1 is functional. The solution must ensure that VM5 remains accessible to clients.
What should you do from Hyper-V Manager?
A. On a server in Cluster2, click Migrate Roles.
B. On a server in Cluster2, configure Cluster-Aware Updating.
C. On a server in Cluster1, click Move Core Cluster Resources, and then click Select Node.
D. On a server in Cluster1, configure Cluster-Aware Updating.
ANSWER: B. On a server in Cluster2, configure Cluster-Aware Updating.
Q32. Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role installed. Server1 and Server2 are configured as Hyper-V replicas of each other.
Server2 hosts a virtual machine named VM5. VM5 is replicated to Server1.
You need to verify whether the replica of VM5 on Server1 is functional. The solution must ensure that VM5 remains accessible to clients.
What should you do from Hyper-V Manager?
A. On Server1, execute a Test Failover.
B. On Server1, execute a Planned Failover.
C. On Server2, execute a Test Failover.
D. On Server2, execute a Planned Failover.
ANSWER: A. On Server1, execute a Test Failover.
Q33. Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 and a member server named Server1. Server1 has the IP Address Management (IPAM) Server feature installed. On Dc1, you configure Windows Firewall to allow all of the necessary inbound ports for IPAM. On Server1, you open Server Manager as shown in the exhibit. (Click the Exhibit button.)
You need to ensure that you can use IPAM on Server1 to manage DNS on DC1. What should you do?
A. Modify the outbound firewall rules on Server1.
B. Modify the inbound firewall rules on Server1.
C. Add Server1 to the Remote Management Users group.
D. Add Server1 to the Event Log Readers group.
ANSWER: D. Add Server1 to the Event Log Readers group.
Q34. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named DHCP1 and DHCP2 that run Windows Server 2012 R2.
You install the IP Address Management (IPAM) Server feature on a member server named Server1 and you run the Run Invoke-IpamGpoProvisioning cmdlet.
You need to manage the DHCP servers by using IPAM on Server1. Which three actions should you perform?
To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
Provision the IPAM server.
Configure server discovery
Set the manageability status of the server
Q35. You have a server named Server1 that runs Windows Server 2012 R2. Server1 is located in the perimeter network and has the DNS Server server role installed. Server1 has a zone named contoso.com. You apply a security template to Server1. After you apply the template, users report that they can no longer resolve names from contoso.com. On Server1, you open DNS Manager as shown in the DNS exhibit. (Click the Exhibit button.)
On Server1, you open Windows Firewall with Advanced Security as shown in the Firewall exhibit. (Click the Exhibit button.)
You need to ensure that users can resolve contoso.com names. What should you do?
A. From Windows Firewall with Advanced Security, disable the DNS (TCP, Incoming) rule and the DNS (UDP, Incoming) rule.
B. From DNS Manager, modify the Zone Transfers settings of the contoso.com zone.
C. From DNS Manager, unsign the contoso.com zone.
D. From DNS Manager, modify the Start of Authority (SOA) of the contoso.com zone.
E. From Windows Firewall with Advanced Security, modify the profiles of the DNS (TCP, Incoming) rule and the DNS (UDP, Incoming) rule.
ANSWER: E. From Windows Firewall with Advanced Security, MODIFY the profiles of the DNS (TCP, Incoming) rule and the DNS (UDP, Incoming) rule.
Q36. You have a server named Server1. You install the IP Address Management (IPAM) Server feature on Server1.
You need to provide a user named User1 with the ability to set the access scope of all the DHCP servers that are managed by IPAM. The solution must use the principle of least privilege.
Which user role should you assign to User1?
A. IPAM Administrator Role
B. IPAM DHCP Administrator Role
C. IPAM ASM Administrator Role
D. DNS Record Administrator Role
ANSWER: B. IPAM DHCP Administrator Role (http://technet.microsoft.com/en-us/library/dn268500.aspx)
Q37. Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 Both servers have the IP Address Management (IPAM) Server feature installed.
You have a support technician named Tech1. Tech1 is a member of the IPAM Administrators group on Server1 and Server2.
You need to ensure that Tech1 can use Server Manager on Server1 to manage IPAM on Server2.
To which group on Server2 should you add Tech1?.
A. IPAM MSM Administrators
B. IPAM Administrators
C. winRMRemoteWMIUsers_
D. Remote Management Users
ANSWER: C. winRMRemoteWMIUsers_
Explanation:
A. IPAM MSM Administrators can’t access remotely
B. IPAM Administrators can’t access remotely
C. If you are accessing the IPAM server remotely using Server Manager IPAM client RSAT, then you must be a member of the WinRMRemoteWMIUsers group on the IPAM server, in addition to being a member of the appropriate IPAM security group (or local Administrators group).
Q38. Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. Both servers have the IP Address Management (IPAM) Server feature installed. You have a support technician named Tech1. Tech1 is a member of the IPAM Administrators group on Server1 and Server2. You need to ensure that Tech1 can use Server Manager on Server1 to manage IPAM on Server2. To which group on Server2 should you add Tech1? To answer, select the appropriate group in the answer area.
![clip_image001[98]](http://examgod.com/l2pimages/f98e0646ba5b_79CB/clip_image00198_thumb.jpg)
ANSWER: winRMRemoteWMIUsers_
![clip_image001[100]](http://examgod.com/l2pimages/f98e0646ba5b_79CB/clip_image001100_thumb.jpg)
Q39. Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
Server1 has the IP Address Management (IPAM) Server feature installed.
Server2 has the DHCP Server server role installed.
A user named User1 is a member of the IPAM Users group on Server1. You need to ensure that User1 can use IPAM to modify the DHCP scopes on Server2. The solution must minimize the number of permissions assigned to User1.
To which group should you add User1?
A. DHCP Administrators on Server2.
B. IPAM ASM Administrators on Server1
C. IPAMUG in Active Directory.
D. IPAM MSM Administrators on Server1.
ANSWER: A. DHCP Administrators on Server2.
Q40. Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server1. Server1 has the IP Address Management (IPAM) Server feature installed.
A technician performs maintenance on Server1.
After the maintenance is complete, you discover that you cannot connect to the IPAM server on Server1.
You open the Services console as shown in the exhibit. (Click the Exhibit button.)
You need to ensure that you can connect to the IPAM server.
Which service should you start?
A. Windows Process Activation Service
B. Windows Event Collector
C. Windows Internal Database
D. Windows Store Service (WSService)
ANSWER: C. Windows Internal Database
Q41. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DHCP Server server role installed. An administrator installs the IP Address Management (IPAM) Server feature on a server named Server2. The administrator configures IPAM by using Group Policy based provisioning and starts server discovery. You plan to create Group Policies for IPAM provisioning. You need to identify which Group Policy object (GPO) name prefix must be used for IPAM Group Policies.
What should you do on Server2?
A. From Server Manager, review the IPAM overview.
B. Run the ipamgc.exe tool.
C. From Task Scheduler, review the IPAM tasks.
D. Run the Get-IpamConfiguration cmdlet.
ANSWER: A. From Server Manager, review the IPAM overview.
Q42. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 and a member server named Server1. All servers run Windows Server 2012 R2. Q42. Hotspot Question
You install the IP Address Management (IPAM) Server feature on Server1.
From the Provision IPAM wizard, you select the Group Policy Based provisioning method and enter a GPO name prefix of IPAM1.
You need to provision IPAM by using Group Policy.
What command should you run on Server1 to complete the process?
To answer, select the appropriate options in the answer area.
Invoke-IpamGPOProvisioning -Domain Contoso.com -GPOPrefixName Ipam1
Q43. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2.
Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 contains a Clustered Shared Volume (CSV).
A developer creates an Application named App1. App1 is NOT a cluster-aware Application. App1 stores data in the file system. You need to ensure that App1 runs in Cluster1. The solution must minimize development effort.
Which cmdlet should you run?
A. Add-ClusterGenericApplicationRole
B. Add-ClusterGenericServiceRole
C. Add-ClusterServerRole
D. Add-ClusterScaleOutFileServerRole
ANSWER: A. Add-ClusterGenericApplicationRole
Q44. Your network contains servers that run Windows Server 2012 R2. The network contains a large number of iSCSI storage locations and iSCSI clients.
You need to deploy a central repository that can discover and list iSCSI resources on the network automatically.
Which feature should you deploy?
A. the Windows Standards-Based Storage Management feature
B. the iSCSI Target Server role service
C. the iSCSI Target Storage Provider feature
D. the iSNS Server service feature
ANSWER: D. the iSNS Server service feature
Q45. Your network contains 20 iSCSI storage appliances that will provide storage for 50 Hyper-V hosts running Windows server 2012 R2.
You need to configure the storage for the Hyper-V hosts. The solution must minimize administrative effort.
What should you do first?
A. Install the iSCSI Target Server role service and configure iSCSI targets,
B. Start the Microsoft iSCSI Initiator Service and configure the iSCSI Initiator Properties.
C. Install the iSNS Server service feature and create a Discovery Domain
D. Install the Multipath I/O (MPIO) feature and configure the MPIO Properties.
ANSWER: C. Install the iSNS Server service feature.
Q46. Your network contains three servers named Server1, Server2, and Server3. All servers run Windows Server2012 R2.
You need to ensure that Server1 can provide iSCSI storage for Server2 and Server3.
What should you do on Server1?
A. Install the iSCSI Target Server role service and configure iSCSI targets.
B. Start the Microsoft iSCSI Initiator Service and configure the iSCSI Initiator Properties.
C. Install the iSNS Server service feature and create a Discovery Domain
D. Install the Multipath I/O (MPIO) feature and configure the MPIO Properties.
ANSWER: A. Install the iSCSI Target Server role service and configure iSCSI targets.
Q47. Hotspot Question
You have a server that runs Windows Server 2012 R2 and has the iSCSI Target Server role service installed.
You run the New-IscsiVirtualDisk cmdlet as shown in the New-IscsiVirtualDisk exhibit.
(Click the Exhibit button.)
To answer, complete each statement according to the information presented in the exhibits.
Each correct selection is worth one point.
ANSWER:
using 4MB GB of
assign Disk2.vhdx to a target
** Explanation: New DYNAMIC (its NOT fixed) disk using 4MB of space. Grows as data is written. Therefore 4096 Kb is the actual size of the VHDX.
Q48. You have a server named Server2 that runs Windows Server 2012 R2. You have storage provisioned on Server2 as shown in the exhibit. (Click the Exhibit button.)
You need to configure the storage so that it appears in Windows Explorer as a drive letter on Server1. Which three actions should you perform in sequence? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
On Server2, add an iSCSI initiator ID to target1.
On Server1, configure the iSCSI initiator to connect to target1.
On Server1, create a new volume from Server Manager.
Q49. Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has access to disks that connect to a RAID controller, iSCSI disks, and disks connected to a SCSI controller.
You plan to use a tiered storage space on Server1.
You need to identify which storage controller and volume type you must use for the tiered storage space.
Which storage components should you use?
To answer, select the appropriate options in the answer area.
ANSWER:
Storage controller: SCSI
Storage volume type: Storage Pool virtual disk volume
50. Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2.
You are configuring a storage space on Server1.
You need to ensure that the storage space supports tiered storage.
Which settings should you configure?
To answer, select the appropriate options in the answer area.
ANSWER:
Automatic/ Fixed
Q51. Your network contains an Active Directory domain named contoso.com. The domain contains four servers named Server1, Server2, Server3, and Server4 that run Windows Server 2012 R2. All servers have the Hyper-V server role and the Failover Clustering feature installed.
The servers are configured as shown in the following table.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. From Hyper-V Manager on a node in Cluster2, create three virtual machines.
B. From Hyper-V Manager on a node in Cluster2, modify the Hyper-V settings.
C. From Failover Cluster Manager on Cluster1, configure each virtual machine for replication.
D. From Cluster1, add and configure the Hyper-V Replica Broker role.
E. From Cluster2, add and configure the Hyper-V Replica Broker role.
ANSWER: CDE. These are two clusters, to replicate any VM to a cluster you need to configure the Replica Broker role on each cluster. Last step should be enabling replication on the VMs.
Q52. Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Both servers have the Hyper-V server role installed. Server1 and Server2 are located in different offices. The offices connect to each other by using a high-latency WAN link. Server2 hosts a virtual machine named VM1. You need to ensure that you can start VM1 on Server1 if Server2 fails. The solution must minimize hardware costs. What should you do?
A. On Server1, install the Multipath I/O (MPIO) feature. Modify the storage location of the VHDs for VM1.
B. From the Hyper-V Settings of Server2, modify the Replication Configuration settings. Enable replication for VM1.
C. On Server2, install the Multipath I/O (MPIO) feature. Modify the storage location of the VHDs for VM1.
D. From the Hyper-V Settings of Server1, modify the Replication Configuration settings. Enable replication for VM1.
ANSWER: D. From the Hyper-V Settings of Server1, modify the Replication Configuration settings. Enable replication for VM1.
Q53. You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the DNS Server server role installed. You need to store the contents of all the DNS queries received by Server1. What should you configure?
A. Logging from Windows Firewall with Advanced Security
B. Debug logging from DNS Manager
C. A Data Collector Set (DCS) from Performance Monitor
D. Monitoring from DNS Manager
ANSWER: B. Debug logging from DNS Manager
Q54. Your network contains an Active Directory forest named contoso.com. The forest contains two domains named contoso.com and child1.contoso.com. The domains contain three domain controllers. The domain controllers are configured as shown in the following table.
You need to ensure that the KDC support for claims, compound authentication, and kerberos armoring setting is enforced in the child1.contoso.com domain.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Upgrade DC1 to Windows Server 2012 R2.
B. Upgrade DC11 to Windows Server 2012 R2.
C. Raise the domain functional level of child1.contoso.com.
D. Raise the domain functional level of contoso.com.
E. Raise the forest functional level of contoso.com.
ANSWER: BC. Upgrade DC11 + Raise functional level child1.contoso.com
*Explanation: If you want to create access control based on claims and compound authentication, you need to deploy Dynamic Access Control. This requires that you upgrade to Kerberos clients and use the KDC, which support these new authorization types. With Windows Server 2012 R2, you do not have to wait until all the domain controllers and the domain functional level are upgraded to take advantage of new access control options.
Q55. Your network contains an Active Directory forest named contoso.com. The forest contains two domains named contoso.com and child1.contoso.com. The domains contain three domain controllers. The domain controllers are configured as shown in the following table.
You need to ensure that the KDC support for claims, compound authentication, and kerberos armoring setting is enforced in both domains.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Upgrade DC1 to Windows Server 2012 R2.
B. Upgrade DC11 to Windows Server 2012 R2.
C. Raise the domain functional level of child1.contoso.com.
D. Raise the domain functional level of contoso.com.
E. Raise the forest functional level of contoso.com.
ANSWER: AD. Upgrade DC1 to Windows Server 2012 R2. Raise the domain functional level of contoso.com.
Explanation: BOTH DOMAINS! => Root domain on the forest must be at Windows Server 2012 level.
First upgrade DC1 to this level, then raise contoso.com DOMAIN functional level to Windows Server 2012.
Q56. Your network contains two servers named HV1 and HV2. Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed. HV1 hosts 25 virtual machines. The virtual machine configuration files and the virtual hard disks are stored in D:\VM. You shut down all of the virtual machines on HV1.
You copy D:\VM to D:\VM on HV2.
You need to start all of the virtual machines on HV2. You want to achieve this goal by using the minimum amount of administrative effort.
What should you do?
A. Run the Import-VMInitialReplication cmdlet.
B. From HV1, export all virtual machines to D:\VM.
Copy D:\VM to D:\VM on HV2 and overwrite the existing files. On HV2, run the Import Virtual Machine wizard.
C. From HV1, export all virtual machines to D:\VM. Copy D:\VM to D:\VM on HV2 and overwrite the existing files.
On HV2, run the New Virtual Machine wizard.
D. Run the Import-VM cmdlet.
ANSWER: D. Run the Import-VM cmdlet.
Q57. Your network contains two servers named Server1 and Server 2. Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed. Server1 hosts a virtual machine named VM1. The virtual machine configuration files and the virtual hard disks for VM1 are stored in D: \VM1.
You shut down VM1 on Server1.
You copy D:\VM1 to D:\VM1 on Server2.
You need to start VM1 on Server2. You want to achieve this goal by using the minimum amount of administrative effort.
What should you do?
A. Run the Import-VMIntialReplication cmdlet.
B. Create a new virtual machine on Server2 and attach the VHD from VM1 to the new virtual machine.
C. From Hyper-V Manager, run the Import Virtual Machine wizard.
D. Run the Import-IscsiVirtualDisk cmdlet.
ANSWER: C. From Hyper-V Manager, run the Import Virtual Machine wizard.
Q58. Your network contains two Web servers named Server1 and Server2. Both servers run Windows Server 2012 R2.
Server1 and Server2 are nodes in a Network Load Balancing (NLB) cluster. The NLB cluster contains an application named App1 that is accessed by using the URL http://app1.contoso.com.
You plan to perform maintenance on Server1.
You need to ensure that all new connections to App1 are directed to Server2. The solution must not disconnect the existing connections to Server1.
What should you run?
A. The Set-NlbCluster cmdlet
B. The Set-NlbClusterNode cmdlet
C. The Stop-NlbCluster cmdlet
D. The Stop-NlbClusterNode cmdlet
ANSWER: D. The Stop-NlbClusterNode cmdlet
Q59. Hotspot Question
Your network contains two Web servers named Server1 and Server2. Both servers run Windows Server 2012 R2.
Server1 and 5erver2 are nodes in a Network Load Balancing (NLB) cluster. The NLB cluster contains an application named App1 that is accessed by using the name appl.contoso.com.
The NLB cluster has the port rules configured as shown in the exhibit. (Click the Exhibit button.)
To answer, complete each statement according to the information presented in the exhibit.
Each correct selection is worth one point.
ANSWER:
When users access the URL http://app1.contoso.com... the connections are processed by a SINGLE server
If one of the nodes in the cluster fails, App1 is..ALWAYS...available
Q60. Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 has the DNS Server server role installed. The network contains client computers that run either Linux, Windows 7, or Windows 8. You have a standard primary zone named adatum.com as shown in the exhibit. (Click the Exhibit button.)
You plan to configure Name Protection on all of the DHCP servers. You need to configure the adatum.com zone to support Name Protection. Which two configurations should you perform from DNS Manager? (Each correct answer presents part of the solution. Choose two.)
A. Sign the zone.
B. Store the zone in Active Directory.
C. Modify the Security settings of the zone.
D. Configure Dynamic updates.
ANSWER: BD. Store the zone in Active Directory + Configure Dynamic updates.
Q61. Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 has the DNS Server server role installed. The network contains client computers that run either Linux, Windows 7, or Windows 8. You have a standard primary zone named adatum.com as shown in the exhibit. (Click the Exhibit button.)
You plan to configure Name Protection on all of the DHCP servers.
You need to configure the adatum.com zone to support Name Protection.
What should you do?
A. Sign the zone.
B. Add a DNSKEY record.
C. Change the zone type.
D. Configure Dynamic updates.
ANSWER: D. Configure Dynamic updates.
Q62. Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains two domain controllers. The domain controllers are configured as shown in the following table.

You configure a user named User1 as a delegated administrator of DC10. You need to ensure that
User1 can log on to DC10 if the network link between the Main site and the Branch site fails.
What should you do?
A. On DC10, modify the User Rights Assignment in Local Policies
B. Add User1 to the Domain Admins group.
C. On DC10, run ntdsutil and configure the settings in the Roles context.
D. Run repadmin and specify /prp parameter.
ANSWER: D. Run repadmin and specify /prp parameter.
Q63. Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains two domain controllers. The domain controllers are configured as shown in the following table.

You configure a user named User1 as a delegated administrator of DC10. You need to ensure that User1 can log on to DC10 if the network link between the Main site and the Branch site fails.
What should you do?
A. On DC10, run ntdsutil and configure the settings in the Roles context.
B. On DC10, run ntdsutil and configure the settings in the Local Roles context.
C. Modify the properties of the DC10 computer account.
D. Run repadmin and specify /replsingleobject parameter.
ANSWER: B. On DC10, run ntdsutil and configure the settings in the Local Roles context.
Q64. You have a server named DC2 that runs Windows Server 2012 R2. DC2 contains a DNS zone named adatum.com. The adatum.com zone is shown in the exhibit.
You need to configure DNS clients to perform DNSSEC validation for the adatum.com DNS domain. What should you configure?
A. The Network Location settings.
B. A Name Resolution Policy.
C. The DNS Client settings.
D. The Network Connection settings.
ANSWER: B. A Name Resolution Policy.
Q65. Your network contains an Active Directory forest named adatum.com. The forest contains a single domain. The domain contains four servers. The servers are configured as shown in the following table.
You need to update the schema to support a domain controller that will run Windows Server 2012 R2.
On which server should you run adprep.exe?
A. DC1
B. DC2
C. DC3
D. Server1
ANSWER: C. DC3. You can use adprep.exe on DCs running 64bit versions of Windows Server 2008 or Windows Server 2008 R2.
Q66. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Certificate Services server role installed and is configured as an enterprise certification authority (CA). You need to ensure that all of the users in the domain are issued a certificate that can be used for the following purposes:
- Email security
- Client authentication
- Encrypting File System (EFS)
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From a Group Policy, configure the Certificate Services Client Auto-Enrollment settings.
B. From a Group Policy, configure the Certificate Services Client Certificate Enrollment Policy settings.
C. Modify the properties of the User certificate template, and then publish the template.
D. Duplicate the User certificate template, and then publish the template.
E. From a Group Policy, configure the Automatic Certificate Request Settings settings.
ANSWER: AD. From a Group Policy, configure the Certificate Services Client Auto-Enrollment settings. Duplicate the User certificate template, and then publish the template.
Q67. Drag and Drop Question
Your network contains an Active Directory domain named adatum.com. The domain contains three servers. The servers are configured as shown in the following table.
Server1 is configured as shown in the exhibit. (Click the Exhibit button.)
Template1 contains custom cryptography settings that are required by the corporate security team.
On Server2, an administrator successfully installs a certificate based on Template1.
The administrator reports that Template1 is not listed in the Certificate Enrollment wizard on Server3, even after selecting the Show all templates check box.
You need to ensure that you can install a server authentication certificate on Server3. The certificate must comply with the cryptography requirements.
Which three actions should you perform in sequence?
To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
From Certificate Templates, click Duplicate Template
From Certificate Templates, modify the Compatibility settings of the template.
From Certificate Templates. modify the Request handling settings of the template.
Q68. Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Certificate Services server role installed and is configured as a standalone certification authority (CA).
You install a second server named Server2. You install the Online Responder role service on Server2.
You need to ensure that Server1 can issue an Online Certificate Status Protocol (OCSP) Response Signing certificate to Server2.
What should you run on Server1?
A. The certreq.exe command and specify the -policy parameter
B. The certutil.exe command and specify the -getkey parameter
C. The certutil.exe command and specify the -setreg parameter
D. The certreq.exe command and specify the -retrieve parameter
ANSWER: C. The certutil.exe command and specify the -setreg parameter
Q69. Your network contains an Active Directory domain named contoso.com. The domain contains three servers named Server1, Server2, and Server3 that run Windows Server 2012 R2. All three servers have the Hyper-V server role installed and the Failover Clustering feature installed. Server1 and Server2 are nodes in a failover cluster named Cluster1. Several highly available virtual machines run on Cluster1. Cluster1 has the Hyper-V Replica Broker role installed. The Hyper-V Replica Broker currently runs on Server1. Server3 currently has no virtual machines.
You need to configure Cluster1 to be a replica server for Server3 and Server3 to be a replica server for Cluster1. Which two tools should you use? (Each correct answer presents part of the solution. Choose two.)
A. The Hyper-V Manager console connected to Server1
B. The Hyper-V Manager console connected to Server2
C. The Hyper-V Manager console connected to Server3
D. The Failover Cluster Manager console connected to Cluster1
E. The Failover Cluster Manager console connected to Server3
ANSWER: CD. The Hyper-V Manager console connected to Server3. The Failover Cluster Manager console connected to Cluster1
Q70. You have a server named Server1 that runs a Server Core Installation of Windows Server 2012 R2. Shadows copies are enabled on all volumes.
You need to delete a specific shadow copy. The solution must minimize server downtime.
Which tool should you use?
A. Vssadmin
B. Diskpart
C. Wbadmin
D. Shadow
ANSWER: A. Vssadmin (Vssadmin delete shadows)
Q71. You have a server named Server1 that runs a Server Core Installation of Windows Server 2012 R2. Shadows copies are enabled on all volumes.
You need to delete a specific shadow copy. The solution must minimize server downtime.
Which tool should you use?
A. Diskshadow
B. Diskpart
C. Wbadmin
D. Shadow
ANSWER: A. Diskshadow (Diskshadow delete Shadows)
Q72. Your network contains an Active Directory domain named contoso.com. The domain contains a file server named File1 that runs a Server Core Installation of Windows Server 2012 R2. File1 has a volume named D that contains home folders. File1 creates a shadow copy of volume D twice a day.
You discover that volume D is almost full. You add a new volume named H to File1.
You need to ensure that the shadow copies of volume D are stored on volume H.
Which command should you run?
A. The Set-Volume cmdlet with the -driveletter parameter
B. The vssadmin.exe create shadow command
C. The Set-Volume cmdlet with the -path parameter
D. The vssadmin.exe add shadowstorage command
ANSWER: D. The vssadmin.exe add shadowstorage command
Server1 is backed up by using Windows Server Backup. The backup configuration is shown in the exhibit.
You discover that only the last copy of the backup is maintained. You need to ensure that multiple backup copies are maintained. What should you do?
A. Modify the backup destination.
B. Configure the Optimize Backup Performance settings.
C. Modify the Volume Shadow Copy Service (VSS) settings.
D. Modify the backup times.
ANSWER: A. Modify the backup destination.
Explanation: A, The destination in the exhibit shows a network share is used. If a network share is being used only the latest copy will be saved
Q74. Your network contains two servers that run Windows Server 2012 R2 named Server1 and Server2. Both servers have the File Server role service installed. On Server2, you create a share named Backups. From Windows Server Backup on Server1, you schedule a full backup to run every night. You set the backup destination to \\Server2 \Backups.
After several weeks, you discover that \\Server2\Backups only contains the last backup that completed on Server1. You need to ensure that multiple backups of Server1 are maintained. What should you do?
A. Modify the Volume Shadow Copy Service (VSS) settings.
B. Modify the properties of the Windows Store Service (WSService) service.
C. Change the backup destination.
D. Configure the permission of the Backups share.
ANSWER: C. Change the backup destination
Q75. You have 30 servers that run Windows Server 2012 R2. All of the servers are backed up daily by using Windows Azure Online Backup.
You need to perform an immediate backup of all the servers to Windows Azure Online Backup.
Which Windows PowerShell cmdlets should you run on each server?
A. Get-OBPolicy | StartOBBackup
B. Start-OBRegistration | StartOBBackup
C. Get-WBPolicy | Start-WBBackup
D. Get-WBBackupTarget | Start-WBBackup
ANSWER: A. Get-OBPolicy | StartOBBackup
Q76. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DHCP Server server role installed.
You need to create an IPv6 scope on Server1. The scope must use an address space that is reserved for private networks. The addresses must be routable.
Which IPV6 scope prefix should you use?
A. 2001:123:4567:890A::
B. FE80:123:4567::
C. FF00:123:4567:890A::
D. FD00:123:4567::
ANSWER: D. FD00:123:4567::
Q77. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DHCP Server server role installed. Server1 has an IPv6 scope named Scope1.
You implement an additional DHCP server named Server2 that runs Windows Server 2012 R2.
You need to provide high availability for Scope1. The solution must minimize administrative effort.
What should you do?
A. Install and configure Network Load Balancing (NLB) on Server1 and Server2.
B. Create a scope on Server2.
C. Configure DHCP failover on Server1.
D. Install and configure Failover Clustering on Server1 and Server2.
ANSWER: B. Create a scope on Server2.
Q78. Your network contains a perimeter network and an internal network. The internal network contains an Active Directory Federation Services (AD FS) 2.1 infrastructure. The infrastructure uses Active Directory as the attribute store.
You plan to deploy a federation server proxy to a server named Server2 in the perimeter network. You need to identify which value must be included in the certificate that is deployed to Server2. What should you identify?
A. The FQDN of the AD FS server
B. The name of the Federation Service
C. The name of the Active Directory domain
D. The public IP address of Server2
ANSWER: A. The FQDN of the AD FS server
Q79. You have a server named Server1 that runs Windows Server 2012 R2. Server1 has a single volume that is encrypted by using BitLocker Drive Encryption (BitLocker). BitLocker is configured to save encryption keys to a Trusted Platform Module (TPM). Server1 is configured to perform a daily system image backup. The motherboard on Server1 is upgraded.
After the upgrade, Windows Server 2012 R2 on Server1 fails to start.
You need to start the operating system on Server1 as soon as possible. What should you do?
A. Start Server1 from the installation media. Run startrec.exe.
B. Move the disk to a server that has a model of the old motherboard. Start the server from the installation media. Run bcdboot.exe.
C. Move the disk to a server that has a model of the old motherboard. Start the server. Run tpm.msc.
D. Start Server1 from the installation media. Perform a system image recovery.
ANSWER: D. Start Server1 from the installation media. Perform a system image recovery.
Q80. Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. Both servers have the Hyper-V server role installed. You plan to replicate virtual machines between Server1 and Server2. The replication will be encrypted by using Secure Sockets Layer (SSL). You need to request a certificate on Server1 to ensure that the virtual machine replication is encrypted. Which two intended purposes should the certificate for Server1 contain? (Each correct answer presents part of the solution. Choose two.)
A. Client Authentication
B. Kernel Mode Code Signing
C. Server Authentication
D. IP Security end system
E. KDC Authentication
ANSWER: AC. Client Authentication + Server Authentication
Q81. You create a new virtual disk in a storage pool by using the New Virtual Disk Wizard. You discover that the new virtual disk has a write-back cache of 1 GB.
You need to ensure that the virtual disk has a write-back cache of 5 GB.
What should you do?
A. Detach the virtual disk, and then run the Resize-VirtualDisk cmdlet.
B. Detach the virtual disk, and then run the Set-VirtualDisk cmdlet.
C. Delete the virtual disk, and then run the New-StorageSubSystemVirtualDisk cmdlet.
D. Delete the virtual disk, and then run the New-VirtualDisk cmdlet.
ANSWER: D. Delete the virtual disk, and then run the New-VirtualDisk cmdlet.
Q82. You have a server named Server1 that runs Windows Server 2012 R2 and is used for testing. A developer at your company creates and installs an unsigned kernel-mode driver on Server1. The developer reports that Server1 will no longer start. You need to ensure that the developer can test the new driver. The solution must minimize the amount of data loss. Which Advanced Boot Option should you select?
A. Disable Driver Signature Enforcement
B. Disable automatic restart on system failure
C. Last Know Good Configuration (advanced)
D. Repair Your Computer
ANSWER: A. Disable Driver Signature Enforcement
Q83. Your network contains an Active Directory forest named contoso.com.
Users frequently access the website of an external partner company. The URL of the website is http://partners.adatum.com.
The partner company informs you that it will perform maintenance on its Web server and that the IP addresses of the Web server will change.
After the change is complete, the users on your internal network report that they fail to access the website. However, some users who work from home report that they can access the website.
You need to ensure that your DNS servers can resolve partners.adatum.com to the correct IP address immediately.
What should you do?
A. Run dnscmd and specify the CacheLockingPercent parameter.
B. Run Set-DnsServerGlobalQueryBlockList.
C. Run ipconfig and specify the Renew parameter.
D. Run Set-DnsServerCache.
ANSWER: D. Run Set-DnsServerCache (with the -LockingPercent switch).
Q84. You have a server named LON-DC1 that runs Windows Server 2012 R2. An iSCSI virtual disk named VirtualiSCSIl.vhd exists on LON-DC1 as shown in the exhibit. (Click the Exhibit button.)
You create a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt iSCSI target. VirtualiSCSI1.vhd is removed from LON-DC1.
You need to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
A. Modify the properties of the itgt ISCSI target.
B. Modify the properties of the VirttualiSCSI2.vhd iSCSI virtual disk.
C. Run the Set-VirtualDisk cmdlet and specify the -UniqueId parameter.
D. Run the iscsicli command and specify the reportluns parameter.
ANSWER: B. Modify the properties of the VirttualiSCSI2.vhd iSCSI virtual disk. Virtual disk has the option to change the lunID, no other option available in the answers appear to allow this change.
Q85. You have a server named LON-DC1 that runs Windows Server 2012 R2. An iSCSI virtual disk named VirtualiSCSIl.vhd exists on LON-DC1 as shown in the exhibit. (Click the Exhibit button.)
You create a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt iSCSI target. VirtualiSCSI1.vhd is removed from LON-DC1.
You need to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
A. Run the Set-IscsiVirtualDisk cmdlet and specify the -DevicePath parameter.
B. Run the iscsicpl command and specify the virtualdisklun parameter.
C. Modify the properties of the itgt ISCSI target.
D. Run the Set-VirtualDisk cmdlet and specify the -Uniqueld parameter.
ANSWER: D. Run the Set-VirtualDisk cmdlet and specify the -UniqueId parameter.
Explanation: Set-VirtualDisk Modifies the attributes of an existing virtual disk.
Applies To: Windows Server 2012 R2
-UniqueId<String> Specifies an ID used to uniquely identify a Disk object in the system. The ID persists through restarts.
Q86. You have a server named LON-DC1 that runs Windows Server 2012 R2. An iSCSI virtual disk named VirtualiSCSI1.vhd exists on LON-DC1 as shown in the exhibit. (Click the Exhibit button.)
You create a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt target.
VirtualiSCSI1.vhd is removed from LON-DC1.
You need to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
VirtualiSCSI1.vhd is removed from LON-DC1.
You need to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
A. Modify the properties of the VirtualiSCSI2.vhd iSCSI virtual disk.
B. Run the Set-VirtualDisk cmdlet and specify the -UniqueId parameter.
C. Run the iscsicli command and specify the reportluns parameter.
D. Modify the properties of the itgt ISCSI target.
ANSWER: A. Modify the properties of the VirtualiSCSI2.vhd iSCSI virtual disk.
Explanation: The virtual disk has the option to change the lun ID, no other option available in the answers appear to allow this change.
Explanation: The virtual disk has the option to change the lun ID, no other option available in the answers appear to allow this change.
Q87. You have a server named LON-DC1 that runs Windows Server 2012 R2. An iSCSI virtual disk named VirtualiSCSI1.vhd exists on LON-DC1 as shown in the exhibit. (Click the Exhibit button.)

You create a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt iSCSI target.
VirtualiSCSI1.vhd is removed from LON-DC1.
You need to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
A. Modify the properties of the VirtualiSCSI2.vhd iSCSI virtual disk.
B. Run the Add-IscsiVirtualDiskTargetMapping cmdlet and specify the -Lun parameter.
C. Run the iscsicli command and specify the reportluns parameter.
D. Run the iscsicpl command and specify the virtualdisklun parameter.
ANSWER: B. Run the Add-IscsiVirtualDiskTargetMapping cmdlet and specify the -Lun parameter.
Q88. You have a server named LON-DC1 that runs Windows Server 2012 R2. An iSCSI virtual disk named VirtualiSCSI1.vhd exists on LON-DC1 as shown in the exhibit. (Click the Exhibit button.)

You create a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt iSCSI target. VirtuahSCSI1.vhd is removed from LON-DC1. You need to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
A. Run the Set-IscsiVirtualDisk cmdlet and specify the -DevicePath parameter.
B. Run the iscsicpl command and specify the virtualdisklun parameter.
C. Modify the properties of the itgt ISCSI target.
D. Run the Set-VirtualDisk cmdlet and specify the -Uniqueld parameter.
ANSWER: D. Run the Set-VirtualDisk cmdlet and specify the -Uniqueld parameter.
Q89. Your network contains an Active Directory forest named contoso.com. The forest contains three domains. All domain controllers run Windows Server 2012 R2. The forest has a two-way realm trust to a Kerberos realm named adatum.com. You discover that users in adatum.com can only access resources in the root domain of contoso.com.
You need to ensure that the adatum.com users can access the resources in all of the domains in the forest.
What should you do in the forest?
What should you do in the forest?
A. Delete the realm trust and create a forest trust.
B. Delete the realm trust and create three external trusts.
C. Modify the incoming realm trust.
D. Modify the outgoing realm trust.
ANSWER: D. Modify the outgoing realm trust.
Q90. Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server1 that has the Active Directory Federation Services server role installed. All servers run Windows Server 2012.d
You complete the Active Directory Federation Services Configuration Wizard on Server1.
You need to ensure that client devices on the internal network can use Workplace Join.
Which two actions should you perform on Server1? (Each correct answer presents part of the solution. Choose two.)
A. Run Enable-AdfsDeviceRegistration -PrepareActiveDirectory.
B. Edit the multi-factor authentication global authentication policy settings.
C. Run Enable-AdfsDeviceRegistration.
D. Run Set-AdfsProxyProperties HttpPort 80.
E. Edit the primary authentication global authentication policy settings.
ANSWER: CE. Run Enable-AdfsDeviceRegistration. Edit the primary authentication global authentication policy settings.
Q91. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
You plan to install the Active Directory Federation Services server role on Server1 to allow for Workplace Join.
You run nslookup enterprise registration and you receive the following results:
You need to create a certificate request for Server1 to support the Active Directory Federation Services (AD FS) installation.
How should you configure the certificate request?
To answer, drag the appropriate names to the correct locations. Each name may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Q92. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
You need to ensure that third-party devices can use Workplace Join to access domain resources on the Internet.
Which four actions should you perform in sequence?
To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
Install a certificate obtained from a trusted third-party certification authority (CA)
Install and configure Active Directory Federation Services (AD FS)
Enable the Device Registration Service.
Install and configure a Web Application Proxy.
Q91. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
You plan to install the Active Directory Federation Services server role on Server1 to allow for Workplace Join.
You run nslookup enterprise registration and you receive the following results:
You need to create a certificate request for Server1 to support the Active Directory Federation Services (AD FS) installation.
How should you configure the certificate request?
To answer, drag the appropriate names to the correct locations. Each name may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Subject Name (CN): Adfs1.contoso.com
Subject Alternative Name (DNS): Adfs1.contoso.com
Subject Alternative Name(DNS): Enterpriseregistration.contoso.com
Q92. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
You need to ensure that third-party devices can use Workplace Join to access domain resources on the Internet.
Which four actions should you perform in sequence?
To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
Install a certificate obtained from a trusted third-party certification authority (CA)
Install and configure Active Directory Federation Services (AD FS)
Enable the Device Registration Service.
Install and configure a Web Application Proxy.
Q93. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
You plan to install the Active Directory Federation Services server role on Server1 to allow for Workplace Join.
You run nslookup enterprise registration and you receive the following results:
![clip_image001[16]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00116_thumb.jpg)
You need to create a certificate request for Server1 to support the Active Directory Federation Services (AD FS) installation.
How should you configure the certificate request?
To answer, drag the appropriate names to the correct locations. Each name may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
![clip_image002[25]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00225_thumb.jpg)
ANSWER:
Subject Name (CN): Adfs1.contoso.com
Subject Alternative Name (DNS): Adfs1.contoso.com
Subject Alternative Name (DNS): Enterpriseregistration.contoso.com
![clip_image002[27]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00227_thumb.jpg)
Q94. Your network contains an Active Directory domain named contoso.com. The domain contains an enterprise certification authority (CA). The domain contains a server named Server1 that runs Windows Server 2012 R2. You install the Active Directory Federation Services server role on Server1. You plan to configure Server1 as an Active Directory Federation Services (AD FS) server. The Federation Service name will be set to adfs1.contoso.com. You need to identify which type of certificate template you must use to request a certificate for AD FS.
ANSWER:
Web Server
Q95. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Federation Services (AD FS) server role installed. Adatum.com is a partner organization. You are helping the administrator of adatum.com set up a federated trust between adatum.com and contoso.com.
The administrator of adatum.com asks you to provide a file containing the federation metadata of contoso.com. You need to identify the location of the federation metadata file. Which node in the AD FS console should you select?
To answer, select the appropriate node in the answer area.
ANSWER:
Endpoints
Q96. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Rights Management Services server role installed. Your company works with a partner organization that does not have its own Active Directory Rights Management Services (AD RMS) implementation. You need to create a trust policy for the partner organization.
The solution must meet the following requirements:
- Grant users in the partner organization access to protected content.
- Provide users in the partner organization with the ability to create protected content.
Which type of trust policy should you create?
A. A federated trust
B. Windows Live ID
C. A trusted publishing domain
D. A trusted user domain
ANSWER: A. A federated trust
Q97. Your network contains an Active Directory domain named contoso.com. The domain contains a certification authority (CA).
You suspect that a certificate issued to a Web server is compromised.
You need to minimize the likelihood that users will trust the compromised certificate.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. Stop the Certificate Propagation service.
B. Modify the validity period of the Web Server certificate template.
C. Run certutil and specify the -revoke parameter.
D. Run certutil and specify the -deny parameter.
E. Publish the certificate revocation list (CRL).
ANSWER: CE. Run certutil and specify the -revoke parameter + Publish the certificate revocation list (CRL).
Explanation: First revoke the certificate, then publish the CRL.
Q98. Hotspot Question
Your company has a primary data center and a disaster recovery data center. The network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 runs Windows Server 2012 R2. Server1 is located in the primary data center. Server1 has an enterprise root certification authority (CA) for contoso.com.
You deploy another server named Server2 to the disaster recovery data center.
You plan to configure Server2 as a secondary certificate revocation list (CRL) distribution point.
You need to configure Server2 as a CRL distribution point (CDP).
Which tab should you use to configure the required CDP entry? To answer, select the appropriate tab in the answer area.
ANSWER:
Extensions
Q99. Drag and Drop Question
Your network contains two Active Directory forests named contoso.com and adatum.com. All domain controllers run Windows Server 2012 R2. A federated trust exists between adatum.com and contoso.com. The trust provides adatum.com users with access to contoso.com resources.
You need to configure Active Directory Federation Services (AD FS) claim rules for the federated trust. The solution must meet the following requirements:
- In contoso.com, replace an incoming claim type named Group with an outgoing claim type named Role.
- In adatum.com, allow users to receive their tokens for the relying party by using their Active Directory group membership as the claim type.
The AD FS claim rules must use predefined templates.
Which rule types should you configure on each side of the federated trust?
To answer, drag the appropriate rule types to the correct location or locations. Each rule type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Claims provider trust: An acceptance TRANSFORM rule
Relaying Party trust: An issuance AUTHORIZATION rule
Q100. Your network contains an Active Directory forest named adatum.com. The forest contains an Active Directory Rights Management Services (AD RMS) cluster.
A partner company has an Active Directory forest named litwareinc.com. The partner company does not have AD RMS deployed.
You need to ensure that users in litwareinc.com can consume rights-protected content from adatum.com.
Which type of trust policy should you create?
A. A federated trust
B. A trusted user domain
C. A trusted publishing domain
D. Windows Live ID
ANSWER: A. A federated trust
Explanation: A. In AD RMS rights can be assigned to users who have a federated trust with Active Directory Federation Services (AD FS). This enables an organization to share access to rights-protected content with another organization without having to establish a separate Active Directory trust or Active Directory Rights Management Services (AD RMS) infrastructure.
ANSWER:
Web Server
Q95. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Federation Services (AD FS) server role installed. Adatum.com is a partner organization. You are helping the administrator of adatum.com set up a federated trust between adatum.com and contoso.com.
The administrator of adatum.com asks you to provide a file containing the federation metadata of contoso.com. You need to identify the location of the federation metadata file. Which node in the AD FS console should you select?
To answer, select the appropriate node in the answer area.
ANSWER:
Endpoints
Q96. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Rights Management Services server role installed. Your company works with a partner organization that does not have its own Active Directory Rights Management Services (AD RMS) implementation. You need to create a trust policy for the partner organization.
The solution must meet the following requirements:
- Grant users in the partner organization access to protected content.
- Provide users in the partner organization with the ability to create protected content.
Which type of trust policy should you create?
A. A federated trust
B. Windows Live ID
C. A trusted publishing domain
D. A trusted user domain
ANSWER: A. A federated trust
Q97. Your network contains an Active Directory domain named contoso.com. The domain contains a certification authority (CA).
You suspect that a certificate issued to a Web server is compromised.
You need to minimize the likelihood that users will trust the compromised certificate.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. Stop the Certificate Propagation service.
B. Modify the validity period of the Web Server certificate template.
C. Run certutil and specify the -revoke parameter.
D. Run certutil and specify the -deny parameter.
E. Publish the certificate revocation list (CRL).
ANSWER: CE. Run certutil and specify the -revoke parameter + Publish the certificate revocation list (CRL).
Explanation: First revoke the certificate, then publish the CRL.
Q98. Hotspot Question
Your company has a primary data center and a disaster recovery data center. The network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 runs Windows Server 2012 R2. Server1 is located in the primary data center. Server1 has an enterprise root certification authority (CA) for contoso.com.
You deploy another server named Server2 to the disaster recovery data center.
You plan to configure Server2 as a secondary certificate revocation list (CRL) distribution point.
You need to configure Server2 as a CRL distribution point (CDP).
Which tab should you use to configure the required CDP entry? To answer, select the appropriate tab in the answer area.
ANSWER:
Extensions
Q99. Drag and Drop Question
Your network contains two Active Directory forests named contoso.com and adatum.com. All domain controllers run Windows Server 2012 R2. A federated trust exists between adatum.com and contoso.com. The trust provides adatum.com users with access to contoso.com resources.
You need to configure Active Directory Federation Services (AD FS) claim rules for the federated trust. The solution must meet the following requirements:
- In contoso.com, replace an incoming claim type named Group with an outgoing claim type named Role.
- In adatum.com, allow users to receive their tokens for the relying party by using their Active Directory group membership as the claim type.
The AD FS claim rules must use predefined templates.
Which rule types should you configure on each side of the federated trust?
To answer, drag the appropriate rule types to the correct location or locations. Each rule type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Claims provider trust: An acceptance TRANSFORM rule
Relaying Party trust: An issuance AUTHORIZATION rule
Q100. Your network contains an Active Directory forest named adatum.com. The forest contains an Active Directory Rights Management Services (AD RMS) cluster.
A partner company has an Active Directory forest named litwareinc.com. The partner company does not have AD RMS deployed.
You need to ensure that users in litwareinc.com can consume rights-protected content from adatum.com.
Which type of trust policy should you create?
A. A federated trust
B. A trusted user domain
C. A trusted publishing domain
D. Windows Live ID
ANSWER: A. A federated trust
Explanation: A. In AD RMS rights can be assigned to users who have a federated trust with Active Directory Federation Services (AD FS). This enables an organization to share access to rights-protected content with another organization without having to establish a separate Active Directory trust or Active Directory Rights Management Services (AD RMS) infrastructure.
Q101. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012.
Server1 is the enterprise root certification authority (CA) for contoso.com.
You need to enable CA role separation on Server1.
Which tool should you use?
A. The Certutil command
B. The Authorization Manager console
C. The Certsrv command
D. The Certificates snap-in
ANSWER: A. The Certutil command
Server1 is the enterprise root certification authority (CA) for contoso.com.
You need to enable CA role separation on Server1.
Which tool should you use?
A. The Certutil command
B. The Authorization Manager console
C. The Certsrv command
D. The Certificates snap-in
ANSWER: A. The Certutil command
Q102. Your network contains an Active directory forest named contoso.com. The forest contains two child domains named east.contoso.com and west.contoso.com. You install an Active Directory Rights Management Services (AD RMS) cluster in each child domain.
You discover that all of the users in the contoso.com forest are directed to the AD RMS cluster in east.contoso.com.
You need to ensure that the users in west.contoso.com are directed to the AD RMS cluster in west.contoso.com and that the users in east.contoso.com are directed to the AD RMS cluster in east.contoso.com. What should you do?
A. Modify the Service Connection Point (SCP).
B. Configure the Group Policy object (GPO) settings of the users in the west.contoso.com domain.
C. Configure the Group Policy object (GPO) settings of the users in the east.contoso.com domain.
D. Modify the properties of the AD RMS cluster in west.contoso.com.
ANSWER: B Configure the Group Policy object (GPO) settings of the users in the west.contoso.com domain.
Q103. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server2 that runs Windows Server 2012 R2. You are a member of the local Administrators group on Server2. You install an Active Directory Rights Management Services (AD RMS) root cluster on Server2. You need to ensure that the AD RMS cluster is discoverable automatically by the AD RMS client computers and the users in contoso.com. Which additional configuration settings should you configure?
To answer, select the appropriate tab in the answer area.
ANSWER:
SCP
To answer, select the appropriate tab in the answer area.
ANSWER:
SCP
Q104. Your network contains an Active Directory domain named corp.contoso.com. You deploy Active Directory Rights Management Services (AD RMS). You have a rights policy template named Template1. Revocation is disabled for the template. A user named User1 can open content that is protected by Template1 while the user is connected to the corporate network. When User1 is disconnected from the corporate network, the user cannot open the protected content even
if the user previously opened the content. You need to ensure that the content protected by Template1 can be opened by users who are disconnected from the corporate network. What should you modify?
A. The User Rights settings of Template1
B. The templates file location of the AD RMS cluster
C. The Extended Policy settings of Template1
D. The exclusion policies of the AD RMS cluster
ANSWER: C. The Extended Policy settings of Template1
Explanation:
C. You can add trust policies so that AD RMS can process licensing requests for content that was rights protected
http://technet.microsoft.com/en-us/library/ee221071(v=ws.10).aspx
Q105. Drag and Drop Question
Your network contains two Active Directory forests named contoso.com and adatum.com. Each forest contains an Active Directory Rights Management Services (AD RMS) root cluster. All servers run Windows Server 2012 R2.
You need to ensure that the rights account certificates issued in adatum.com are accepted by the AD RMS root cluster in contoso.com.
What should you do in each forest?
To answer, drag the appropriate actions to the correct forests. Each action may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Adatum.com: Export the SERVER licensor certificate.
Contoso.com: Add a trusted user domain.
Q106. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DNS Server server role installed. Server1 has a zone named contoso.com. The zone is configured as shown in the exhibit. (Click the Exhibit button.)
You need to assign a user named User1 permission to add and delete records from the contoso.com zone only. What should you do first?
A. Enable the Advanced view from DNS Manager.
B. Add User1 to the DnsUpdateProxy group.
C. Run the New Delegation Wizard.
D. Configure the zone to be Active Directory-integrated.
ANSWER: D. Configure the zone to be Active Directory-integrated.
Q107. You have a virtual machine named VM1 that runs on a host named Host1.
You configure VM1 to replicate to another host named Host2. Host2 is located in the same physical location as Host1.
You need to add an additional replica of VM1. The replica will be located in a different physical site.
What should you do?
A. From VM1 on Host2, click Extend Replication.
B. On Host1, configure the Hyper-V settings.
C. From VM1 on Host1, click Extend Replication.
D. On Host2, configure the Hyper-V settings.
ANSWER: A. From VM1 on Host2, click Extend Replication.
Q108. You have a server named Server1 that runs Windows Server 2012 R2. The storage on Server1 is configured as shown in the following table.
You plan to implement Data Deduplication on Server1. You need to identify on which drives you can enable Data Deduplication. Which three drives should you identify? (Each correct answer presents part of the solution. Choose three.)
A. Drive C
B. Drive D
C. Drive E
D. Drive F
E. Drive G
B. Drive D
C. Drive E
D. Drive F
E. Drive G
ANSWER: BDE.
Explanation: Volumes that are candidates for deduplication must conform to the following requirements:
* (not A) Must NOT be a system or boot volume. Deduplication is not supported on operating system volumes.
* Can be partitioned as a master boot record (MBR) or a GUID Partition Table (GPT), and must be formatted using the NTFS file system.
* Can reside on shared storage, such as storage that uses a Fibre Channel or an SAS array, or when an iSCSI SAN and Windows Failover Clustering is fully supported.
* Do not rely on Cluster Shared Volumes (CSVs). You can access data if a deduplicationenabled volume is converted to a CSV, but you cannot continue to process files for deduplication.
* (not C) Do not rely on the Microsoft Resilient File System (ReFS).
* Must be exposed to the operating system as non-removable drives. Remotely-mapped drives are not supported.
Q109. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a
failover cluster named Cluster1. Cluster1 has access to four physical disks. The disks are configured as shown in the following table.
![clip_image001[14]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00114_thumb.jpg)
You need to ensure that all of the disks can be added to a Cluster Shared Volume (CSV). Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Enable BitLocker on Disk4.
B. Format Disk2 to use NTFS.
C. Format Disk3 to use NTFS.
D. Disable BitLocker on Disk1.
ANSWER: BC
Explanation: You cannot use a disk for a CSV that is formatted with FAT, FAT32, or Resilient File System (ReFS)
Q110. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server3 that runs Windows Server 2012 R2 and has the DHCP Server server role installed. DHCP is configured as shown in the exhibit.
You need to ensure that only Scope1, Scope3, and Scope5 assign the same DNS servers to DHCP clients. The solution must minimize administrative effort.
What should you do?
A. Create a superscope and scope-level policies.
B. Configure the Scope Options.
C. Create a superscope and a filter.
D. Configure the Server Options.
ANSWER: B. Configure the Scope Options.
Scope1, Scope2, and Scope3 are configured to assign the IP addresses of two DNS servers to DHCP clients. The remaining scopes are NOT configured to assign IP addresses of DNS servers to DHCP clients.
You need to ensure that only Scope1, Scope3, and Scope5 assign the IP addresses of the DNS servers to DHCP clients. The solution must minimize administrative effort.
What should you do?
A. Create a superscope and scope-level policies.
B. Configure the Scope Options.
C. Create a superscope and a filter.
D. Configure the Server Options.
ANSWER: B. Configure the Scope Options.
Q112. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. The system properties of Server1 are shown in the exhibit. (Click the Exhibit button.)
You need to configure Server1 as an enterprise subordinate certification authority (CA). What should you do first?
A. Add RAM to the server.
B. Set the Startup Type of the Certificate Propagation service to Automatic.
C. Install the Certification Authority Web Enrollment role service.
D. Join Server1 to the contoso.com domain.
ANSWER: D. Join Server1 to the contoso.com domain.
Q113. You have a server named Server1 that runs Windows Server 2012 R2.
From Server Manager, you install the Active Directory Certificate Services server role on Server1.
A domain administrator named Admin1 logs on to Server1.
When Admin1 runs the Certification Authority console, Admin1 receive the following error message.
You need to ensure that when Admin1 opens the Certification Authority console on Server1, the error message does not appear. What should you do?
A. Install the Active Directory Certificate Services (AD CS) tools.
B. Run the regsvr32.exe command.
C. Modify the PATH system variable.
D. Configure the Active Directory Certificate Services server role from Server Manager.
ANSWER: D. Configure the Active Directory Certificate Services server role from Server Manager.
Explanation: Error message related to missing role configuration.
Explanation: Error message related to missing role configuration.
Q114. You have a server named Server1 that runs Windows Server 2012 R2.
From Server Manager, you install the Active Directory Certificate Services server role on Server1.
A domain administrator named Admin1 logs on to Server1.
When Admin1 runs the Certification Authority console, Admin1 receive the following error message.
You need to ensure that when Admin1 opens the Certification Authority console on Server1, the error message does not appear. What should you do?
A. Add Admin1 to the Cert Publishers group.
B. Install the Active Directory Certificate Services (AD CS) tools.
B. Install the Active Directory Certificate Services (AD CS) tools.
C. Run the Install-AdcsCertificationAuthority cmdlet.
D. Modify the PATH system variable.
ANSWER: C.Run the Install-AdcsCertificationAuthority cmdlet.
Q115. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs a Server Core installation of Windows Server 2012 R2.
You need to deploy a certification authority (CA) to Server1. The CA must support the auto- enrollment of certificates.
Which two cmdlets should you run? (Each correct answer presents part of the solution.
Choose two.)
A. Add-CAAuthoritylnformationAccess
B. Install-AdcsCertificationAuthority
C. Add-WindowsFeature
D. Install-AdcsOnlineResponder
E. Install-AdcsWebEnrollment
ANSWER:BE. Install-AdcsCertificationAuthority + Install-AdcsWebEnrollment
Q115. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs a Server Core installation of Windows Server 2012 R2.
You need to deploy a certification authority (CA) to Server1. The CA must support the auto- enrollment of certificates.
Which two cmdlets should you run? (Each correct answer presents part of the solution.
Choose two.)
A. Add-CAAuthoritylnformationAccess
B. Install-AdcsCertificationAuthority
C. Add-WindowsFeature
D. Install-AdcsOnlineResponder
E. Install-AdcsWebEnrollment
ANSWER:BE. Install-AdcsCertificationAuthority + Install-AdcsWebEnrollment
Q116. Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Certificate Services server role installed and is configured as a standalone certification authority (CA). You install a second server named Server2. You install the Online Responder role service on Server2. You need to ensure that Server1 can issue an Online Certificate Status Protocol (OCSP) Response Signing certificate to Server2. What should you do?
A. On Server1, run the certutil.exe command and specify the -setreg parameter.
B. On Server2, run the certutil.exe command and specify the -policy parameter.
C. On Server1, configure Security for the OCSP Response Signing certificate template.
D. On Server2, configure Issuance Requirements for the OCSP Response Signing certificate template.
ANSWER: C. On Server1, configure Security for the OCSP Response Signing certificate template.
Q117. Your network contains an Active Directory domain named adatum.com. The domain contains a server named CA1 that runs Windows Server 2012 R2. CA1 has the Active Directory Certificate Services server role installed and is configured to support key archival and recovery. You need to ensure that a user named User1 can decrypt private keys archived in the Active Directory Certificate Services (AD CS) database. The solution must prevent User1 from retrieving the private keys from the AD CS database. What should you do?
A. Assign User1 the Issue and Manage Certificates permission to Server1.
B. Assign User1 the Read permission and the Write permission to all certificate templates.
C. Provide User1 with access to a Key Recovery Agent certificate and a private key.
D. Assign User1 the Manage CA permission to Server1.
ANSWER: C. Provide User1 with access to a Key Recovery Agent certificate and a private key.
Q118. Your network contains an Active Directory domain named adatum.com. The domain contains a server named CA1 that runs Windows Server 2012 R2. CA1 has the Active Directory Certificate Services server role installed and is configured to support key archival and recovery.
You create a new Active Directory group named Group1.
You need to ensure that the members of Group1 can request a Key Recovery Agent certificate. The solution must minimize the permissions assigned to Group1.
Which two permissions should you assign to Group1? (Each correct answer presents part of the solution. Choose two)
A. Enroll
B. Auto enroll
C. Read
D. Full control
E. Write
ANSWER: AC. Enroll + Read
Q119. You have a server named Server1 that has the Active Directory Certificate Services server role installed. Server1 uses a hardware security module (HSM) to protect the private key of Server1. You need to ensure that the Active Directory Certificate Services (AD CS) database, log files, and private key are backed up. You perform regular backups of the HSM module by using a backup utility provided by the HSM manufacturer.
What else should you do?
What else should you do?
A. Run the certutil.exe command and specify the -backupkey parameter.
B. Run the certutil.exe command and specify the -backupdb parameter.
C. Run the certutil.exe command and specify the -backup parameter.
D. Run the certutil.exe command and specify the -dump parameter.
ANSWER: B. Run the certutil.exe command and specify the -backupdb parameter.
Q120. Your company has offices in Montreal, New York, and Amsterdam. The network contains an Active Directory forest named contoso.com. An Active Directory site exists for each office. All of the sites connect to each other by using the DEFAULTIPSITELINK site link.
You need to ensure that only between 20:00 and 08:00, the domain controllers in the Montreal office replicate the Active Directory changes to the domain controllers in the Amsterdam office. The solution must ensure that the domain controllers in the Montreal and the New York offices can replicate the Active Directory changes any time of day.
What should you do?
You need to ensure that only between 20:00 and 08:00, the domain controllers in the Montreal office replicate the Active Directory changes to the domain controllers in the Amsterdam office. The solution must ensure that the domain controllers in the Montreal and the New York offices can replicate the Active Directory changes any time of day.
What should you do?
A. Create a new site link that contains Montreal and Amsterdam. Remove Amsterdam from DEFAULTIPSITELINK. Modify the schedule of DEFAULTIPSITELINK.
B. Create a new site link that contains Montreal and Amsterdam. Create a new site link bridge. Modify the schedule of DEFAULTIPSITELINK.
C. Create a new site link that contains Montreal and Amsterdam. Remove Amsterdam from DEFAULTIPSITELINK. Modify the schedule of the new site link.
D. Create a new site link that contains Montreal and Amsterdam. Create a new site link bridge. Modify the schedule of the new site link.
ANSWER: C. CREATE a new site link that contains Montreal and Amsterdam.
REMOVE Amsterdam from DEFAULTIPSITELINK.
MODIFY the schedule of the NEW site link.
Q121. Your company has offices in Montreal, New York, and Amsterdam. The network contains an Active Directory forest named contoso.com. An Active Directory site exists for each office. All of the sites connect to each other by using the DEFAULTIPSITELINK site link.
You need to ensure that only between 20:00 and 08:00, the domain controllers in the Montreal office replicate the Active Directory changes to the domain controllers in the Amsterdam office. The solution must ensure that the domain controllers in the Montreal and the New York offices can replicate the Active Directory changes any time of day.
What should you do FIRST?
You need to ensure that only between 20:00 and 08:00, the domain controllers in the Montreal office replicate the Active Directory changes to the domain controllers in the Amsterdam office. The solution must ensure that the domain controllers in the Montreal and the New York offices can replicate the Active Directory changes any time of day.
What should you do FIRST?
A. Create a new site link that contains Montreal and Amsterdam.
B. Create a new site link that contains Montreal and New York.
C. Delete Amsterdam from DEFAULTIPSITELINK.
D. Delete New York from DEFAULTIPSITELINK.
ANSWER: A. Create a new site link that contains Montreal and Amsterdam.
The forest contains two Active Directory sites named Main and Branch1. The sites connect to each other by using a site link named Main-Branch1. There are no other site links.
Each site contains several domain controllers. All domain controllers run Windows Server 2012 R2. Your company plans to open a new branch site named Branch2. The new site will have a WAN link that connects to the Main site only. The site will contain two domain controllers that run Windows Server 2012 R2.
You need to create a new site and a new site link for Branch2. The solution must ensure that the domain controllers in Branch2 only replicate to the domain controllers in Branch1 if all of the domain controllers in Main are unavailable.
Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
Create a new site object named Branch2
Remove Branch2 from the Main-Branch1 site link
Create a new site link object named Main-Branch2
Q123. Your network contains an Active Directory forest named contoso.com that contains a single domain. The forest contains three sites named Site1, Site2, and Site3. Domain controllers run either Windows Server 2008 R2 or Windows Server 2012 R2. Each site contains two domain controllers. Site1 and Site2 contain a global catalog server.
You need to create a new site link between Site1 and Site2. The solution must ensure that the site link supports the replication of all the naming contexts. From which node should you create the site link?
To answer, select the appropriate node in the answer area.
ANSWER:
(Inter-Site Transports =>) IP
Q124. Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The forest contains three Active Directory sites named SiteA, SiteB, and SiteC. The sites contain four domain controllers. The domain controllers are configured as shown in the following table.
An IP site link exits between each site.
You discover that the users in SiteC are authenticated by the domain controllers in SiteA and SiteB. You need to ensure that the SiteC users are authenticated by the domain controllers in SiteB, unless all of the domain controllers in SiteB are unavailable.
What should you do?
A. Create an SMTP site link between SiteB and SiteC.
B. Create additional connection objects for DC3 and DC4.
C. Decrease the cost of the site link between SiteB and SiteC.
D. Create additional connection objects for DC1 and DC2.
ANSWER: C. Decrease the cost of the site link between SiteB and SiteC.
Explanation: By decreasing the site link cost between SiteB and SiteC the SiteC users would be authenticated by SiteB rather than by SiteA.
Q125. You have a server named Server1 that runs Windows Server 2012 R2.
You start Server1 by using Windows PE.
You need to repair the Boot Configuration Data (BCD) store on Server1.
Which tool should you use?
A. Bootim
B. Bootsect
C. Bootrec
D. Bootcfg
ANSWER: C. Bootrec.
Q126. You have a server named Server1 that runs Windows Server 2012 R2.
When you install a custom Application on Server1 and restart the server, you receive the following error message: " The Boot Configuration Data file is missing some required information. File: \Boot\BCD\ Error code: 0x0000034"
You start Server1 by using Windows PE.
You need to repair the Boot Configuration Data (BCD) store on Server1.
Which tool should you use?
A. Bootim
B. Bootsect
C. Bootrec
D. Bootcfg
ANSWER: C. Bootrec. Updates the master boot code for hard disk partitions to switch between BOOTMGR and NTLDR. Replaces FixFat and FixNTFS
Q127?. You have a server named Server1 that runs Windows Server 2012 R2.
Server1 fails.
You identify that the master boot record (MBR) is corrupt.
You need to repair the MBR.
You need to repair the MBR.
Which tool should you use?
A. Fixmbr
B. Bcdboot
C. Bootrec
D. Bcdedit
ANSWER: C. Bootrec.
Q127. You have a test server named Server1 that is configured to dual-boot between Windows Server 2008 R2 and Windows Server 2012 R2. You start Server1 and you discover that the boot entry for Windows Server 2008 R2 no longer appears on the boot menu. You start Windows Server 2012 R2 on Server1 and you discover the disk configurations shown in the following table.
![clip_image00124_thumb_thumb_thumb_th[2]_thumb_thumb_thumb](http://examgod.com/l2pimages/207d3e55dd09_F480/clip_image00124_thumb_thumb_thumb_th2_thumb_thumb_thumb_thumb.jpg)
You need to restore the Windows Server 2008 R2 boot entry on Server1. What should you do?
A. Run bcdedit.exe and specify the /createstore parameter.
B. Run bootrec.exe and specify the /scanos parameter.
C. Run bcdboot.exe d:\windows.
D. Run bootrec.exe and specify the /rebuildbcd parameter.
ANSWER: D. Run bootrec.exe and specify the /rebuildbcd parameter.
Q128. You have a server named Server1 that runs Windows Server 2012 R2. Windows Server 2012 R2 is installed on volume C. You need to ensure that Safe Mode with Command Prompt loads the next time Server1 restarts. Which tool should you use?
A. The Restart-Server cmdlet
B. The Bootcfg command
C. The Restart-Computer cmdlet
D. The Bcdedit command
ANSWER: D. The Bcdedit command
Q129. You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 contains a virtual machine named VM1 that runs Windows Server 2012 R2. You fail to start VM1 and you suspect that the boot files on VM1 are corrupt. On Server1, you attach the virtual hard disk (VHD) of VM1 and you assign the VHD a drive letter of F. You need to repair the corrupt boot files on VM1. What should you run?
A. bootrec.exe /rebuildbcd
B. bootrec.exe /scanos
C. bcdboot.exe f:\windows /s c:
D. bcdboot.exe c:\windows /s f:
ANSWER: D. bcdboot.exe c:\windows /s f:
Q130. Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 that runs Windows Server 2012 R2. All client computers run Windows 8. You need to configure a custom Access Denied message that will be displayed to users when they are denied access to folders or files on Server1.
What should you configure?
A. A classification property
B. The File Server Resource Manager Options
C. A file management task
D. A file screen template
ANSWER: B. The File Server Resource Manager Options
Q131. Your network contains an Active Directory domain named contoso.com. All file servers in the domain run Windows Server 2012 R2. The computer accounts of the file servers are in an organizational unit (OU) named OU1. A Group Policy object (GPO) named GPO1 is linked to OU1. You plan to modify the NTFS permissions for many folders on the file servers by using central access policies. You need to identify any users who will be denied access to resources that they can cu
rrently access once the new permissions are implemented. In which order should you Perform the five actions?
ANSWER:
Create a central access RULE
Create a central access POLICY
In GPO1, modify the Audit Central Access Policy Staging setting and configure the Central Access Policy settings.
Modify the Security settings of the shared folders on the file server.
Search for failure events in the security logs from the file servers.
Q132. Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You have a Dynamic Access Control policy named Policy1.
You create a new Central Access Rule named Rule1.
You need to add Rule1 to Policy1.
What command should you run?
To answer, select the appropriate options in the answer area.
ANSWER:
Add-AdCentralAccessPolicyMember Policy1 -Members Rule1
Q131. Hotspot Question
You have a file server named Server1 that runs Windows Server 2012 R2.
Server1 contains a file share that must be accessed by only a limited number of users.
You need to ensure that if an unauthorized user attempts to access the file share, a custom access-denied message appears, which contains a link to request access to the share. The message must not appear when the unauthorized user attempts to access other shares.
Which two nodes should you configure in File Server Resource Manager? To answer, select the appropriate two nodes in the answer area.
ANSWER:
File Server Resource Manager (Local)
Classification Properties
Q132. Your network contains two Active Directory forests named contoso.com and adatum.com. Each forest contains one domain. Contoso.com has a two-way forest trust to adatum.com. Selective authentication is enabled on the forest trust.
Contoso contains 10 servers that have the File Server role service installed. Users successfully access shared folders on the file servers by using permissions granted to the Authenticated Users group.
You migrate the file servers to adatum.com
Contoso users report that after the migration, they are unable to access shared forlders on the file servers.
You migrate the file servers to adatum.com
Contoso users report that after the migration, they are unable to access shared forlders on the file servers.
You need to ensure that the Contoso users can access the shared folders on the file servers.
What should you do?
A. Replace the existing forest trust with an external trust.
B. Run netdom and specify the /quarantine attribute.
C. Disable SID filtering on the existing forest trust.
D. Disable selective authentication on the existing forest trust.
ANSWER: C. Disable SID filtering on the existing forest trust.
Q134. Your network contains two Active Directory forests named contoso.com and adatum.com. Contoso.com contains one domain. Adatum.com contains a child domain named child.adatum.com. Contoso.com has a one-way forest trust to adatum.com. Selective authentication is enabled on the forest trust.
Several user accounts are migrated from child.adatum.com to adatum.com. Users report that after the migration, they fail to access resources in contoso.com. The users successfully accessed the resources in contoso.com before the accounts were migrated.
You need to ensure that the migrated users can access the resources in contoso.com.
What should you do?
A. Replace the existing forest trust with an external trust.
B. Run netdom and specify the /quarantine attribute.
C. Disable SID filtering on the existing forest trust.
D. Disable selective authentication on the existing forest trust.
ANSWER: C. Disable SID filtering on the existing forest trust.
Q135. Your network contains two Active Directory forests named contoso.com and litwareinc.com. A two- way forest trusts exists between the forest. Selective authentication is enabled on the trust.
The contoso.com forest contains a server named Server1.
You need to ensure that users in litwareinc.com can access resources on Server1.
What should you do?
A. Install Active Directory Rights Management Services on a domain controller in contoso.com.
B. Modify the permission on the Server1 computer account.
C. Install Active Directory Rights Management Services on a domain controller in litwareinc.com.
D. Configure SID filtering on the trust.
ANSWER: B. Modify the permission on the Server1 computer account.
Explanation:
Q136. Your network contains two Active Directory forests named contoso.com and adatum.com. All of the domain controllers in both of the forests run Windows Server 2012 R2. The adatum.com domain contains a file server named Servers. Adatum.com has a one-way forest trust to contoso.com. A contoso.com user name User10 attempts to access a shared folder on Servers and receives the error message shown in the exhibit. (Click the Exhibit button.)
You verify that the Authenticated Users group has Read permissions to the Data folder. You need to ensure that User10 can read the contents of the Data folder on Server5 in the adatum.com domain.
What should you do?
A. Grant the Other Organization group Read permissions to the Data folder.
B. Modify the list of logon workstations of the contoso\User10 user account.
C. Enable the Netlogon Service (NP-In) firewall rule on Server5.
D. Modify the permissions on the Server5 computer object in Active Directory.
ANSWER: D. Modify the permissions on the Server5 computer object in Active Directory.
Q137. You have a server named DNS1 that runs Windows Server 2012 R2.
You discover that the DNS resolution is slow when users try to access the company intranet home page by using the URL http://companyhome.
You need to provide single-label name resolution for CompanyHome that is not dependent on the suffix search order.
Which three cmdlets should you run? (Each correct answer presents part of the solution.
Choose three.)
A. Add-DnsServerPrimaryZone
B. Add-DnsServerResourceRecordCName
C. Set-DnsServerDsSetting
D. Set-DnsServerGlobalNameZone
E. Set-DnsServerEDns
F. Add-DnsServerDirectory Partition
ANSWER: ABD. Add-DnsServerPrimaryZone + Add-DnsServerResourceRecordCName + Set-DnsServerGlobalNameZone
Explanation:
*The Add-DnsServerPrimaryZone cmdlet adds a specified primary zone on a Domain Name System (DNS) server.
* The Add-DnsServerResourceRecordCName cmdlet adds a canonical name (CNAME) resource record to a specified Domain Name System (DNS) zone. A CNAME record allows you to use more than one resource record to refer to a single host *The Set-DnsServerGlobalNameZone cmdlet enables or disables single-label Domain Name System (DNS) queries.
It also changes configuration settings for a GlobalNames zone.
The GlobalNames zone supports short, easy-to-use names instead of fully qualified domain names (FQDNs) without using Windows Internet Name Service (WINS) technology. For instance, DNS can query SarahJonesDesktop instead of SarahJonesDesktop.contoso.com
Q138. You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the DNS Server server role installed. You need to configure Server1 to resolve queries for single-label DNS names. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Run the Set-DNSServerGlobalNameZone cmdlet.
B. Modify the DNS suffix search list setting.
C. Modify the Primary DNS Suffix Devolution setting.
D. Create a zone named “.”.
E. Create a zone named GlobalNames.
F. Run the Set-DNSServerRootHint cmdlet.
ANSWER: AE. Run the Set-DNSServerGlobalNameZone cmdlet + Create a zone named GlobalNames.
You have a server named Server1 that runs Windows Server 2012. Server1 has the DNS
Server server role installed. You need to configure Server1 to resolve queries for single-label DNS names. Which two actions should you perform? (Each correct answer presents
part of the solution. Choose two.)
A. Run the Set-DNSServerGlobalNameZone cmdlet.
B. Modify the DNS suffix search list setting.
C. Modify the Primary DNS Suffix Devolution setting.
D. Create a zone named “.”.
E. Create a zone named GlobalNames.
F. Run the Set-DNSServerRootHint cmdlet.
??Answer: B, D. Explanation: ipass4sure.com
Q139. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a DNS server named Server1. Server1 is configured to resolve single-label names for DNS clients.
You need to view the number of queries for single-label names that are resolved by Server1.
What command should you run? To answer, select the appropriate options in the answer area.
ANSWER:
Get-DnsServerStatistics -ZoneName GlobalNames
Q140. Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. Server1 is a BranchCache hosted cache server that is located in a branch office.
The network contains client computers that run either Windows 7 or Windows 8.
For the branch office, all of the user accounts and the client computer accounts are located in an organizational unit (OU) named Branch1. A group Policy object (GPO) named GPO1 is linked to Branch1. GPO1 contains the BranchCache settings.
You discover that users in the branch office who have client computers that run Windows 7 do not access cached content from Server1. Users in the branch office who have Windows 8 computers access cached content from Server1.
You need to confiure the Windows 7 computers to use BranchCache on Server1. Which setting should you configure in GPO1?
To answer, select the appropiate setting in the answer area.
ANSWER:
Set BranchCache Hosted Cache mode
Q141. Your network contains an Active Directory domain named contoso.com. All client computers run Windows 8 Enterprise.
You have a remote site that only contains client computers. All of the client computer accounts are located in an organizational unit (OU) named Remote1. A Group Policy object (GPO) named GPO1 is linked to the Remote1 OU.
You need to configure BranchCache for the remote site.
Which two settings should you configure in GPO1? To answer, select the appropiate setting in the answer area.
Q142. Your company has a main office and a branch office. The main office is located in Detroit. The branch office is located in Seattle.
The network contains an Active Directory domain named adatum.com. Client computers run eiter Windows 7 Enterprise or Windows 8 Enterprise.
The main office contains 1,000 client computers and 50 servers. The branch office contains 20 client computers.
All computer accounts are located in an organizational unit (OU) named SeattleComputers. A Group Policy object (GPO) named GPO1 is linked to the SeattleComputers OU.
You need to configure BranchCache for the remote site.
Which two settings should you configure in GPO1? To answer, select the appropiate setting in the answer area.
Q143. Your company has a main office and a branch office. An Active Directory site exists for each office.
The network contains an Active Directory forest named contoso.com. The contoso.com domain contains three member servers named Server1, Server2, and Server3. All servers run Windows Server 2012 R2.
In the main office, you configure Server1 as a file server that uses BranchCache.
In the branch office, you configure Server2 and Server3 as BranchCache hosted cache servers.
You are creating a Group Policy for the branch office site.
Which two Group Policy settings should you configure? To answer, select the appropriate two settings in the answer area.
ANSWER:
Turn on BranchCache
Set BranchCache Hosted Cache mode
Q144. Your company has a main office and a branch office. An Active Directory site exists for each office.
The network contains an Active Directory forest named contoso.com. The contoso.com domain contains three member servers named Server1, Server2, and Server3. All servers run Windows Server 2012 R2.
In the main office, you configure Server1 as a file server that uses BranchCache.
In the branch office, you configure Server2 and Server3 as BranchCache hosted cache servers.
You are creating a Group Policy for the branch office site. In the branch office, you need to configure the client computers that run Windows 8 to use Server2 and Server3 as BranchCache.
ANSWER:
Turn on BranchCache
Configure Hosted Cache Servers
![clip_image001[72]](http://examgod.com/l2pimages/f98e0646ba5b_79CB/clip_image00172_thumb.jpg)
Q145. You plan to deploy a failover cluster that will contain two nodes that run Windows Server 2012 R2. You need to configure a witness disk for the failover cluster. How should you configure the witness disk? To answer, drag the appropriate configurations to the correct location or locations. Each configuration may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Disk Type: Basic / File System: NTFS
Q146. Drag and Drop Question
You have two failover clusters named Cluster1 and Cluster2. All of the nodes in both of the clusters run Windows Server 2012 R2.
Cluster1 hosts two virtual machines named VM1 and VM2.
You plan to configure VM1 and VM2 as nodes in a new failover cluster named Cluster3.
You need to configure the witness disk for Cluster3 to be hosted on Cluster2.
Which three actions should you perform in sequence?
To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
On Cluster1, add an iSCSI hard disk drive to VM1 and VM2
On Cluster2, install the File Server role service
On Cluster2, install the Scale-Out File Server for application data (Scale-Out File Server) option.
Q147. Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. All servers run Windows Server 2012 R2. All domain user accounts have the Division attribute automatically populated as part of the user provisioning process. The Support for Dynamic Access Control and Kerberos armoring policy is enabled for the domain. You need to control access to the file shares on Server1 based on the values in the Division attribute and the Division resource property. Which three actions should you perform in sequence?
ANSWER:
From Active Directory Administrative Center, create a claim type
From Active Directory Administrative Center, create a reference resource property
On the Shared folders, set the classification value.
Q148. Hotspot Question
Your network contains an Active Directory forest.
You implement Dynamic Access Control in the forest.
You have the claim types shown in the Claim Types exhibit. (Click the Exhibit button.)
The properties of a user named User1 are configured as shown in the User1 exhibit. (Click the Exhibit button.)
The output of Whoami /claims for a user named User2 is shown in the Whoa mi exhibit.
(Click the Exhibit button.)
Select Yes if the statement can be shown to be true based on the available information; otherwise select No. Each correct selection is worth one point.
ANSWER:
The security token for User1 contains at least one claim - Yes
A value is set for the department attribute of User2 - No
The client computer of User2 supports Dynamic Access Control - Yes
Q149. Your network contains an Active Directory forest named contoso.com. The forest contains a single domain, The forest functional level is Windows Server 2012 R2. You have a domain controller named DC1.
On DC1, you create a new Group Policy object (GPO) named GPO1.
You need to verify that GPO1 was replicated to all of the domain controllers.
Which tool should you use?
A. Active Directory Administrative Center
B. Group Policy Management
C. DFS Management
D. Active Directory Sites and Services
E. Gpresult
ANSWER: B. Group Policy Management.
Q150. Your network contains an Active Directory domain named adatum.com. The domain contains two sites named Site1 and Site2 and two domain controllers named DC1 and DC2.DC1 is located in Site1 and DC2 is located in Site2.
You install an additional domain controller named DC3 in Site1 and you ship DC3 to Site2. A technician connects DC3 to Site2.
You discover that users in Site2 are authenticated only by DC2.
You need to ensure that the users in Site2 are authenticated by both DC2 and DC3.
What should you do?
A. In Active Directory Users and Computers, configure the msDS-PrimaryComputer attribute for DC3.
B. From Active Directory Sites and Services, modify the site link between Site1 and Site2.
C. From Active Directory Sites and Services, move DC3.
D. In Active Directory Users and Computers, configure the msDS-Site-Affinity attribute for DC3.
ANSWER: C. From Active Directory Sites and Services, move DC3.
Q151. Your network contains an Active Directory domain named contoso.com. The domain contains two sites named Site1 and Site2 and two domain controllers named DC1 and DC2. Both domain controllers are located in Site1.
You install an additional domain controller named DC3 in Site1 and you ship DC3 to Site2. A technician connects DC3 to Site2. You discover that users in Site2 are authenticated by all three domain controllers.
You need to ensure that the users in Site2 are authenticated by DC1 or DC2 only if DC3 is unavailable.
What should you do?
A. From Network Connections, modify the IP address of DC3.
B. In Active Directory Sites and Services, modify the Query Policy of DC3.
C. From Active Directory Sites and Services, move DC3.
D. In Active Directory Users and Computers, configure the msDS-PrimaryComputer attribute for the users in Site2.
ANSWER: C. From Active Directory Sites and Services, move DC3.
Q152. Your network contains an Active Directory domain named adatum.com. The domain contains two sites named Site1 and Site2 and two domain controllers named DC1 and DC2.DC1 is located in Site1 and DC2 is located in Site2. You install an additional domain controller named DC3 in Site1 and you ship DC3 to Site2. A technician connects DC3 to Site2.
You discover that users in Site2 are authenticated only by DC2.
You need to ensure that the users in Site2 are authenticated by both DC2 and DC3.
What should you do?
A. From Network Connections, modify the IP address of DC3.
B. In Active Directory Sites and Services, modify the Query Policy of DC3.
C. From Active Directory Sites and Services, move DC3.
D. In Active Directory Users and Computers, configure the msDS-PrimaryComputer attribute for the users in Site2.
ANSWER: C. From Active Directory Sites and Services, move DC3.
Q152. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 is an enterprise root certification authority (CA) for contoso.com.
You need to ensure that the members of a group named Group1 can request code signing
certificates. The certificates must be issued automatically to the members.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From Certificate Templates, modify the certificate template.
B. From Certification Authority, add a certificate template to be issued.
C. From Certificate Authority, modify the CA properties.
D. From Certificate Templates, duplicate a certificate template.
E. From Certificate Authority, stop and start the Active Directory Certificate Services (AD CS) service.
ANSWER: AB.
Explanation: First modify the certificate template in Certificate Templates, then add it in Certification Authority.
Q153. Your network contains two Active Directory forests named contoso.com and corp.contoso.com.
User1 is a member of the DnsAdmins domain local group in contoso.com.
User1 attempts to create a conditional forwarder to corp.contoso.com but receive an error message shown in the exhibit. (Click the Exhibit button.)

You need to configure bi-directional name resolution between the two forests.
What should you do first?
A. Add User1 to the DnsUpdateProxy group.
B. Configure the zone to be Active Directory-integrated.
C. Enable the Advanced view from DNS Manager.
D. Run the New Delegation Wizard.
ANSWER: B. Configure the zone to be Active Directory-integrated.
Q154. Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com. The functional level of the forest is Windows Server 2003. You have a domain outside the forest named adatum.com. You need to configure an access solution to meet the following requirements:
- Users in adatum.com must be able to access resources in contoso.com.
- Users in adatum.com must be prevented from accessing resources in fabrikam.com.
- Users in both contoso.com and fabrikam.com must be prevented from accessing resources in adatum.com.
What should you create?
A. a one-way external trust from contoso to adatum.com
B. a one-way realm trust from adatum.com to contoso.com
C. a one-way external trust from adatum.com to contoso.com
D. a one-way realm trust from contoso.com to adatum.com
ANSWER: A. a one-way EXTERNAL trust from contoso to adatum.com
Q155. Hotspot Question
Your network contains three Active Directory forests. The forests are configured as shown in the following table.
A two-way forest trust exists between contoso.com and division1.contoso.com. A two-way forest trust also exists between contoso.com and division2.contoso.com.
You plan to create a one-way forest trust from division1.contoso.com to division2.contoso.com.
You need to ensure that any cross-forest authentication requests are sent to the domain controllers in the appropriate forest after the trust is created.
How should you configure the existing forest trust settings?
In the table below, identify which configuration must be performed in each forest. Make only one selection in each column. Each correct selection is worth one point.
ANSWER:
Division2.contoso.com = Add division1.contoso.com as a name suffix routing entry
Division1.contoso.com = Add division2.contoso.com as an EXCLUSION to the name suffix routing entry of contoso.com
Q156. You have a server named FS1 that runs Windows Server 2012 R2.
You install the File and Storage Services server role on FS1.
From Windows Explorer, you view the properties of a shared folder named Share1 and you discover that the Classification tab is missing.
You need to ensure that you can assign classifications to Share1 from Windows Explorer manually.
What should you do?
A. From Folder Options, select Show hidden files, folders, and drives.
B. From Folder Options, clear Use Sharing Wizard (Recommend).
C. Install the File Server Resource Manager role service.
D. Install the Enhanced Storage feature.
ANSWER: C. Install the File Server Resource Manager role service.
Q157. You have a server named Server1 that runs Windows Server 2012 R2.
You install the File and Storage Services server role on Server1.
From Windows Explorer, you view the properties of a shared folder named Folder1 and you discover that the Classification tab is missing.
You need to ensure that you can assign classifications to Folder1 from Windows Explorer manually.
What should you do?
A. Install the Share and Storage Management tools.
B. From Folder Options, clear Hide protected operating system files (Recommended).
C. Install the File Server Resource Manager role service.
D. From Folder Options, señect the Always show menus.
ANSWER: C. Install the File Server Resource Manager role service.
Q158. Your network contains an Active Directory domain named adatum.com. The domain contains a file server named FS1 that runs Windows Server 2012 R2 and has the File Server Resource Manager role service installed. All client computers run Windows 8.
File classification and Access-Denied Assistance are enabled on FS1.
You need to ensure that if users receive an Access Denied message, they can request assistance by email from the Access Denied dialog box.
What should you configure?
A. A file management task.
B. The File Server Resource Manager Options
C. A report task
D. A classification property.
ANSWER: B. The File Server Resource Manager Options.
Q159. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 and a server named Server1. Both servers run Windows Server 2012 R2.
You configure the classification of a share on Server1 as shown in the Share1 Properties exhibit. (Click the Exhibit button.)
You configure the resource properties in Active Directory as shown in the Resource Properties exhibit. (Click the Exhibit button.)
You need to ensure that the Impact classification can be assigned to Share1 immediately.
Which cmdlet should you run on each server?
To answer, select the appropriate cmdlet for each server in the answer area.
ANSWER:
DC1: SET-AdResourceProperty
Server1: UPDATE-FsrmClassificationPropertyDefinition
Q160. You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource Manager role service installed. You attempt to delete a classification property and you receive the error message as shown in the exhibit. (Click the Exhibit button.)
You need to delete the is Confidential classification property.
What should you do?
A. Delete the classification rule that is assigned the isConfidential classification property.
B. Disable the classification rule that is assigned the isConfidential classification property.
C. Set files that have an isConfidential classification property value of Yes to No.
D. Clear the isConfidential classification property value of all files.
ANSWER: A. Delete the classification rule that is assigned the isConfidential classification property.
Q161. Hotspot Question
Your network contains two DHCP servers named Server1 and Server2. Server1 fails. You discover that DHCP clients can no longer receive IP address leases. You need to ensure that the DHCP clients receive IP addresses immediately. What should you configure from the View/Edit Failover Relationship settings? To answer, select the appropriate setting in the answer area.
ANSWER:
Change to partner down
Q162. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains four member servers named Server1, Server2, Server3, and Server4. All servers run Windows Server 2012 R2.
Server1 and Server3 are located in a site named Site1. Server2 and Server4 are located in a site named Site2. The servers are configured as nodes in a failover cluster named Cluster1.
Dynamic quorum management is disabled.
Cluster1 is configured to use the Node Majority quorum configuration.
You need to ensure that users in Site2 can access Cluster1 if the network connection between the two sites becomes unavailable.
What should you run from Windows PowerShell?
To answer, drag the appropriate commands to the correct location. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Get-ClusterNode Server1 | $_.NodeWeight = 0
Q163. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains four member servers named Server1, Server2, Server3, and Server4. All servers run Windows Server 2012 R2.
Server1 and Server2 are located in a site named Site1. Server3 and Server4 are located in a site named Site2. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 is configured to use the Node Majority quorum configuration.
You need to ensure that Server1 is the only server in Site1 that can vote to maintain quorum.
What should you run from Windows PowerShell?
To answer, drag the appropriate commands to the correct location. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Get-ClusterNode Server2 | $_.NodeWeight = 0
Q164. You have five servers that run Windows Server 2012 R2. The servers have the Failover Clustering feature installed. You deploy a new cluster named Cluster1. Cluster1 is configured as shown in the following table.
Server1, Server2, and Server3 are configured as the preferred owners of the cluster roles.
Dynamic quorum management is disabled.
You plan to perform hardware maintenance on Server3.
You need to ensure that if the WAN link between Site1 and Site2 fails while you are performing maintenance on Server3, the cluster resource will remain available in Site1.
What should you do?
A. Add a file share witness in Site1.
B. Enable DrainOnShutdown on Cluster1.
C. Remove the node vote for Server4 and Server5.
D. Remove the node vote for Server3.
ANSWER: C. Remove the node vote for Server4 and Server5.
Q165. Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 has the DHCP Server server role installed. DHCP is configured as shown in the exhibit. (Click the Exhibit button.)
You discover that client computers cannot obtain IPv4 addresses from DC1. You need to ensure that the client computers can obtain IPv4 addresses from DC1. What should you do?
A. Activate the scope.
B. Authorize DC1.
C. Disable the Allow filters.
D. Disable the Deny filters.
ANSWER: C. Disable the Allow filters. (There are NO items to show in this view for Deny Filters, so it must have Allow Filters that automatically deny access to the DHCP server addresses to any client computer not on the list.)
Q166. Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC2 has the DHCP Server server role installed. DHCP is configured as shown in the exhibit. (Click the Exhibit button.)
You discover that client computers cannot obtain IPv4 addresses from DC2. You need to ensure that the client computers can obtain IPv4 addresses from DC2. What should you do?
A. Enable the Allow filters.
B. Authorize DC2.
C. Disable the Deny filters.
D. Restart the DHCP Server service.
ANSWER: B. Authorize DC2.
Q167. Your network contains an Active Directory domain named contoso.com. The domain contains two Active Directory sites named Site1 and Site2. You need to configure the replication between the sites to occur by using change notification.
Which attribute should you modify?
ANSWER:
Options attribute
Q168. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2. The servers have the Hyper- V server role installed.
A certification authority (CA) is available on the network. A virtual machine named vml.contoso.com is replicated from Server1 to Server2. A virtual machine named vm2.contoso.com is replicated from Server2 to Server1. You need to configure Hyper-V to encrypt the replication of the virtual machines. Which common name should you use for the certificates on each server? To answer, configure the appropriate common name for the certificate on each server in the answer area.
ANSWER:
Server1 - server1.contoso.com
Server2 - server2.contoso.com
Q169. Hotspot Question
Your network contains an Active Directory domain named adatum.com. All servers run Windows Server 2012 R2. All domain controllers have the DNS Server server role installed.
You have a domain controller named DC1.On DC1, you create an Active Directory-integrated zone named adatum.com and you sign the zone by using DNSSEC.
You deploy a new read-only domain controller (RODC) named RODC1.
You need to ensure that the adatum.com zone replicates to RODC1.
What should you configure on DC1?
To answer, select the appropriate tab in the answer area.
ANSWER:
Zone transfers
Q170. Hotspot Question
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. The domain contains two domain controllers. The domain controllers are configured as shown in the following table.
On DC1, you create an Active Directory-integrated zone named Zone1. You verify that Zone1 replicates to DC2.
You use DNSSEC to sign Zone1.
You discover that the updates to Zone1 fail to replicate to DC2.
You need to ensure that Zone1 replicates to DC2.
What should you configure on DC1?
To answer, select the appropriate tab in the answer area.
ANSWER:
Zone transfers
Q171. You have a datacenter that contains six servers. Each server has the Hyper-V server role installed and runs Windows Server 2012 R2. The servers are configured as shown in the following table.
Host4 and Host5 are part of a cluster named Cluster1. Cluster1 hosts a virtual machine named VM1. You need to move VM1 to another Hyper-V host. The solution must minimize the downtime of VM1. To which server and by which method should you move VM1?
A. To Host3 by using a storage migration
B. To Host6 by using a storage migration
C. To Host2 by using a live migration
D. To Host1 by using a quick migration
ANSWER: A. To Host3 by using a storage migration
Q172. Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts 10 virtual machines that run Windows Server 2012 R2. You add a new server named Server2. Server2 has faster hard disk drives, more RAM, and a different processor manufacturer than Server1.
You need to move all of the virtual machines from Server1 to Server2. The solution must minimize downtime. What should you do for each virtual machine?
A. Perform a quick migration.
B. Perform a storage migration.
C. Export the virtual machines from Server1 and import the virtual machines to Server2.
D. Perform a live migration.
ANSWER: C. Export the virtual machines from Server1 and import the virtual machines to Server2.
Q173. Your network contains three servers named HV1, HV2, and Server1 that run Windows Server 2012 R2. HV1 and HV2 have the Hyper-V server role installed. Server1 is a file server that contains 3 TB of free disk space.
HV1 hosts a virtual machine named VM1. The virtual machine configuration file for VM1 is stored in D:\VM and the virtual hard disk file is stored in E:\VHD.
You plan to replace drive E with a larger volume.
You need to ensure that VM1 remains available from HV1 while drive E is being replaced. You want to achieve this goal by using the minimum amount of administrative effort.
What should you do?
A. Perform a live migration to HV2.
B. Add HV1 and HV2 as nodes in a failover cluster. Perform a storage migration to HV2.
C. Add HV1 and HV2 as nodes in a failover cluster. Perform a live migration to HV2.
D. Perform a storage migration to Server1.
ANSWER: D. Perform a storage migration to Server1.
Q174. Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
Server1 hosts several virtual machines. The virtual machine configuration files are stored on drive D and the VHD files are stored on drive E.
You plan to replace drive E with a larger volume.
You need to ensure that the virtual machines on Server1 remain available while drive E is being replaced.
What should you do?
A. Perform a live migration.
B. Perform a quick migration.
C. Add Server1 and Server2 as nodes in a failover cluster.
D. Perform a storage migration .
ANSWER: D. Perform a storage migration.
Q175. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role installed. The servers are configured as shown in the following table.
You add a third server named Server3 to the network. Server3 has Intel processors. You need to move VM3 and VM6 to Server3. The solution must minimize downtime on the virtual machines.
Which method should you use to move each virtual machine? To answer, select the appropriate method for each virtual machine in the answer area.
ANSWER:
VM3: export and import
VM6: live migration
The contoso.com forest contains a server named Server1.
You need to ensure that users in litwareinc.com can access resources on Server1.
What should you do?
A. Install Active Directory Rights Management Services on a domain controller in contoso.com.
B. Modify the permission on the Server1 computer account.
C. Install Active Directory Rights Management Services on a domain controller in litwareinc.com.
D. Configure SID filtering on the trust.
ANSWER: B. Modify the permission on the Server1 computer account.
Explanation:
Q136. Your network contains two Active Directory forests named contoso.com and adatum.com. All of the domain controllers in both of the forests run Windows Server 2012 R2. The adatum.com domain contains a file server named Servers. Adatum.com has a one-way forest trust to contoso.com. A contoso.com user name User10 attempts to access a shared folder on Servers and receives the error message shown in the exhibit. (Click the Exhibit button.)
You verify that the Authenticated Users group has Read permissions to the Data folder. You need to ensure that User10 can read the contents of the Data folder on Server5 in the adatum.com domain.
What should you do?
A. Grant the Other Organization group Read permissions to the Data folder.
B. Modify the list of logon workstations of the contoso\User10 user account.
C. Enable the Netlogon Service (NP-In) firewall rule on Server5.
D. Modify the permissions on the Server5 computer object in Active Directory.
ANSWER: D. Modify the permissions on the Server5 computer object in Active Directory.
Q137. You have a server named DNS1 that runs Windows Server 2012 R2.
You discover that the DNS resolution is slow when users try to access the company intranet home page by using the URL http://companyhome.
You need to provide single-label name resolution for CompanyHome that is not dependent on the suffix search order.
Which three cmdlets should you run? (Each correct answer presents part of the solution.
Choose three.)
A. Add-DnsServerPrimaryZone
B. Add-DnsServerResourceRecordCName
C. Set-DnsServerDsSetting
D. Set-DnsServerGlobalNameZone
E. Set-DnsServerEDns
F. Add-DnsServerDirectory Partition
ANSWER: ABD. Add-DnsServerPrimaryZone + Add-DnsServerResourceRecordCName + Set-DnsServerGlobalNameZone
Explanation:
*The Add-DnsServerPrimaryZone cmdlet adds a specified primary zone on a Domain Name System (DNS) server.
* The Add-DnsServerResourceRecordCName cmdlet adds a canonical name (CNAME) resource record to a specified Domain Name System (DNS) zone. A CNAME record allows you to use more than one resource record to refer to a single host *The Set-DnsServerGlobalNameZone cmdlet enables or disables single-label Domain Name System (DNS) queries.
It also changes configuration settings for a GlobalNames zone.
The GlobalNames zone supports short, easy-to-use names instead of fully qualified domain names (FQDNs) without using Windows Internet Name Service (WINS) technology. For instance, DNS can query SarahJonesDesktop instead of SarahJonesDesktop.contoso.com
Q138. You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the DNS Server server role installed. You need to configure Server1 to resolve queries for single-label DNS names. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Run the Set-DNSServerGlobalNameZone cmdlet.
B. Modify the DNS suffix search list setting.
C. Modify the Primary DNS Suffix Devolution setting.
D. Create a zone named “.”.
E. Create a zone named GlobalNames.
F. Run the Set-DNSServerRootHint cmdlet.
ANSWER: AE. Run the Set-DNSServerGlobalNameZone cmdlet + Create a zone named GlobalNames.
You have a server named Server1 that runs Windows Server 2012. Server1 has the DNS
Server server role installed. You need to configure Server1 to resolve queries for single-label DNS names. Which two actions should you perform? (Each correct answer presents
part of the solution. Choose two.)
A. Run the Set-DNSServerGlobalNameZone cmdlet.
B. Modify the DNS suffix search list setting.
C. Modify the Primary DNS Suffix Devolution setting.
D. Create a zone named “.”.
E. Create a zone named GlobalNames.
F. Run the Set-DNSServerRootHint cmdlet.
??Answer: B, D. Explanation: ipass4sure.com
Your network contains an Active Directory domain named contoso.com. The domain contains a DNS server named Server1. Server1 is configured to resolve single-label names for DNS clients.
You need to view the number of queries for single-label names that are resolved by Server1.
What command should you run? To answer, select the appropriate options in the answer area.
Get-DnsServerStatistics -ZoneName GlobalNames
Q140. Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. Server1 is a BranchCache hosted cache server that is located in a branch office.
The network contains client computers that run either Windows 7 or Windows 8.
For the branch office, all of the user accounts and the client computer accounts are located in an organizational unit (OU) named Branch1. A group Policy object (GPO) named GPO1 is linked to Branch1. GPO1 contains the BranchCache settings.
You discover that users in the branch office who have client computers that run Windows 7 do not access cached content from Server1. Users in the branch office who have Windows 8 computers access cached content from Server1.
You need to confiure the Windows 7 computers to use BranchCache on Server1. Which setting should you configure in GPO1?
To answer, select the appropiate setting in the answer area.
ANSWER:
Set BranchCache Hosted Cache mode
Q141. Your network contains an Active Directory domain named contoso.com. All client computers run Windows 8 Enterprise.
You have a remote site that only contains client computers. All of the client computer accounts are located in an organizational unit (OU) named Remote1. A Group Policy object (GPO) named GPO1 is linked to the Remote1 OU.
You need to configure BranchCache for the remote site.
Which two settings should you configure in GPO1? To answer, select the appropiate setting in the answer area.
ANSWER:
Turn on BranchCache
Set BranchCache Distributed Cache mode
The network contains an Active Directory domain named adatum.com. Client computers run eiter Windows 7 Enterprise or Windows 8 Enterprise.
The main office contains 1,000 client computers and 50 servers. The branch office contains 20 client computers.
All computer accounts are located in an organizational unit (OU) named SeattleComputers. A Group Policy object (GPO) named GPO1 is linked to the SeattleComputers OU.
You need to configure BranchCache for the remote site.
Which two settings should you configure in GPO1? To answer, select the appropiate setting in the answer area.
ANSWER:
Turn on BranchCache
Set BranchCache Distributed Cache mode
The network contains an Active Directory forest named contoso.com. The contoso.com domain contains three member servers named Server1, Server2, and Server3. All servers run Windows Server 2012 R2.
In the main office, you configure Server1 as a file server that uses BranchCache.
In the branch office, you configure Server2 and Server3 as BranchCache hosted cache servers.
You are creating a Group Policy for the branch office site.
Which two Group Policy settings should you configure? To answer, select the appropriate two settings in the answer area.
ANSWER:
Turn on BranchCache
Set BranchCache Hosted Cache mode
Q144. Your company has a main office and a branch office. An Active Directory site exists for each office.
The network contains an Active Directory forest named contoso.com. The contoso.com domain contains three member servers named Server1, Server2, and Server3. All servers run Windows Server 2012 R2.
In the main office, you configure Server1 as a file server that uses BranchCache.
In the branch office, you configure Server2 and Server3 as BranchCache hosted cache servers.
You are creating a Group Policy for the branch office site. In the branch office, you need to configure the client computers that run Windows 8 to use Server2 and Server3 as BranchCache.
ANSWER:
Turn on BranchCache
Configure Hosted Cache Servers
![clip_image001[72]](http://examgod.com/l2pimages/f98e0646ba5b_79CB/clip_image00172_thumb.jpg)
Q145. You plan to deploy a failover cluster that will contain two nodes that run Windows Server 2012 R2. You need to configure a witness disk for the failover cluster. How should you configure the witness disk? To answer, drag the appropriate configurations to the correct location or locations. Each configuration may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Disk Type: Basic / File System: NTFS
Q146. Drag and Drop Question
You have two failover clusters named Cluster1 and Cluster2. All of the nodes in both of the clusters run Windows Server 2012 R2.
Cluster1 hosts two virtual machines named VM1 and VM2.
You plan to configure VM1 and VM2 as nodes in a new failover cluster named Cluster3.
You need to configure the witness disk for Cluster3 to be hosted on Cluster2.
Which three actions should you perform in sequence?
To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
On Cluster1, add an iSCSI hard disk drive to VM1 and VM2
On Cluster2, install the File Server role service
On Cluster2, install the Scale-Out File Server for application data (Scale-Out File Server) option.
Q147. Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. All servers run Windows Server 2012 R2. All domain user accounts have the Division attribute automatically populated as part of the user provisioning process. The Support for Dynamic Access Control and Kerberos armoring policy is enabled for the domain. You need to control access to the file shares on Server1 based on the values in the Division attribute and the Division resource property. Which three actions should you perform in sequence?
ANSWER:
From Active Directory Administrative Center, create a claim type
From Active Directory Administrative Center, create a reference resource property
On the Shared folders, set the classification value.
Q148. Hotspot Question
Your network contains an Active Directory forest.
You implement Dynamic Access Control in the forest.
You have the claim types shown in the Claim Types exhibit. (Click the Exhibit button.)
The properties of a user named User1 are configured as shown in the User1 exhibit. (Click the Exhibit button.)
The output of Whoami /claims for a user named User2 is shown in the Whoa mi exhibit.
(Click the Exhibit button.)
Select Yes if the statement can be shown to be true based on the available information; otherwise select No. Each correct selection is worth one point.
ANSWER:
The security token for User1 contains at least one claim - Yes
A value is set for the department attribute of User2 - No
The client computer of User2 supports Dynamic Access Control - Yes
Q149. Your network contains an Active Directory forest named contoso.com. The forest contains a single domain, The forest functional level is Windows Server 2012 R2. You have a domain controller named DC1.
On DC1, you create a new Group Policy object (GPO) named GPO1.
You need to verify that GPO1 was replicated to all of the domain controllers.
Which tool should you use?
A. Active Directory Administrative Center
B. Group Policy Management
C. DFS Management
D. Active Directory Sites and Services
E. Gpresult
ANSWER: B. Group Policy Management.
Q150. Your network contains an Active Directory domain named adatum.com. The domain contains two sites named Site1 and Site2 and two domain controllers named DC1 and DC2.DC1 is located in Site1 and DC2 is located in Site2.
You install an additional domain controller named DC3 in Site1 and you ship DC3 to Site2. A technician connects DC3 to Site2.
You discover that users in Site2 are authenticated only by DC2.
You need to ensure that the users in Site2 are authenticated by both DC2 and DC3.
What should you do?
A. In Active Directory Users and Computers, configure the msDS-PrimaryComputer attribute for DC3.
B. From Active Directory Sites and Services, modify the site link between Site1 and Site2.
C. From Active Directory Sites and Services, move DC3.
D. In Active Directory Users and Computers, configure the msDS-Site-Affinity attribute for DC3.
ANSWER: C. From Active Directory Sites and Services, move DC3.
Q151. Your network contains an Active Directory domain named contoso.com. The domain contains two sites named Site1 and Site2 and two domain controllers named DC1 and DC2. Both domain controllers are located in Site1.
You install an additional domain controller named DC3 in Site1 and you ship DC3 to Site2. A technician connects DC3 to Site2. You discover that users in Site2 are authenticated by all three domain controllers.
You need to ensure that the users in Site2 are authenticated by DC1 or DC2 only if DC3 is unavailable.
What should you do?
A. From Network Connections, modify the IP address of DC3.
B. In Active Directory Sites and Services, modify the Query Policy of DC3.
C. From Active Directory Sites and Services, move DC3.
D. In Active Directory Users and Computers, configure the msDS-PrimaryComputer attribute for the users in Site2.
ANSWER: C. From Active Directory Sites and Services, move DC3.
Q152. Your network contains an Active Directory domain named adatum.com. The domain contains two sites named Site1 and Site2 and two domain controllers named DC1 and DC2.DC1 is located in Site1 and DC2 is located in Site2. You install an additional domain controller named DC3 in Site1 and you ship DC3 to Site2. A technician connects DC3 to Site2.
You discover that users in Site2 are authenticated only by DC2.
You need to ensure that the users in Site2 are authenticated by both DC2 and DC3.
What should you do?
A. From Network Connections, modify the IP address of DC3.
B. In Active Directory Sites and Services, modify the Query Policy of DC3.
C. From Active Directory Sites and Services, move DC3.
D. In Active Directory Users and Computers, configure the msDS-PrimaryComputer attribute for the users in Site2.
ANSWER: C. From Active Directory Sites and Services, move DC3.
Q152. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 is an enterprise root certification authority (CA) for contoso.com.
You need to ensure that the members of a group named Group1 can request code signing
certificates. The certificates must be issued automatically to the members.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From Certificate Templates, modify the certificate template.
B. From Certification Authority, add a certificate template to be issued.
C. From Certificate Authority, modify the CA properties.
D. From Certificate Templates, duplicate a certificate template.
E. From Certificate Authority, stop and start the Active Directory Certificate Services (AD CS) service.
ANSWER: AB.
Explanation: First modify the certificate template in Certificate Templates, then add it in Certification Authority.
Q153. Your network contains two Active Directory forests named contoso.com and corp.contoso.com.
User1 is a member of the DnsAdmins domain local group in contoso.com.
User1 attempts to create a conditional forwarder to corp.contoso.com but receive an error message shown in the exhibit. (Click the Exhibit button.)

You need to configure bi-directional name resolution between the two forests.
What should you do first?
A. Add User1 to the DnsUpdateProxy group.
B. Configure the zone to be Active Directory-integrated.
C. Enable the Advanced view from DNS Manager.
D. Run the New Delegation Wizard.
ANSWER: B. Configure the zone to be Active Directory-integrated.
Q154. Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com. The functional level of the forest is Windows Server 2003. You have a domain outside the forest named adatum.com. You need to configure an access solution to meet the following requirements:
- Users in adatum.com must be able to access resources in contoso.com.
- Users in adatum.com must be prevented from accessing resources in fabrikam.com.
- Users in both contoso.com and fabrikam.com must be prevented from accessing resources in adatum.com.
What should you create?
A. a one-way external trust from contoso to adatum.com
B. a one-way realm trust from adatum.com to contoso.com
C. a one-way external trust from adatum.com to contoso.com
D. a one-way realm trust from contoso.com to adatum.com
ANSWER: A. a one-way EXTERNAL trust from contoso to adatum.com
Q155. Hotspot Question
Your network contains three Active Directory forests. The forests are configured as shown in the following table.
A two-way forest trust exists between contoso.com and division1.contoso.com. A two-way forest trust also exists between contoso.com and division2.contoso.com.
You plan to create a one-way forest trust from division1.contoso.com to division2.contoso.com.
You need to ensure that any cross-forest authentication requests are sent to the domain controllers in the appropriate forest after the trust is created.
How should you configure the existing forest trust settings?
In the table below, identify which configuration must be performed in each forest. Make only one selection in each column. Each correct selection is worth one point.
ANSWER:
Division2.contoso.com = Add division1.contoso.com as a name suffix routing entry
Division1.contoso.com = Add division2.contoso.com as an EXCLUSION to the name suffix routing entry of contoso.com
You install the File and Storage Services server role on FS1.
From Windows Explorer, you view the properties of a shared folder named Share1 and you discover that the Classification tab is missing.
You need to ensure that you can assign classifications to Share1 from Windows Explorer manually.
What should you do?
A. From Folder Options, select Show hidden files, folders, and drives.
B. From Folder Options, clear Use Sharing Wizard (Recommend).
C. Install the File Server Resource Manager role service.
D. Install the Enhanced Storage feature.
ANSWER: C. Install the File Server Resource Manager role service.
Q157. You have a server named Server1 that runs Windows Server 2012 R2.
You install the File and Storage Services server role on Server1.
From Windows Explorer, you view the properties of a shared folder named Folder1 and you discover that the Classification tab is missing.
You need to ensure that you can assign classifications to Folder1 from Windows Explorer manually.
What should you do?
A. Install the Share and Storage Management tools.
B. From Folder Options, clear Hide protected operating system files (Recommended).
C. Install the File Server Resource Manager role service.
D. From Folder Options, señect the Always show menus.
ANSWER: C. Install the File Server Resource Manager role service.
Q158. Your network contains an Active Directory domain named adatum.com. The domain contains a file server named FS1 that runs Windows Server 2012 R2 and has the File Server Resource Manager role service installed. All client computers run Windows 8.
File classification and Access-Denied Assistance are enabled on FS1.
You need to ensure that if users receive an Access Denied message, they can request assistance by email from the Access Denied dialog box.
What should you configure?
A. A file management task.
B. The File Server Resource Manager Options
C. A report task
D. A classification property.
ANSWER: B. The File Server Resource Manager Options.
Q159. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 and a server named Server1. Both servers run Windows Server 2012 R2.
You configure the classification of a share on Server1 as shown in the Share1 Properties exhibit. (Click the Exhibit button.)
You configure the resource properties in Active Directory as shown in the Resource Properties exhibit. (Click the Exhibit button.)
You need to ensure that the Impact classification can be assigned to Share1 immediately.
Which cmdlet should you run on each server?
To answer, select the appropriate cmdlet for each server in the answer area.
DC1: SET-AdResourceProperty
Server1: UPDATE-FsrmClassificationPropertyDefinition
Q160. You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource Manager role service installed. You attempt to delete a classification property and you receive the error message as shown in the exhibit. (Click the Exhibit button.)
You need to delete the is Confidential classification property.
What should you do?
A. Delete the classification rule that is assigned the isConfidential classification property.
B. Disable the classification rule that is assigned the isConfidential classification property.
C. Set files that have an isConfidential classification property value of Yes to No.
D. Clear the isConfidential classification property value of all files.
ANSWER: A. Delete the classification rule that is assigned the isConfidential classification property.
Q161. Hotspot Question
Your network contains two DHCP servers named Server1 and Server2. Server1 fails. You discover that DHCP clients can no longer receive IP address leases. You need to ensure that the DHCP clients receive IP addresses immediately. What should you configure from the View/Edit Failover Relationship settings? To answer, select the appropriate setting in the answer area.
ANSWER:
Change to partner down
Q162. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains four member servers named Server1, Server2, Server3, and Server4. All servers run Windows Server 2012 R2.
Server1 and Server3 are located in a site named Site1. Server2 and Server4 are located in a site named Site2. The servers are configured as nodes in a failover cluster named Cluster1.
Dynamic quorum management is disabled.
Cluster1 is configured to use the Node Majority quorum configuration.
You need to ensure that users in Site2 can access Cluster1 if the network connection between the two sites becomes unavailable.
What should you run from Windows PowerShell?
To answer, drag the appropriate commands to the correct location. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Get-ClusterNode Server1 | $_.NodeWeight = 0
Q163. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains four member servers named Server1, Server2, Server3, and Server4. All servers run Windows Server 2012 R2.
Server1 and Server2 are located in a site named Site1. Server3 and Server4 are located in a site named Site2. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 is configured to use the Node Majority quorum configuration.
You need to ensure that Server1 is the only server in Site1 that can vote to maintain quorum.
What should you run from Windows PowerShell?
To answer, drag the appropriate commands to the correct location. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Get-ClusterNode Server2 | $_.NodeWeight = 0
Q164. You have five servers that run Windows Server 2012 R2. The servers have the Failover Clustering feature installed. You deploy a new cluster named Cluster1. Cluster1 is configured as shown in the following table.
Server1, Server2, and Server3 are configured as the preferred owners of the cluster roles.
Dynamic quorum management is disabled.
You plan to perform hardware maintenance on Server3.
You need to ensure that if the WAN link between Site1 and Site2 fails while you are performing maintenance on Server3, the cluster resource will remain available in Site1.
What should you do?
A. Add a file share witness in Site1.
B. Enable DrainOnShutdown on Cluster1.
C. Remove the node vote for Server4 and Server5.
D. Remove the node vote for Server3.
ANSWER: C. Remove the node vote for Server4 and Server5.
You discover that client computers cannot obtain IPv4 addresses from DC1. You need to ensure that the client computers can obtain IPv4 addresses from DC1. What should you do?
A. Activate the scope.
B. Authorize DC1.
C. Disable the Allow filters.
D. Disable the Deny filters.
ANSWER: C. Disable the Allow filters. (There are NO items to show in this view for Deny Filters, so it must have Allow Filters that automatically deny access to the DHCP server addresses to any client computer not on the list.)
Q166. Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC2 has the DHCP Server server role installed. DHCP is configured as shown in the exhibit. (Click the Exhibit button.)
A. Enable the Allow filters.
B. Authorize DC2.
C. Disable the Deny filters.
D. Restart the DHCP Server service.
ANSWER: B. Authorize DC2.
Q167. Your network contains an Active Directory domain named contoso.com. The domain contains two Active Directory sites named Site1 and Site2. You need to configure the replication between the sites to occur by using change notification.
Which attribute should you modify?
ANSWER:
Options attribute
Q168. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2. The servers have the Hyper- V server role installed.
A certification authority (CA) is available on the network. A virtual machine named vml.contoso.com is replicated from Server1 to Server2. A virtual machine named vm2.contoso.com is replicated from Server2 to Server1. You need to configure Hyper-V to encrypt the replication of the virtual machines. Which common name should you use for the certificates on each server? To answer, configure the appropriate common name for the certificate on each server in the answer area.
Server1 - server1.contoso.com
Server2 - server2.contoso.com
Q169. Hotspot Question
Your network contains an Active Directory domain named adatum.com. All servers run Windows Server 2012 R2. All domain controllers have the DNS Server server role installed.
You deploy a new read-only domain controller (RODC) named RODC1.
You need to ensure that the adatum.com zone replicates to RODC1.
What should you configure on DC1?
To answer, select the appropriate tab in the answer area.
ANSWER:
Zone transfers
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. The domain contains two domain controllers. The domain controllers are configured as shown in the following table.
On DC1, you create an Active Directory-integrated zone named Zone1. You verify that Zone1 replicates to DC2.
You use DNSSEC to sign Zone1.
You discover that the updates to Zone1 fail to replicate to DC2.
You need to ensure that Zone1 replicates to DC2.
What should you configure on DC1?
To answer, select the appropriate tab in the answer area.
ANSWER:
Zone transfers
Q171. You have a datacenter that contains six servers. Each server has the Hyper-V server role installed and runs Windows Server 2012 R2. The servers are configured as shown in the following table.
Host4 and Host5 are part of a cluster named Cluster1. Cluster1 hosts a virtual machine named VM1. You need to move VM1 to another Hyper-V host. The solution must minimize the downtime of VM1. To which server and by which method should you move VM1?
A. To Host3 by using a storage migration
B. To Host6 by using a storage migration
C. To Host2 by using a live migration
D. To Host1 by using a quick migration
ANSWER: A. To Host3 by using a storage migration
Q172. Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts 10 virtual machines that run Windows Server 2012 R2. You add a new server named Server2. Server2 has faster hard disk drives, more RAM, and a different processor manufacturer than Server1.
You need to move all of the virtual machines from Server1 to Server2. The solution must minimize downtime. What should you do for each virtual machine?
A. Perform a quick migration.
B. Perform a storage migration.
C. Export the virtual machines from Server1 and import the virtual machines to Server2.
D. Perform a live migration.
ANSWER: C. Export the virtual machines from Server1 and import the virtual machines to Server2.
Q173. Your network contains three servers named HV1, HV2, and Server1 that run Windows Server 2012 R2. HV1 and HV2 have the Hyper-V server role installed. Server1 is a file server that contains 3 TB of free disk space.
HV1 hosts a virtual machine named VM1. The virtual machine configuration file for VM1 is stored in D:\VM and the virtual hard disk file is stored in E:\VHD.
You plan to replace drive E with a larger volume.
You need to ensure that VM1 remains available from HV1 while drive E is being replaced. You want to achieve this goal by using the minimum amount of administrative effort.
What should you do?
A. Perform a live migration to HV2.
B. Add HV1 and HV2 as nodes in a failover cluster. Perform a storage migration to HV2.
C. Add HV1 and HV2 as nodes in a failover cluster. Perform a live migration to HV2.
D. Perform a storage migration to Server1.
ANSWER: D. Perform a storage migration to Server1.
Q174. Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
Server1 hosts several virtual machines. The virtual machine configuration files are stored on drive D and the VHD files are stored on drive E.
You plan to replace drive E with a larger volume.
You need to ensure that the virtual machines on Server1 remain available while drive E is being replaced.
What should you do?
A. Perform a live migration.
B. Perform a quick migration.
C. Add Server1 and Server2 as nodes in a failover cluster.
D. Perform a storage migration .
ANSWER: D. Perform a storage migration.
Q175. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role installed. The servers are configured as shown in the following table.
You add a third server named Server3 to the network. Server3 has Intel processors. You need to move VM3 and VM6 to Server3. The solution must minimize downtime on the virtual machines.
Which method should you use to move each virtual machine? To answer, select the appropriate method for each virtual machine in the answer area.
ANSWER:
VM3: export and import
VM6: live migration
Q176. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains the two servers.The servers are configured as shown in the following table.
You investigate a report about the potential compromise of a private key for a certificate issued to Server2.
You need to revoke the certificate issued to Server2. The solution must ensure that the revocation can be reverted. Which reason code should you select? To answer, select the appropriate reason code in the answer area.
ANSWER:
Certificate Hold
Q177. Your network contains an Active Directory domain named contoso.com. The network contains a file server named Server1 that runs Windows Server 2012 R2. You are configuring a central access policy for temporary employees. You enable the Department resource property and assign the property a suggested value of Temp. You need to configure a target resource condition for the central access rule that is scoped to resources assigned to Temp only. Which condition should you use?
Your network contains an Active Directory domain named contoso.com. The domain contains the two servers.The servers are configured as shown in the following table.
You investigate a report about the potential compromise of a private key for a certificate issued to Server2.
You need to revoke the certificate issued to Server2. The solution must ensure that the revocation can be reverted. Which reason code should you select? To answer, select the appropriate reason code in the answer area.
ANSWER:
Certificate Hold
Q177. Your network contains an Active Directory domain named contoso.com. The network contains a file server named Server1 that runs Windows Server 2012 R2. You are configuring a central access policy for temporary employees. You enable the Department resource property and assign the property a suggested value of Temp. You need to configure a target resource condition for the central access rule that is scoped to resources assigned to Temp only. Which condition should you use?
A. (Temp.Resource Equals “Department”)
B. (Resource.Temp Equals “Department”)
C. (Resource.Department Equals “Temp”)
D. (Department.Value Equals “Temp”)
ANSWER: C. (Resource.Department Equals “Temp”)
Q178. Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2.
The domain contains a domain controller named DC1 that is configured as an enterprise root certification authority (CA).
All users in the domain are issued a smart card and are required to log on to their domain- joined client computer by using their smart card.
A user named User1 resigned and started to work for a competing company.
You need to prevent User1 immediately from logging on to any computer in the domain. The solution must not prevent other users from logging on to the domain.
Which tool should you use?
A. Active Directory Users and Computers
B. Active Directory Sites and Services
C. The Certificates snap-in
D. Server Manager
ANSWER: A. Active Directory Users and Computers
Q179. Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2.
The domain contains a domain controller named DC1 that is configured as an enterprise root certification authority (CA).
All users in the domain are issued a smart card and are required to log on to their domain- joined client computer by using their smart card.
A user named User1 resigned and started to work for a competing company.
You need to prevent User1 immediately from logging on to any computer in the domain. The solution must not prevent other users from logging on to the domain.
Which tool should you use?
A. Server Manager
B. The Certificates snap-in
C. Active Directory Users and Computers
D. The Certification Authority console.
ANSWER: D. The Certification Authority console.
Q180. Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. The domain contains a domain controller named DC1 that is configured as an enterprise root certification authority (CA). All users in the domain are issued a smart card and are required to log on to their domain-joined client computer by using their smart card. A user named User1 resigned and started to work for a competing company. You need to prevent User1 immediately from logging on to any computer in the domain. The solution must not prevent other users from logging on to the domain. Which tool should you use?
A. Active Directory Sites and Services
B. Active Directory Administrative Center
C. Server Manager
D. Certificate Templates
ANSWER: B. Active Directory Administrative Center
Explanation: B. Disable user1 from ADAC (http://technet.microsoft.com/en-us/library/dd861307.aspx)
Q181. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Certificate Services server role installed and configured. Q180. Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. The domain contains a domain controller named DC1 that is configured as an enterprise root certification authority (CA). All users in the domain are issued a smart card and are required to log on to their domain-joined client computer by using their smart card. A user named User1 resigned and started to work for a competing company. You need to prevent User1 immediately from logging on to any computer in the domain. The solution must not prevent other users from logging on to the domain. Which tool should you use?
A. Active Directory Sites and Services
B. Active Directory Administrative Center
C. Server Manager
D. Certificate Templates
ANSWER: B. Active Directory Administrative Center
Explanation: B. Disable user1 from ADAC (http://technet.microsoft.com/en-us/library/dd861307.aspx)
For all users, you are deploying smart cards for logon. You are using an enrollment agent to enroll the smart card certificates for the users.
You need to configure the Contoso Smartcard Logon certificate template to support the use of the enrollment agent.
Which setting should you modify? To answer, select the appropriate setting in the answer area.
ANSWER:
Any Purpose
Q182. Hotspot Question
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role installed.
Server1 and Server2 have different processor models from the same manufacturer.
On Server1, you plan to create a virtual machine named VM1. Eventually, VM1 will be exported to Server2.
You need to ensure that when you import VM1 to Server2, you can start VM1 from saved snapshots.
What should you configure on VM1? To answer, select the appropriate node in the answer area.
ANSWER:
(Processor =>) Compatibility
Q183. Hotspot Question
Your network contains two Hyper-V hosts that are configured as shown in the following table.
You create a virtual machine on Server1 named VM1.
You plan to export VM1 from Server1 and import VM1 to Server2. You need to ensure that you can start the imported copy of VM1 from snapshots.
What should you configure on VM1?
To answer, select the appropriate node in the answer area.
ANSWER:
Compatibility
Q184. Your network contains an Active Directory forest named adatum.com. All servers run Windows Server 2012 R2. The domain contains four servers. The servers are configured as shown in the following table.
![clip_image001[58]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00158_thumb.jpg)
You need to deploy IP Address Management (IPAM) to manage DNS and DHCP.
On which server should you install IPAM?
A. Server1
B. Server2
C. Server3
D. Server4
ANSWER: D. Server4.
Explanation: IPAM cannot be installed on Domain Controllers (nor RODCs).
Q185. Your network contains an Active Directory forest named adatum.com. All servers run Windows Server 2012 R2. The domain contains four servers. The servers are configured as shown in the following table.
You need to deploy IP Address Management (IPAM) to manage DNS and DHCP.
On which server should you install IPAM?
A. DC1
B. DC2
C. DC3
D. Server1
ANSWER: D. Server1.
Explanation: IPAM cannot be installed on DCs.
Q186. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2.
You install the DHCP Server server role on Server1 and Server2. You install the IP Address Management (IPAM) Server feature on Server1.
You notice that you cannot discover Server1 or Server2 in IPAM.
You need to ensure that you can use IPAM to discover the DHCP infrastructure.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. On Server2, create an IPv4 scope.
B. On Server1, run the Add-IpamServerInventory cmdlet.
C. On Server2, run the Add-DhcpServerInDc cmdlet
D. On both Server1 and Server2, run the Add-DhcpServerv4Policy cmdlet.
E. On Server1, uninstall the DHCP Server server role.
ANSWER: BC. On Server1, run the Add-IpamServerInventory cmdlet + On Server2, run the Add-DhcpServerInDc cmdlet
Explanation: The Add-IpamServerInventory cmdlet adds a new infrastructure server to the IP Address Management (IPAM) server inventory. Use the fully qualified domain name (FQDN) of the server to add to the server inventory.
The Add-DhcpServerInDC cmdlet adds the computer running the DHCP server service to the list of authorized Dynamic Host Configuration Protocol (DHCP) server services in the Active Directory (AD). A DHCP server service running on a domain joined computer needs to be authorized in AD so that it can start leasing IP addresses on the network.
Q187. Your network contains an Active Directory forest. The forest contains one domain named adatum.com. The domain contains three domain controllers. The domain controllers are configured as shown in the following table.
DC2 has all of the domain-wide operations master roles. DC3 has all of the forest-wide operation master roles. You need to ensure that you can use Password Settings objects (PSOs) in the domain.
What should you do first?
A. Uninstall Active Directory from DC1.
B. Change the domain functional level.
C. Transfer the domain-wide operations master roles.
D. Transfer the forest-wide operations master roles.
ANSWER: A. Uninstall Active Directory from DC1.
Q188. Your network contains an Active Directory forest.
The forest contains one domain named contoso.com. The domain contains three domain controllers. The domain controllers are configured as shown in the following table.
DC1 has all of the operations master roles installed. You transfer all of the operations master roles to DC2, and then you uninstall Active Directory from DC1. You need to ensure that you can use Password Settings objects (PSOs) in the domain.
What should you do?
A. Change the domain functional level.
B. Upgrade DC2.
C. Run the dcgpofix.exe command.
D. Transfer the schema master role.
ANSWER: A. Change the domain functional level.
Q189. The File Server Resource Manager role service is installed on Server1. All servers run Windows Server 2012 R2. A Group Policy object (GPO) named GPO1 is linked to the organizational unit (OU) that contains Server1. The following graphic shows the configured settings in GPO1.
Server1 contains a folder named Folder1. Folder1 is shared as Share1.
You attempt to configure access-denied assistance on Server1, but the Enable access-denied assistance option cannot be selected from File Server Resource Manager.
You need to ensure that you can configure access-denied assistance on Server1 manually by using File Server Resource Manager.
Which two actions should you perform?
A. Set the Enable access-denied assistance on client for all file types policy setting to Disabled for GPO1.
B. Set the Customize message for Access Denied errors policy setting to Not Configured for GPO1.
C. Set the Enable access-denied assistance on client for all file types policy setting to Enabled for GPO1.
D. Set the Customize message for Access Denied errors policy setting to Enabled for GPO1.
ANSWER: CD. Set the Customize message for Access Denied errors policy setting to Enabled for GPO1. Set the Enable access-denied assistance on client for all file types policy setting to Enabled for GPO1.
Q190. Your network contains an Active Directory domain named contoso.com. The domain contains domain controllers that run either Windows Server 2003, Windows Server 2008 R2, or Windows Server 2012 R2.
You plan to implement a new Active Directory forest. The new forest will be used for testing and will be isolated from the production network.
In the test network, you deploy a server named Server1 that runs Windows Server 2012 R2. You need to configure Server1 as a new domain controller in a new forest named contoso.test.
The solution must meet the following requirements:
- The functional level of the forest and of the domain must be the same as that of contoso.com
- Server1 must provide name resolution services for contoso.test
What should you do?
To answer, configure the appropiate options in the answer area.
ANSWER:
Forest functional level: 2003
Domain functional level:2003
Domain Name System (DNS) Server - Checked
Q191. Your network contains an Active Directory forest named contoso.com. The contoso.com domain only contains domain controllers that run Windows Server 2012 R2.
The forest contains a child domain named child.contoso.com. The child.contoso.com domain only contains domain controllers that run Windows Server 2008 R2. The child.contoso.com domain contains a member server named Server1 that runs Windows Server 2012 R2.
You have access to four administrative user accounts in the forest. The administrative user accounts are configured as shown in the following table.
You need to ensure that you can add a domain controller that runs Windows Server 2012 R2 to the child.contoso.com domain.
Which account should you use to run adprep.exe?
A. Admin1
B. Admin2
C. Admin3
D. Admin4
ANSWER: C. Admin3.
Explanation: Make sure you can log on to the infraestructure master with an account that is a member of the Domain Admins group
Q192. Your network contains an Active Directory domain named contoso.com. The domain contains servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the Active Directory Federation Services server role installed. Server2 is a file server.
Your company introduces a Bring Your Own Device (BYOD) policy.
You need to ensure that users can use a personal device to access domain resources by using Single Sign-On (SSO) while they are connected to the internal network.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. Enable the Device Registration Service in Active Directory.
B. Publish the Device Registration Service by using a Web Application Proxy.
C. Configure Active Directory Federation Services (AD FS) for the Device Registration Service.
D. Create and configure a sync share on Server2.
E. Install the Work Folders role service on Server2.
ANSWER: AC. Enable the Device Registration Service in Active Directory + Configure Active Directory Federation Services (AD FS) for the Device Registration Service.
Q193. Your network contains an Active Directory forest named contoso.com. The forest contains four domains. All servers run Windows Server 2012 R2.
Each domain has a user named User1.
You have a file server named Server1 that is used to synchronize user folders by using the
Work Folders role service.
Server1 has a work folder named Sync1.
You need to ensure that each user has a separate folder in Sync1.
What should you do?
A. From Windows Explorer, modify the Sharing properties of Sync1.
B. Run the Set-SyncServerSetting cmdlet.
C. From File and Storage Services in Server Manager, modify the properties of Sync1.
D. Run the Set-SyncShare cmdlet.
ANSWER: D. Run the Set-SyncShare cmdlet.
Q194. Drag and Drop Question
You have a server that runs Windows Server 2012 R2.
You create a new work folder named Share1.
You need to configure Share1 to meet the following requirements:
Ensure that all synchronized copies of Share1 are encrypted. Ensure that clients synchronize to Share1 every 30 minutes. Ensure that Share1 inherits the NTFS permissions of the parent folder.
Which cmdlet should you use to achieve each requirement?
To answer, drag the appropriate cmdlets to the correct requirements. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Set-SyncShare
Set-SyncServerSettings
Set-SyncShare
Q195. You have an Active Directory Rights Management Services (AD RMS) cluster.
You need to prevent users from encrypting new content. The solution must ensure that the users can continue to decrypt content that was encrypted already.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. From the Active Directory Rights Management Services console, enable decommissioning.
B. From the Active Directory Rights Management Services console, create a user exclusion policy.
C. Modify the NTFS permissions of %systemdrive%\inetpub\wwwroot\_wmcs\licensing.
D. Modify the NTFS permissions of %systemdrive%\inetpub\wwwroot\_wmcs\decommission.
E. From the Active Directory Rights Management Services console, modify the rights policy templates.
ANSWER: BE. From the Active Directory Rights Management Services console, create a user exclusion policy + From the Active Directory Rights Management Services console, modify the rights policy templates.
Q196. You deploy an Active Directory Federation Services (AD FS) 2.1 infrastructure. The infrastructure uses Active Directory as the attribute store. Some users report that they fail to authenticate to the AD FS infrastructure. You discover that only users who run third-party web browsers experience issues. You need to ensure that all of the users can authenticate to the AD FS infrastructure successfully. Which Windows PowerShell command should you run?
A. Set-ADFSProperties -ProxyTrustTokenLifetime 1:00:00
B. Set-ADFSProperties -AddProxyAuthenticationRules None
C. Set-ADFSProperties -SSOLifetime 1:00:00
D. Set-ADFSProperties -ExtendedProtectionTokenCheck None
ANSWER: D. Set-ADFSProperties -ExtendedProtectionTokenCheck None.
Explanation:
A. Sets the valid token lifetime for proxy trust tokens (in minutes). This value is used by the federation server proxy to authenticate with its associated federation server.
B. Specifies a policy rule set that can be used to establish authorization permissions for setting up trust proxies. The default value allows the AD FS 2.0 service user account or any member of BUILTIN\Administrators to register a federation server proxy with the Federation Service.
C. Specifies the duration of the single sign-on (SSO) experience for Web browser clients (in minutes).
D. Specifies the level of extended protection for authentication supported by the federation server. Extended Protection for Authentication helps protect against man-in-the-middle (MITM) attacks, in which an attacker intercepts a client’s credentials and forwards them to a server.
Q197. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains four member servers named Server1, Server2, Server3, and Server4. Server1 and Server2 run Windows Server 2008 R2.
Server1 and Server2 have the Hyper-V server role and the Failover Clustering feature installed. Failover Clustering is configured to provide highly available virtual machines by using a cluster named Cluster1.
Cluster1 hosts 10 virtual machines.
Server3 and Server4 run Windows Server 2012 R2.
You install the Hyper-V server role and the Failover Clustering feature on Server3 and Server4. You create a cluster named Cluster2.
You need to migrate cluster resources from Cluster1 to Cluster2. The solution must minimize downtime on the virtual machines.
Which five actions should you perform?
To answer, move the appropriate five actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
From Failover Cluster Manager in Cluster2, run the migrate a Cluster Wizard
Shut down all of the virtual machines in Cluster1
Mask the shared storage to prevent the storage from being accessed by Cluster1
Unmask the shared storage to present the storage to Cluster2.
Start the virtual machines in Cluster2
Q198. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role and the Failover Clustering feature installed. Server1 and Server2 are members of a cluster named Cluster1. Cluster1 hosts 10 virtual machines.
When you try to migrate a running virtual machine from one server to another, you receive the following error message:
“There was an error checking for virtual machine compatibility on the target node.”
You need to ensure that the virtual machines can be migrated from one node to another.
From which node should you perform the configuration? To answer, select the appropriate node in the answer area.
ANSWER:
Processor
Q199. Your company has two offices. The offices are located in Seattle and Montreal.
The network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Server1 is located in the Seattle office. Server2 is located in the Montreal office. All servers run Windows Server 2012 R2.
You need to create a DHCP scope for video conferencing in the Montreal office. The scope must be configured as shown in the following table.
Which Windows PowerShell cmdlet should you run?
A. Add-DchpServerv4SuperScope
B. Add-DchpServerv4MulticastScope
C. Add-DHCPServerv4Policy
D. Add-DchpServerv4Scope
ANSWER: B. Add-DchpServerv4MulticastScope.
Q200. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Both servers have multiple IPv4 scopes.
Server1 and Server2 are used to assign IP addresses for the network IDs of 172.20.0.0/16 and 131.107.0.0/16.
You install the IP Address Management (IPAM) Server feature on a server named IPAM1 and configure IPAM1 to manage Server1 and Server2.
Some users from the 172.20.0.0 network report that they occasionally receive an IP address conflict error message.
You need to identify whether any scopes in the 172.20.0.0 network ID conflict with one another.
What Windows PowerShell cmdlet should you run?
To answer, select the appropriate options in the answer area.
ANSWER:
Get-IpamRange / Private / True
Q201. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Rights Management Services server role installed.
The domain contains a domain local group named Group1.
You create a rights policy template named Template1. You assign Group1 the rights to Template1.
You need to ensure that all the members of Group1 can use Template1.
What should you do?
A. Configure the email address attribute of Group1.
B. Convert the scope of Group1 to global.
C. Convert the scope of Group1 to universal.
D. Configure the email address attribute of all the users who are members of Group1.
ANSWER: D. Configure the email address attribute of all the users who are members of Group1.
Q202. Hotspot Question
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2.
The network has the physical sites and TCP/IP subnets configured as shown in the following table.
You have a web application named App1 that is hosted on six separate Web servers. DNS has the host names and IP addresses registered as shown in the following table.
You discover that when users connect to appl.contoso.com, they are connected frequently to a server that is not on their local subnet.
You need to ensure that when the users connect to appl.contoso.com, they connect to a server on their local subnet. The connections must be distributed across the servers that host appl.contoso.com on their subnet.
Which two settings should you configure? To answer, select the appropriate two settings in the answer area.
ANSWER:
Enable Round Robin
Enable netmask ordering
Q203. You have a failover cluster named Cluster1 that contains four nodes. All of the nodes run Windows Server 2012 R2.
You need to force every node in Cluster1 to contact immediately the Windows Server Update Services (WSUS) server on your network for updates.
Which tool should you use?
A. The Add-CauClusterRole cmdlet
B. The Wuauclt command
C. The Wusa command
D. The Invoke-CauScan cmdlet
ANSWER: D. The Invoke-CauScan cmdlet
Q204. Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 that runs Windows Server 2012 R2. You create a user account named User1 in the domain. You need to ensure that User1 can use Windows Server Backup to back up Server1. The solution must minimize the number of administrative rights assigned to User1. What should you do?
A. Add User1 to the Backup Operators group.
B. Add User1 to the Power Users group.
C. Assign User1 the Backup files and directories user right and the Restore files and directories user right.
D. Assign User1 the Backup files and directories user right.
ANSWER: D. Assign User1 the Backup files and directories user right.
Q205. Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 and Server2 are configured as shown in the following table.
You need to ensure that when new targets are added to Server1, the targets are registered on Server2 automatically. What should you do on Server1?
A. Configure the security settings of the iSCSI target
B. Run the Set-IscsiTarget cmdlet.
C. Configure the Discovery settings of the iSCSI initiator.
D. Run the Set-WmiInstance cmdlet.
ANSWER: D. Run the Set-WmiInstance cmdlet.
Q206. Your network contains an Active Directory domain named adatum.com. The domain contains two domain controllers that run Windows Server 2012 R2. The domain controllers are configured as shown in the following table.
You log on to DC1 by using a user account that is a member of the Domain Admins group, and then you create a new user account named User1. You need to prepopulate the password for User1 on DC2. What should you do first?
A. Connect to DC2 from Active Directory Users and Computers.
B. Add DC2 to the Allowed RODC Password Replication Policy group.
C. Add the User1 account to the Allowed RODC Password Replication Policy group.
D. Run Active Directory Users and Computers as a member of the Enterprise Admins group.
ANSWER: C. Add the User1 account to the Allowed RODC Password Replication Policy group.
Q207. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. All servers run Windows Server 2012 R2.
You install the DHCP Server server role on both servers.
On Server1, you have the DHCP scope configured as shown in the exhibit. (Click the Exhibit button.)
You need to configure the scope to be load-balanced across Server1 and Server2.
What Windows PowerShell cmdlet should you run on Server1?
To answer, select the appropriate options in the answer area.
 ANSWER:
ANSWER:
Add-DhcpServerv4FAILOVER -PartnerServer Server2 -ScopeID 10.0.0.0
Q208. Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You install the IP Address Management (IPAM) Server feature on a server named Server1 and select Manual as the provisioning method.
The IPAM database is located on a server named SQL1.
You need to configure IPAM to use Group Policy Based provisioning.
What command should you run first?
To answer, select the appropriate options in the answer area.
ANSWER:
Uninstall-WindowsFeature -Name Ipam
Explanation: You cannot change the provisioning method for the current installation of IPAM Server after it has been selected. To change the provisioning method, you must uninstall and reinstall IPAM Server on the computer.
Q209. Your network contains an Active Directory domain named contoso.com. The domain contains an IP Address Management (IPAM) server that uses a Windows Internal Database.
You install a Microsoft SQL Server 2012 instance on a new server.
You need to migrate the IPAM database to the SQL Server instance.
Which cmdlet should you run?
A. Disable-IpamCapability
B. Set-IpamConfiguration
C. Update-IpamServer
D. Move-IpamDatabase
ANSWER: D. Move-IpamDatabase.
Q210. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 is an enterprise root certification authority (CA) for contoso.com. Your user account is assigned the certificate manager role and the auditor role on the contoso.com CA. Your account is a member of the local Administrators group on Server1. You enable CA role separation on Server1.
You need to ensure that you can manage the certificates on the CA. What should you do?
A. Remove your user account from the local Administrators group.
B. Assign the CA administrator role to your user account.
C. Assign your user account the Bypass traverse checking user right.
D. Remove your user account from the Manage auditing and security log user right.
ANSWER: D. Remove your user account from the Manage auditing and security log user right.
Q211. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Federation Services server role installed.
You need to make configuration changes to the Windows Token-based Agent role service.
Which tool should you use?
To answer, select the appropriate tool in the answer area.
Hot Area:
ANSWER:
Internet Information Services (IIS) Manager
Q212. Your network contains four Active Directory forests. Each forest contains an Active Directory Rights Management Services (AD RMS) root cluster.
All of the users in all of the forests must be able to access protected content from any of the forests.
You need to identify the minimum number of AD RMS trusts required.
How many trusts should you identify?
A. 3
B. 6
C. 12
D. 16
ANSWER: C. 12 N*(N-1)
Explanation: N*(N-1). 4 Forests = 4*(4-1) = 12
Q213. Your network contains three Active Directory forests. Each forest contains an Active Directory Rights Management Services (AD RMS) root cluster.
All of the users in all of the forests must be able to access protected content from any of the forests.
You need to identify the minimum number of AD RMS trusts required.
How many trusts should you identify?
A. 3
B. 6
C. 12
D. 16
ANSWER: B. 6
Explanation: N*(N-1) 3 Forests. = 3*(3-1) = 6
Q214. Your network contains an Active Directory domain named adatum.com. All servers run Windows Server 2012 R2. All domain controllers have the DNS Server server role installed. You have a domain controller named DC1. On DC1, you create an Active Directory-integrated zone named adatum.com and you sign the zone by using DNSSEC. You deploy a new read-only domain controller (RODC) named R0DC1. You need to ensure that the contoso.com zone replicates to R0DC1. What should you configure on DC1?
To answer, select the appropriate tab in the answer area.
ANSWER:
Zone Transfers
Q215. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server3. The network contains a standalone server named Server2.
All servers run Windows Server 2012 R2. The servers are configured as shown in the following table.
Server3 hosts an application named App1. App1 is accessible internally by using the URL https://appl.contoso.com. App1 only supports Integrated Windows authentication.
You need to ensure that all users from the Internet are pre-authenticated before they can access Appl.
What should you do?
To answer, drag the appropriate servers to the correct actions. Each server may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Create a relying party trust: Server1
Enable constrained delegation: Server2
Run the Publish New Application Wizard: Server2
Install a certificate for app1.contoso.com: Server2
Q216. Your network contains an Active Directory domain named contoso.com. The domain contains two Active Directory sites named Site1 and Site2.
You discover that when the account of a user in Site1 is locked out, the user can still log on to the servers in Site2 for up to 15 minutes by using Remote Desktop Services (RDS).
You need to reduce the amount of time it takes to synchronize account lockout information across the domain.
Which attribute should you modify?
To answer, select the appropriate attribute in the answer area.
ANSWER:
Options
Q217. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The relevant servers in the domain are configured as shown in the following table.
You plan to create a shared folder on Server1 named Share1. Share1 must only be accessed by users who are using computers that are joined to the domain.
You need to identify which servers must be upgraded to support the requirements of Share1.
In the table below, identify which computers require an upgrade and which computers do not require an upgrade. Make only one selection in each row. Each correct selection is worth one point.
ANSWER:
Only Server1 (File Server) must be upgraded
Q218. Your network contains an Active Directory domain named contoso.com.
You deploy a server named Server1 that runs Windows Server 2012 R2.
A local administrator installs the Active Directory Rights Management Services server role on Server1.
You need to ensure that AD RMS clients can discover the AD RMS cluster automatically.
What should you do?
A. Run the Active Directory Rights Management Services console by using an account that is a member of the Schema Admins group, and then configure the proxy settings.
B. Run the Active Directory Rights Management Services console by using an account that is a member of the Schema Admins group, and then register the Service Connection Point (SCP).
C. Run the Active Directory Rights Management Services console by using an account that is a member of the Enterprise Admins group, and then register the Service Connection Point (SCP).
D. Run the Active Directory Rights Management Services console by using an account that is a member of the Enterprise Admins group, and then configure the proxy settings.
ANSWER: C. Run the Active Directory Rights Management Services console by using an account that is a member of the ENTERPRISE Admins group, and then REGISTER the Service Connection Point (SCP).
Q219. Hotspot Question
Your network contains two Web servers named Server1 and Server2. Both servers run Windows Server 2012 R2.
Server1 and 5erver2 are nodes in a Network Load Balancing (NLB) cluster. The NLB cluster contains an application named App1 that is accessed by using the URL http://app1.contoso.com.
You deploy a new server named Server3 that runs Windows Server 2012 R2. The contoso.com DNS zone contains the records shown in the following table.
You need to add Server3 to the NLB cluster.
What command should you run?
To answer, select the appropriate options in the answer area.
ANSWER:
Get-NlbClusterNode Server1
Add-NlbClusterNode
Q220. Your company has a main office and a remote office. The remote office is used for disaster recovery.
The network contains an Active Directory domain named contoso.com. The domain contains member servers named Server1, Server2, Server3, and Server4. All servers run Windows Server 2012 R2. Server1 and Server2 are located in the main office. Server3 and Server4 are located in the remote office.
All servers have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Storage is replicated between the main office and the remote site. You need to ensure that Cluster1 is available if two nodes in the same office fail. What are two possible quorum configurations that achieve the goal? (Each correct answer presents a complete solution. Choose two.)
A. Node Majority
B. No Majority: Disk Only
C. Node and File Share Majority
D. Node and Disk Majority
Answer: AB
Explanation:
Depending on the quorum configuration option that you choose and your specific settings, the cluster will be configured in one of the following quorum modes:
* (A) Node majority (no witness) Only nodes have votes. No quorum witness is configured. The cluster quorum is the majority of voting nodes in the active cluster membership.
* (B) No majority (disk witness only) No nodes have votes. Only a disk witness has a vote. The cluster quorum is determined by the state of the disk witness. The cluster has quorum if one node is available and communicating with a specific disk in the cluster storage. Generally, this mode is not recommended, and it should not be selected because it creates a single point of failure for the cluster.
* Node majority with witness (disk or file share)
Nodes have votes. In addition, a quorum witness has a vote. The cluster quorum is the majority of voting nodes in the active cluster membership plus a witness vote. A quorum witness can be a designated disk witness or a designated file share witness.
Note:
* Quorum in Windows 2008 R2 referred to a consensus , that is, a majority of votes is required in order to reach quorum and maintain stability of the cluster. A new option created in Windows Server 2012 R2 which was also back ported to Windows Server 2008 R2 SP1 was the ability to stop a node being able to participate in the voting process.
* Dynamic quorum is the ability of the cluster to recalculate quorum on the fly and still maintain a working cluster. This is a huge improvement as we are now able to continue to run a cluster even if the number of nodes remaining in the cluster is less than 50%. This was not possible before but the dynamic quorum concept now allows us to do this. In fact we can reduce the cluster down to the last node (known as last man standing) and still maintain quorum. Reference: Configure and Manage the Quorum in a Windows Server 2012 R2 Failover Cluster
Q221. You are employed as a network administrator at contoso.com. contoso.com has a single Active Directory domain named contoso.com.All servers on the Contoso.com network have Windows Server 2012 R2 installed.
Contoso.com has two servers,named server1 and server2 which are configured in a two-node fail over cluster.
You are currently configuration the quorum settings for the cluster.
You want to make use of a quorum mode that allows each node to vote if it is available and in communication.
Which of the following is the mode you should use?
A. Node Majority
B. Node and Disk Majority
C. Node and File Share Majority
D. No Majority:Disk Only
ANSWER: A. Node Majority
Explanation:
A. Allows each node to vote
B. Allows each node and a disk witness to vote
C. Allows each node and a File share witness to vote
D. Allows one node with a specified disk to have quorum
Q222. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
You need to ensure that a WIM file that is located on a network share is used as the installation source when installing server roles and features on Server1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Run the dism.exe command and specify the /remove-package parameter.
B. Run the Remove-WindowsFeature cmdlet.
C. Enable and configure the Specify settings for optional component installation and component repair
policy setting by using a Group Policy object (GPO).
D. Enable the Enforce upgrade component rules policy setting by using a Group Policy object (GPO).
E. Run the Remove-WindowsPackage cmdlet.
Answer: AC
Explanation:
A: To remove packages from an offline image by using DISM Example:
At a command prompt, specify the package identity to remove it from the image. You can remove multiple packages on one command line.
DISM /Image:C:\test\offline /Remove-Package
/PackageName:Microsoft.Windows.Calc.Demo~6595b6144ccf1df~x86~en~1.0.0.0 /PackageName:Microsoft-Windows-MediaPlayerPackage~31bf3856ad364e35~x86~~6.1.6801.0
C: * You can use Group Policy to specify a Windows image repair source to use within your network. The repair source can be used to restore Windows features or to repair a corrupted Windows image.
* Set Group Policy
You can use Group Policy to specify when to use Windows Update, or a network location as a repair source for features on demand and automatic corruption repair. To configure Group Policy for Feature on Demand
Open the group policy editor. For example, on a computer that is running Windows?8, click Search, click Settings, type Edit Group Policy, and then select the Edit Group Policy setting.
Click Computer Configuration, click Administrative Templates, click System, and then double-click the Specify settings for optional component uninstallation and component repair setting. Select the settings that you want to use for Features on Demand.
Note: * The Windows Imaging Format (WIM) is a file-based disk image format. It was developed by Microsoft to help deploy Windows Vista and subsequent versions of Windows operating system family, as well as Windows Fundamentals for Legacy PCs.
Q223. Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com. The functional level of the forest is Windows Server 2003. You have a domain outside the forest named litwareinc.com. You need to configure an access solution to meet the following requirements:
- Users in litwareinc.com must be able to access resources on a server named Server1 in contoso.com.
- Users in the contoso.com forest must be prevented from accessing any resources in litwareinc.com.
- Users in litwareinc.com must be prevented from accessing any other resources in the contoso.com forest.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Configure SID filtering on the trust.
B. Configure forest-wide authentication on the trust.
C. Create a one-way forest trust.
D. Create a one-way external trust
E. Modify the permission on the Server1 object.
F. Configure selective authentication on the trust.
Answer: DEF
Explanation:
D (not C): litwareinc.com is outside the forest so we need an external trust (not a forest trust).
E: Must grant the required permissions on Server1.
F(not B): For external trust we must either select Domain-Wide or Selective Authentication (forest- wide authentication is not an option)
BCE
Note: * You can create an external trust to form a one-way or two-way, nontransitive trust with domains that are outside your forest. External trusts are sometimes necessary when users need access to resources in a Windows NT 4.0 domain or in a domain that is located in a separate forest that is not joined by a forest trust.
/ To select the scope of authentication for users that are authenticating through a forest trust, click the forest trust that you want to administer, and then click Properties . On the Authentication tab, click either Forest-wide authentication or Selective authentication .
/ To select the scope of authentication for users that are authenticating through an external trust, click the external trust that you want to administer, and then click Properties . On the Authentication tab, click either Domain-wide authentication or Selective authentication .
* The forest-wide authentication setting permits unrestricted access by any users in the trusted forest to all available shared resources in any of the domains in the trusting forest.
* Forest-wide authentication is generally recommended for users within the same organization. Reference: Select the Scope of Authentication for Users
Q224. Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Node1 and Node2. Node1 and Node2 run Windows Server 2012 R2. Node1 and Node2 are configured as a two-node failover cluster named Cluster2. The computer accounts for all of the servers reside in an organizational unit (OU) named Servers. A user named User1 is a member of the local Administrators group on Node1 and Node2. User1 creates a new clustered File Server role named File1 by using the File Server for general use option. A report is generated during the creation of File1 as shown in the exhibit. (Click the Exhibit button.)
![clip_image001[18]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00118_thumb.jpg)
File1 fails to start.
You need to ensure that you can start File1. What should you do?
A. Log on to the domain by using the built-in Administrator for the domain, and then recreate the clustered File Server role by using the File Server for general use option.
B. Recreate the clustered File Server role by using the File Server for scale-out Application data option.
C. Assign the computer account permissions of Cluster2 to the Servers OU.
D. Assign the user account permissions of User1 to the Servers OU.
E. Increase the value of the ms-DS-MachineAccountQuota attribute of the domain.
Answer: B
Q225. Your network contains an Active Directory domain named contoso.com. The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012 R2. DC1 and DC2 fail to replicate Active Directory information. You confirm that DC1 and DC2 have network connectivity. The NTDS Settings of DC2 are configured as shown in the NTDS Settings exhibit. (Click the Exhibit button.)
![clip_image001[22]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00122_thumb.jpg)
DNS is configured as shown in the DNS exhibit. (Click the Exhibit button.)
![clip_image002[6]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0026_thumb.jpg)
You need to ensure that DC1 and DC2 can replicate immediately. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From DC1, restart the Netlogon service.
B. From DC2, run nltest.exe /sync.
C. From DC1, run ipconfig /flushdns.
D. From DC1, run repadmin /syncall.
E. From DC2, run ipconfig /registerdns.
F. From DC2, restart the Netlogon service.
Answer: DE
Explanation: The DC2 name/alias is not available in DNS.
First we register the DC2 name from DC with the ipconfig /registerdns. (E) Then we synchronizes a specified domain controller DC1 (DC2 would also work) with all of its replication partners with repadmin /syncall. (D)
Q226. Your network contains two Active Directory forests named contoso.com and fabrikam.com. A two- way forest trust exists between the forests.
The contoso.com forest contains an enterprise certification authority (CA) named CA1. You implement cross-forest certificate enrollment between the contoso.com forest and the fabrikam.com forest. On CA1, you create a new certificate template named Template1.
You need to ensure that users in the fabrikam.com forest can request certificates that are based on Template1.
Which tool should you use?
A. Sync-ADObject
B. Get-ADObject
C. Set-ADObject
D. Rename-ADObject
ANSWER: A. Sync-ADObject (TestKing)
Q227. Your network contains two Active Directory forests named contoso.com and fabrikam.com. A two- way forest trust exists between the forests.
The contoso.com forest contains an enterprise certification authority (CA) named CA1. You implement cross-forest certificate enrollment between the contoso.com forest and the fabrikam.com forest. On CA1, you create a new certificate template named Template1. You need to ensure that users in the fabrikam.com forest can request certificates that are based on Template1. Which tool should you use?
A. Sync-ADObject
B. Pkiview.msc
C. CertificateServices.ps1
D. Certutil
E. PKISync.ps1
Answer: E.
Explanation: PKISync.ps1 copies objects in the source forest to the target forest.
In cross-forest AD CS deployments, use PKISync.ps1 during initial deployment and to keep resource and account forest PKI objects synchronized.
Q228. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 contains a file server role named FS1 and a generic service role named SVC1. Server1 is the preferred node for FS1. Server2 is the preferred node for SVC1.
You plan to run a disk maintenance tool on the physical disk used by FS1. You need to ensure that running the disk maintenance tool does not cause a failover to occur.
What should you do before you run the tool?
A. Run cluster.exe and specify the pause parameter.
B. Run cluster.exe and specify the offline parameter.
C. Run Suspend-ClusterResource
D. Run Suspend-ClusterNode.
ANSWER: B
Explanation: (http://technet.microsoft.com/en-us/library/ee460986.aspx)
Q229. You work as an administrator at contoso.com. Contoso.com network consists of a single domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 R2 installed. Contoso.com has a server, named SERVER1, which has the AD DS, DHCP and DNS server roles installed. Contoso.com also has a server named SERVER2, which has the DHCP and Remote Access Server Role installed.
You have configured a server, which has the File and Storage Services Server role installed to automatically acquire an IP address.The server is named Server3. You then create a filter on SERVER1.
Which of the following is a reason for this configuration?
A. To make sure that SERVER1 issues Server3 an IP address.
B. To make sure that SERVER1 does not issue SERVER3 an IP address
C. To make sure that SERVER3 acquires a constant IP address from SERVER2 only.
D. To make sure that SERVER3 is configured with a static IP address
ANSWER: B. To make sure that SERVER1 does not issue SERVER3 an IP address.
Q230. You are employed as a senior network administrator at contoso.com. Contoso.com has a single Active Directory Domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior network administrator.
You are currently discussing the Dnslint.exe tool.
Which of the following should this tool be used for ? (Choose all that apply)
A. To help diagnose common DNS name resolution issues
B. For developing scripts for configuring a DNS server
C. To administer the DNS server Service.
D. To look for specific DNS record set and sure that they are consistent across multiple DNS servers.
E. To verify that DNS records used specifially for Active Directory replication are correct
F. To Create and delete zones and resource records.
Answer: ADE
![clip_image002[14]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00214_thumb.jpg)
You have a DHCP server named Server1. Server1 has one network adapter. Server1 is
located on a subnet named Subnet1. Server1 has scope named Scope1. Scope1 contains
IP addresses for the 192.168.1.0/24 network. Your company is migrating the IP addresses
on Subnet1 to use a network ID of 10.10.0.0/16. On Server11 you create a scope named
Scope2. Scope2 contains IP addresses for the 10.10.0.0/16 network.
You need to ensure
that clients on Subnet1 can receive IP addresses from either scope.
What should you
create on Server1?
A. A multicast scope
B. A scope
C. A superscope
D. A split-scope
Answer: C. A superscope.
Your network contains an Active Directory domain named adatum.com. The domain
contains a domain controller named DC1 that runs Windows Server 2012. On Dc1, you
open DNS Manager as shown in the exhibit. (Click the Exhibit button.)
You need to change the zone type of the contoso.com zone from an Active Directoryintegrated
zone to a standard primary zone. What should you do before you change the
zone type?
A. Unsign the zone.
B. Modify the Zone Signing Key (ZSK).
C. Modify the Key Signing Key (KSK).
D. Change the Key Master.
Answer: A. Unsign the zone
Your network contains an Active Directory domain named contoso.com. The domain
contains two servers named Server1 and Server2 that run Windows Server 2012. Server1
has the DHCP Server server role installed. Server2 has the Hyper-V server role installed.
Server2 has an IP address of 192.168.10.50. Server1 has a scope named Scope1 for the
192.168.10.0/24 network. You plan to deploy 20 virtual machines on Server2 that will be
connected to the external network. The MAC addresses for the virtual machines will
begin with 00-15-SD-83-03. You need to configure Server1 to offer the virtual machines
IP addresses from 192.168.10.200 to 192.168.10.21g. Physical computers on the network
must be offered IP addresses outside this range. You want to achieve this goal by using
the minimum amount of administrative effort.
What should you do from the DHCP
console?
A. Create reservations.
B. Create a policy.
C. Delete Scope1 and create two new scopes.
D. Configure Allow filters and Deny filters.
Answer: B
Server1 and Server2 have different processor models from the same manufacturer.
On Server1, you plan to create a virtual machine named VM1. Eventually, VM1 will be exported to Server2.
You need to ensure that when you import VM1 to Server2, you can start VM1 from saved snapshots.
What should you configure on VM1? To answer, select the appropriate node in the answer area.
ANSWER:
(Processor =>) Compatibility
Q183. Hotspot Question
Your network contains two Hyper-V hosts that are configured as shown in the following table.
You create a virtual machine on Server1 named VM1.
You plan to export VM1 from Server1 and import VM1 to Server2. You need to ensure that you can start the imported copy of VM1 from snapshots.
What should you configure on VM1?
To answer, select the appropriate node in the answer area.
ANSWER:
Compatibility
Q184. Your network contains an Active Directory forest named adatum.com. All servers run Windows Server 2012 R2. The domain contains four servers. The servers are configured as shown in the following table.
![clip_image001[58]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00158_thumb.jpg)
You need to deploy IP Address Management (IPAM) to manage DNS and DHCP.
On which server should you install IPAM?
A. Server1
B. Server2
C. Server3
D. Server4
ANSWER: D. Server4.
Explanation: IPAM cannot be installed on Domain Controllers (nor RODCs).
Q185. Your network contains an Active Directory forest named adatum.com. All servers run Windows Server 2012 R2. The domain contains four servers. The servers are configured as shown in the following table.
You need to deploy IP Address Management (IPAM) to manage DNS and DHCP.
On which server should you install IPAM?
A. DC1
B. DC2
C. DC3
D. Server1
ANSWER: D. Server1.
Explanation: IPAM cannot be installed on DCs.
Q186. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2.
You install the DHCP Server server role on Server1 and Server2. You install the IP Address Management (IPAM) Server feature on Server1.
You notice that you cannot discover Server1 or Server2 in IPAM.
You need to ensure that you can use IPAM to discover the DHCP infrastructure.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. On Server2, create an IPv4 scope.
B. On Server1, run the Add-IpamServerInventory cmdlet.
C. On Server2, run the Add-DhcpServerInDc cmdlet
D. On both Server1 and Server2, run the Add-DhcpServerv4Policy cmdlet.
E. On Server1, uninstall the DHCP Server server role.
ANSWER: BC. On Server1, run the Add-IpamServerInventory cmdlet + On Server2, run the Add-DhcpServerInDc cmdlet
Explanation: The Add-IpamServerInventory cmdlet adds a new infrastructure server to the IP Address Management (IPAM) server inventory. Use the fully qualified domain name (FQDN) of the server to add to the server inventory.
The Add-DhcpServerInDC cmdlet adds the computer running the DHCP server service to the list of authorized Dynamic Host Configuration Protocol (DHCP) server services in the Active Directory (AD). A DHCP server service running on a domain joined computer needs to be authorized in AD so that it can start leasing IP addresses on the network.
Q187. Your network contains an Active Directory forest. The forest contains one domain named adatum.com. The domain contains three domain controllers. The domain controllers are configured as shown in the following table.
DC2 has all of the domain-wide operations master roles. DC3 has all of the forest-wide operation master roles. You need to ensure that you can use Password Settings objects (PSOs) in the domain.
What should you do first?
A. Uninstall Active Directory from DC1.
B. Change the domain functional level.
C. Transfer the domain-wide operations master roles.
D. Transfer the forest-wide operations master roles.
ANSWER: A. Uninstall Active Directory from DC1.
Q188. Your network contains an Active Directory forest.
The forest contains one domain named contoso.com. The domain contains three domain controllers. The domain controllers are configured as shown in the following table.
DC1 has all of the operations master roles installed. You transfer all of the operations master roles to DC2, and then you uninstall Active Directory from DC1. You need to ensure that you can use Password Settings objects (PSOs) in the domain.
What should you do?
A. Change the domain functional level.
B. Upgrade DC2.
C. Run the dcgpofix.exe command.
D. Transfer the schema master role.
ANSWER: A. Change the domain functional level.
Q189. The File Server Resource Manager role service is installed on Server1. All servers run Windows Server 2012 R2. A Group Policy object (GPO) named GPO1 is linked to the organizational unit (OU) that contains Server1. The following graphic shows the configured settings in GPO1.
Server1 contains a folder named Folder1. Folder1 is shared as Share1.
You attempt to configure access-denied assistance on Server1, but the Enable access-denied assistance option cannot be selected from File Server Resource Manager.
You need to ensure that you can configure access-denied assistance on Server1 manually by using File Server Resource Manager.
Which two actions should you perform?
A. Set the Enable access-denied assistance on client for all file types policy setting to Disabled for GPO1.
B. Set the Customize message for Access Denied errors policy setting to Not Configured for GPO1.
C. Set the Enable access-denied assistance on client for all file types policy setting to Enabled for GPO1.
D. Set the Customize message for Access Denied errors policy setting to Enabled for GPO1.
ANSWER: CD. Set the Customize message for Access Denied errors policy setting to Enabled for GPO1. Set the Enable access-denied assistance on client for all file types policy setting to Enabled for GPO1.
Q190. Your network contains an Active Directory domain named contoso.com. The domain contains domain controllers that run either Windows Server 2003, Windows Server 2008 R2, or Windows Server 2012 R2.
You plan to implement a new Active Directory forest. The new forest will be used for testing and will be isolated from the production network.
In the test network, you deploy a server named Server1 that runs Windows Server 2012 R2. You need to configure Server1 as a new domain controller in a new forest named contoso.test.
The solution must meet the following requirements:
- The functional level of the forest and of the domain must be the same as that of contoso.com
- Server1 must provide name resolution services for contoso.test
What should you do?
To answer, configure the appropiate options in the answer area.
ANSWER:
Forest functional level: 2003
Domain functional level:2003
Domain Name System (DNS) Server - Checked
Q191. Your network contains an Active Directory forest named contoso.com. The contoso.com domain only contains domain controllers that run Windows Server 2012 R2.
The forest contains a child domain named child.contoso.com. The child.contoso.com domain only contains domain controllers that run Windows Server 2008 R2. The child.contoso.com domain contains a member server named Server1 that runs Windows Server 2012 R2.
You have access to four administrative user accounts in the forest. The administrative user accounts are configured as shown in the following table.
You need to ensure that you can add a domain controller that runs Windows Server 2012 R2 to the child.contoso.com domain.
Which account should you use to run adprep.exe?
A. Admin1
B. Admin2
C. Admin3
D. Admin4
ANSWER: C. Admin3.
Explanation: Make sure you can log on to the infraestructure master with an account that is a member of the Domain Admins group
Q192. Your network contains an Active Directory domain named contoso.com. The domain contains servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the Active Directory Federation Services server role installed. Server2 is a file server.
Your company introduces a Bring Your Own Device (BYOD) policy.
You need to ensure that users can use a personal device to access domain resources by using Single Sign-On (SSO) while they are connected to the internal network.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. Enable the Device Registration Service in Active Directory.
B. Publish the Device Registration Service by using a Web Application Proxy.
C. Configure Active Directory Federation Services (AD FS) for the Device Registration Service.
D. Create and configure a sync share on Server2.
E. Install the Work Folders role service on Server2.
ANSWER: AC. Enable the Device Registration Service in Active Directory + Configure Active Directory Federation Services (AD FS) for the Device Registration Service.
Q193. Your network contains an Active Directory forest named contoso.com. The forest contains four domains. All servers run Windows Server 2012 R2.
Each domain has a user named User1.
You have a file server named Server1 that is used to synchronize user folders by using the
Work Folders role service.
Server1 has a work folder named Sync1.
You need to ensure that each user has a separate folder in Sync1.
What should you do?
A. From Windows Explorer, modify the Sharing properties of Sync1.
B. Run the Set-SyncServerSetting cmdlet.
C. From File and Storage Services in Server Manager, modify the properties of Sync1.
D. Run the Set-SyncShare cmdlet.
ANSWER: D. Run the Set-SyncShare cmdlet.
Q194. Drag and Drop Question
You have a server that runs Windows Server 2012 R2.
You create a new work folder named Share1.
You need to configure Share1 to meet the following requirements:
Ensure that all synchronized copies of Share1 are encrypted. Ensure that clients synchronize to Share1 every 30 minutes. Ensure that Share1 inherits the NTFS permissions of the parent folder.
Which cmdlet should you use to achieve each requirement?
To answer, drag the appropriate cmdlets to the correct requirements. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Set-SyncShare
Set-SyncServerSettings
Set-SyncShare
Q195. You have an Active Directory Rights Management Services (AD RMS) cluster.
You need to prevent users from encrypting new content. The solution must ensure that the users can continue to decrypt content that was encrypted already.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. From the Active Directory Rights Management Services console, enable decommissioning.
B. From the Active Directory Rights Management Services console, create a user exclusion policy.
C. Modify the NTFS permissions of %systemdrive%\inetpub\wwwroot\_wmcs\licensing.
D. Modify the NTFS permissions of %systemdrive%\inetpub\wwwroot\_wmcs\decommission.
E. From the Active Directory Rights Management Services console, modify the rights policy templates.
ANSWER: BE. From the Active Directory Rights Management Services console, create a user exclusion policy + From the Active Directory Rights Management Services console, modify the rights policy templates.
Q196. You deploy an Active Directory Federation Services (AD FS) 2.1 infrastructure. The infrastructure uses Active Directory as the attribute store. Some users report that they fail to authenticate to the AD FS infrastructure. You discover that only users who run third-party web browsers experience issues. You need to ensure that all of the users can authenticate to the AD FS infrastructure successfully. Which Windows PowerShell command should you run?
A. Set-ADFSProperties -ProxyTrustTokenLifetime 1:00:00
B. Set-ADFSProperties -AddProxyAuthenticationRules None
C. Set-ADFSProperties -SSOLifetime 1:00:00
D. Set-ADFSProperties -ExtendedProtectionTokenCheck None
ANSWER: D. Set-ADFSProperties -ExtendedProtectionTokenCheck None.
Explanation:
A. Sets the valid token lifetime for proxy trust tokens (in minutes). This value is used by the federation server proxy to authenticate with its associated federation server.
B. Specifies a policy rule set that can be used to establish authorization permissions for setting up trust proxies. The default value allows the AD FS 2.0 service user account or any member of BUILTIN\Administrators to register a federation server proxy with the Federation Service.
C. Specifies the duration of the single sign-on (SSO) experience for Web browser clients (in minutes).
D. Specifies the level of extended protection for authentication supported by the federation server. Extended Protection for Authentication helps protect against man-in-the-middle (MITM) attacks, in which an attacker intercepts a client’s credentials and forwards them to a server.
Q197. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains four member servers named Server1, Server2, Server3, and Server4. Server1 and Server2 run Windows Server 2008 R2.
Server1 and Server2 have the Hyper-V server role and the Failover Clustering feature installed. Failover Clustering is configured to provide highly available virtual machines by using a cluster named Cluster1.
Cluster1 hosts 10 virtual machines.
Server3 and Server4 run Windows Server 2012 R2.
You install the Hyper-V server role and the Failover Clustering feature on Server3 and Server4. You create a cluster named Cluster2.
You need to migrate cluster resources from Cluster1 to Cluster2. The solution must minimize downtime on the virtual machines.
Which five actions should you perform?
To answer, move the appropriate five actions from the list of actions to the answer area and arrange them in the correct order.
ANSWER:
From Failover Cluster Manager in Cluster2, run the migrate a Cluster Wizard
Shut down all of the virtual machines in Cluster1
Mask the shared storage to prevent the storage from being accessed by Cluster1
Unmask the shared storage to present the storage to Cluster2.
Start the virtual machines in Cluster2
Q198. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role and the Failover Clustering feature installed. Server1 and Server2 are members of a cluster named Cluster1. Cluster1 hosts 10 virtual machines.
When you try to migrate a running virtual machine from one server to another, you receive the following error message:
“There was an error checking for virtual machine compatibility on the target node.”
You need to ensure that the virtual machines can be migrated from one node to another.
From which node should you perform the configuration? To answer, select the appropriate node in the answer area.
ANSWER:
Processor
Q199. Your company has two offices. The offices are located in Seattle and Montreal.
The network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Server1 is located in the Seattle office. Server2 is located in the Montreal office. All servers run Windows Server 2012 R2.
You need to create a DHCP scope for video conferencing in the Montreal office. The scope must be configured as shown in the following table.
Which Windows PowerShell cmdlet should you run?
A. Add-DchpServerv4SuperScope
B. Add-DchpServerv4MulticastScope
C. Add-DHCPServerv4Policy
D. Add-DchpServerv4Scope
ANSWER: B. Add-DchpServerv4MulticastScope.
Q200. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Both servers have multiple IPv4 scopes.
Server1 and Server2 are used to assign IP addresses for the network IDs of 172.20.0.0/16 and 131.107.0.0/16.
You install the IP Address Management (IPAM) Server feature on a server named IPAM1 and configure IPAM1 to manage Server1 and Server2.
Some users from the 172.20.0.0 network report that they occasionally receive an IP address conflict error message.
You need to identify whether any scopes in the 172.20.0.0 network ID conflict with one another.
What Windows PowerShell cmdlet should you run?
To answer, select the appropriate options in the answer area.
ANSWER:
Get-IpamRange / Private / True
Q201. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Rights Management Services server role installed.
The domain contains a domain local group named Group1.
You create a rights policy template named Template1. You assign Group1 the rights to Template1.
You need to ensure that all the members of Group1 can use Template1.
What should you do?
A. Configure the email address attribute of Group1.
B. Convert the scope of Group1 to global.
C. Convert the scope of Group1 to universal.
D. Configure the email address attribute of all the users who are members of Group1.
ANSWER: D. Configure the email address attribute of all the users who are members of Group1.
Q202. Hotspot Question
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2.
The network has the physical sites and TCP/IP subnets configured as shown in the following table.
You have a web application named App1 that is hosted on six separate Web servers. DNS has the host names and IP addresses registered as shown in the following table.
You discover that when users connect to appl.contoso.com, they are connected frequently to a server that is not on their local subnet.
You need to ensure that when the users connect to appl.contoso.com, they connect to a server on their local subnet. The connections must be distributed across the servers that host appl.contoso.com on their subnet.
Which two settings should you configure? To answer, select the appropriate two settings in the answer area.
ANSWER:
Enable Round Robin
Enable netmask ordering
Q203. You have a failover cluster named Cluster1 that contains four nodes. All of the nodes run Windows Server 2012 R2.
You need to force every node in Cluster1 to contact immediately the Windows Server Update Services (WSUS) server on your network for updates.
Which tool should you use?
A. The Add-CauClusterRole cmdlet
B. The Wuauclt command
C. The Wusa command
D. The Invoke-CauScan cmdlet
ANSWER: D. The Invoke-CauScan cmdlet
Q204. Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 that runs Windows Server 2012 R2. You create a user account named User1 in the domain. You need to ensure that User1 can use Windows Server Backup to back up Server1. The solution must minimize the number of administrative rights assigned to User1. What should you do?
A. Add User1 to the Backup Operators group.
B. Add User1 to the Power Users group.
C. Assign User1 the Backup files and directories user right and the Restore files and directories user right.
D. Assign User1 the Backup files and directories user right.
ANSWER: D. Assign User1 the Backup files and directories user right.
Q205. Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 and Server2 are configured as shown in the following table.
You need to ensure that when new targets are added to Server1, the targets are registered on Server2 automatically. What should you do on Server1?
A. Configure the security settings of the iSCSI target
B. Run the Set-IscsiTarget cmdlet.
C. Configure the Discovery settings of the iSCSI initiator.
D. Run the Set-WmiInstance cmdlet.
ANSWER: D. Run the Set-WmiInstance cmdlet.
Q206. Your network contains an Active Directory domain named adatum.com. The domain contains two domain controllers that run Windows Server 2012 R2. The domain controllers are configured as shown in the following table.
You log on to DC1 by using a user account that is a member of the Domain Admins group, and then you create a new user account named User1. You need to prepopulate the password for User1 on DC2. What should you do first?
A. Connect to DC2 from Active Directory Users and Computers.
B. Add DC2 to the Allowed RODC Password Replication Policy group.
C. Add the User1 account to the Allowed RODC Password Replication Policy group.
D. Run Active Directory Users and Computers as a member of the Enterprise Admins group.
ANSWER: C. Add the User1 account to the Allowed RODC Password Replication Policy group.
Q207. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. All servers run Windows Server 2012 R2.
You install the DHCP Server server role on both servers.
On Server1, you have the DHCP scope configured as shown in the exhibit. (Click the Exhibit button.)
You need to configure the scope to be load-balanced across Server1 and Server2.
What Windows PowerShell cmdlet should you run on Server1?
To answer, select the appropriate options in the answer area.
 ANSWER:
ANSWER: Add-DhcpServerv4FAILOVER -PartnerServer Server2 -ScopeID 10.0.0.0
Q208. Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You install the IP Address Management (IPAM) Server feature on a server named Server1 and select Manual as the provisioning method.
The IPAM database is located on a server named SQL1.
You need to configure IPAM to use Group Policy Based provisioning.
What command should you run first?
To answer, select the appropriate options in the answer area.
ANSWER:
Uninstall-WindowsFeature -Name Ipam
Explanation: You cannot change the provisioning method for the current installation of IPAM Server after it has been selected. To change the provisioning method, you must uninstall and reinstall IPAM Server on the computer.
Q209. Your network contains an Active Directory domain named contoso.com. The domain contains an IP Address Management (IPAM) server that uses a Windows Internal Database.
You install a Microsoft SQL Server 2012 instance on a new server.
You need to migrate the IPAM database to the SQL Server instance.
Which cmdlet should you run?
A. Disable-IpamCapability
B. Set-IpamConfiguration
C. Update-IpamServer
D. Move-IpamDatabase
ANSWER: D. Move-IpamDatabase.
Q210. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 is an enterprise root certification authority (CA) for contoso.com. Your user account is assigned the certificate manager role and the auditor role on the contoso.com CA. Your account is a member of the local Administrators group on Server1. You enable CA role separation on Server1.
You need to ensure that you can manage the certificates on the CA. What should you do?
A. Remove your user account from the local Administrators group.
B. Assign the CA administrator role to your user account.
C. Assign your user account the Bypass traverse checking user right.
D. Remove your user account from the Manage auditing and security log user right.
ANSWER: D. Remove your user account from the Manage auditing and security log user right.
Q211. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Federation Services server role installed.
You need to make configuration changes to the Windows Token-based Agent role service.
Which tool should you use?
To answer, select the appropriate tool in the answer area.
Hot Area:
ANSWER:
Internet Information Services (IIS) Manager
Q212. Your network contains four Active Directory forests. Each forest contains an Active Directory Rights Management Services (AD RMS) root cluster.
All of the users in all of the forests must be able to access protected content from any of the forests.
You need to identify the minimum number of AD RMS trusts required.
How many trusts should you identify?
A. 3
B. 6
C. 12
D. 16
ANSWER: C. 12 N*(N-1)
Explanation: N*(N-1). 4 Forests = 4*(4-1) = 12
Q213. Your network contains three Active Directory forests. Each forest contains an Active Directory Rights Management Services (AD RMS) root cluster.
All of the users in all of the forests must be able to access protected content from any of the forests.
You need to identify the minimum number of AD RMS trusts required.
How many trusts should you identify?
A. 3
B. 6
C. 12
D. 16
ANSWER: B. 6
Explanation: N*(N-1) 3 Forests. = 3*(3-1) = 6
Q214. Your network contains an Active Directory domain named adatum.com. All servers run Windows Server 2012 R2. All domain controllers have the DNS Server server role installed. You have a domain controller named DC1. On DC1, you create an Active Directory-integrated zone named adatum.com and you sign the zone by using DNSSEC. You deploy a new read-only domain controller (RODC) named R0DC1. You need to ensure that the contoso.com zone replicates to R0DC1. What should you configure on DC1?
To answer, select the appropriate tab in the answer area.
ANSWER:
Zone Transfers
Q215. Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server3. The network contains a standalone server named Server2.
All servers run Windows Server 2012 R2. The servers are configured as shown in the following table.
Server3 hosts an application named App1. App1 is accessible internally by using the URL https://appl.contoso.com. App1 only supports Integrated Windows authentication.
You need to ensure that all users from the Internet are pre-authenticated before they can access Appl.
What should you do?
To answer, drag the appropriate servers to the correct actions. Each server may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
ANSWER:
Create a relying party trust: Server1
Enable constrained delegation: Server2
Run the Publish New Application Wizard: Server2
Install a certificate for app1.contoso.com: Server2
Q216. Your network contains an Active Directory domain named contoso.com. The domain contains two Active Directory sites named Site1 and Site2.
You discover that when the account of a user in Site1 is locked out, the user can still log on to the servers in Site2 for up to 15 minutes by using Remote Desktop Services (RDS).
You need to reduce the amount of time it takes to synchronize account lockout information across the domain.
Which attribute should you modify?
To answer, select the appropriate attribute in the answer area.
ANSWER:
Options
Q217. Hotspot Question
Your network contains an Active Directory domain named contoso.com. The relevant servers in the domain are configured as shown in the following table.
You plan to create a shared folder on Server1 named Share1. Share1 must only be accessed by users who are using computers that are joined to the domain.
You need to identify which servers must be upgraded to support the requirements of Share1.
In the table below, identify which computers require an upgrade and which computers do not require an upgrade. Make only one selection in each row. Each correct selection is worth one point.
ANSWER:
Only Server1 (File Server) must be upgraded
Q218. Your network contains an Active Directory domain named contoso.com.
You deploy a server named Server1 that runs Windows Server 2012 R2.
A local administrator installs the Active Directory Rights Management Services server role on Server1.
You need to ensure that AD RMS clients can discover the AD RMS cluster automatically.
What should you do?
A. Run the Active Directory Rights Management Services console by using an account that is a member of the Schema Admins group, and then configure the proxy settings.
B. Run the Active Directory Rights Management Services console by using an account that is a member of the Schema Admins group, and then register the Service Connection Point (SCP).
C. Run the Active Directory Rights Management Services console by using an account that is a member of the Enterprise Admins group, and then register the Service Connection Point (SCP).
D. Run the Active Directory Rights Management Services console by using an account that is a member of the Enterprise Admins group, and then configure the proxy settings.
ANSWER: C. Run the Active Directory Rights Management Services console by using an account that is a member of the ENTERPRISE Admins group, and then REGISTER the Service Connection Point (SCP).
Q219. Hotspot Question
Your network contains two Web servers named Server1 and Server2. Both servers run Windows Server 2012 R2.
Server1 and 5erver2 are nodes in a Network Load Balancing (NLB) cluster. The NLB cluster contains an application named App1 that is accessed by using the URL http://app1.contoso.com.
You deploy a new server named Server3 that runs Windows Server 2012 R2. The contoso.com DNS zone contains the records shown in the following table.
You need to add Server3 to the NLB cluster.
What command should you run?
To answer, select the appropriate options in the answer area.
ANSWER:
Get-NlbClusterNode Server1
Add-NlbClusterNode
Q220. Your company has a main office and a remote office. The remote office is used for disaster recovery.
The network contains an Active Directory domain named contoso.com. The domain contains member servers named Server1, Server2, Server3, and Server4. All servers run Windows Server 2012 R2. Server1 and Server2 are located in the main office. Server3 and Server4 are located in the remote office.
All servers have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Storage is replicated between the main office and the remote site. You need to ensure that Cluster1 is available if two nodes in the same office fail. What are two possible quorum configurations that achieve the goal? (Each correct answer presents a complete solution. Choose two.)
A. Node Majority
B. No Majority: Disk Only
C. Node and File Share Majority
D. Node and Disk Majority
Answer: AB
Explanation:
Depending on the quorum configuration option that you choose and your specific settings, the cluster will be configured in one of the following quorum modes:
* (A) Node majority (no witness) Only nodes have votes. No quorum witness is configured. The cluster quorum is the majority of voting nodes in the active cluster membership.
* (B) No majority (disk witness only) No nodes have votes. Only a disk witness has a vote. The cluster quorum is determined by the state of the disk witness. The cluster has quorum if one node is available and communicating with a specific disk in the cluster storage. Generally, this mode is not recommended, and it should not be selected because it creates a single point of failure for the cluster.
* Node majority with witness (disk or file share)
Nodes have votes. In addition, a quorum witness has a vote. The cluster quorum is the majority of voting nodes in the active cluster membership plus a witness vote. A quorum witness can be a designated disk witness or a designated file share witness.
Note:
* Quorum in Windows 2008 R2 referred to a consensus , that is, a majority of votes is required in order to reach quorum and maintain stability of the cluster. A new option created in Windows Server 2012 R2 which was also back ported to Windows Server 2008 R2 SP1 was the ability to stop a node being able to participate in the voting process.
* Dynamic quorum is the ability of the cluster to recalculate quorum on the fly and still maintain a working cluster. This is a huge improvement as we are now able to continue to run a cluster even if the number of nodes remaining in the cluster is less than 50%. This was not possible before but the dynamic quorum concept now allows us to do this. In fact we can reduce the cluster down to the last node (known as last man standing) and still maintain quorum. Reference: Configure and Manage the Quorum in a Windows Server 2012 R2 Failover Cluster
Q221. You are employed as a network administrator at contoso.com. contoso.com has a single Active Directory domain named contoso.com.All servers on the Contoso.com network have Windows Server 2012 R2 installed.
Contoso.com has two servers,named server1 and server2 which are configured in a two-node fail over cluster.
You are currently configuration the quorum settings for the cluster.
You want to make use of a quorum mode that allows each node to vote if it is available and in communication.
Which of the following is the mode you should use?
A. Node Majority
B. Node and Disk Majority
C. Node and File Share Majority
D. No Majority:Disk Only
ANSWER: A. Node Majority
Explanation:
A. Allows each node to vote
B. Allows each node and a disk witness to vote
C. Allows each node and a File share witness to vote
D. Allows one node with a specified disk to have quorum
Q222. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
You need to ensure that a WIM file that is located on a network share is used as the installation source when installing server roles and features on Server1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Run the dism.exe command and specify the /remove-package parameter.
B. Run the Remove-WindowsFeature cmdlet.
C. Enable and configure the Specify settings for optional component installation and component repair
policy setting by using a Group Policy object (GPO).
D. Enable the Enforce upgrade component rules policy setting by using a Group Policy object (GPO).
E. Run the Remove-WindowsPackage cmdlet.
Answer: AC
Explanation:
A: To remove packages from an offline image by using DISM Example:
At a command prompt, specify the package identity to remove it from the image. You can remove multiple packages on one command line.
DISM /Image:C:\test\offline /Remove-Package
/PackageName:Microsoft.Windows.Calc.Demo~6595b6144ccf1df~x86~en~1.0.0.0 /PackageName:Microsoft-Windows-MediaPlayerPackage~31bf3856ad364e35~x86~~6.1.6801.0
C: * You can use Group Policy to specify a Windows image repair source to use within your network. The repair source can be used to restore Windows features or to repair a corrupted Windows image.
* Set Group Policy
You can use Group Policy to specify when to use Windows Update, or a network location as a repair source for features on demand and automatic corruption repair. To configure Group Policy for Feature on Demand
Open the group policy editor. For example, on a computer that is running Windows?8, click Search, click Settings, type Edit Group Policy, and then select the Edit Group Policy setting.
Click Computer Configuration, click Administrative Templates, click System, and then double-click the Specify settings for optional component uninstallation and component repair setting. Select the settings that you want to use for Features on Demand.
Note: * The Windows Imaging Format (WIM) is a file-based disk image format. It was developed by Microsoft to help deploy Windows Vista and subsequent versions of Windows operating system family, as well as Windows Fundamentals for Legacy PCs.
Q223. Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com. The functional level of the forest is Windows Server 2003. You have a domain outside the forest named litwareinc.com. You need to configure an access solution to meet the following requirements:
- Users in litwareinc.com must be able to access resources on a server named Server1 in contoso.com.
- Users in the contoso.com forest must be prevented from accessing any resources in litwareinc.com.
- Users in litwareinc.com must be prevented from accessing any other resources in the contoso.com forest.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Configure SID filtering on the trust.
B. Configure forest-wide authentication on the trust.
C. Create a one-way forest trust.
D. Create a one-way external trust
E. Modify the permission on the Server1 object.
F. Configure selective authentication on the trust.
Answer: DEF
Explanation:
D (not C): litwareinc.com is outside the forest so we need an external trust (not a forest trust).
E: Must grant the required permissions on Server1.
F(not B): For external trust we must either select Domain-Wide or Selective Authentication (forest- wide authentication is not an option)
BCE
Note: * You can create an external trust to form a one-way or two-way, nontransitive trust with domains that are outside your forest. External trusts are sometimes necessary when users need access to resources in a Windows NT 4.0 domain or in a domain that is located in a separate forest that is not joined by a forest trust.
/ To select the scope of authentication for users that are authenticating through a forest trust, click the forest trust that you want to administer, and then click Properties . On the Authentication tab, click either Forest-wide authentication or Selective authentication .
/ To select the scope of authentication for users that are authenticating through an external trust, click the external trust that you want to administer, and then click Properties . On the Authentication tab, click either Domain-wide authentication or Selective authentication .
* The forest-wide authentication setting permits unrestricted access by any users in the trusted forest to all available shared resources in any of the domains in the trusting forest.
* Forest-wide authentication is generally recommended for users within the same organization. Reference: Select the Scope of Authentication for Users
Q224. Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Node1 and Node2. Node1 and Node2 run Windows Server 2012 R2. Node1 and Node2 are configured as a two-node failover cluster named Cluster2. The computer accounts for all of the servers reside in an organizational unit (OU) named Servers. A user named User1 is a member of the local Administrators group on Node1 and Node2. User1 creates a new clustered File Server role named File1 by using the File Server for general use option. A report is generated during the creation of File1 as shown in the exhibit. (Click the Exhibit button.)
![clip_image001[18]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00118_thumb.jpg)
File1 fails to start.
You need to ensure that you can start File1. What should you do?
A. Log on to the domain by using the built-in Administrator for the domain, and then recreate the clustered File Server role by using the File Server for general use option.
B. Recreate the clustered File Server role by using the File Server for scale-out Application data option.
C. Assign the computer account permissions of Cluster2 to the Servers OU.
D. Assign the user account permissions of User1 to the Servers OU.
E. Increase the value of the ms-DS-MachineAccountQuota attribute of the domain.
Answer: B
Q225. Your network contains an Active Directory domain named contoso.com. The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012 R2. DC1 and DC2 fail to replicate Active Directory information. You confirm that DC1 and DC2 have network connectivity. The NTDS Settings of DC2 are configured as shown in the NTDS Settings exhibit. (Click the Exhibit button.)
![clip_image001[22]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00122_thumb.jpg)
DNS is configured as shown in the DNS exhibit. (Click the Exhibit button.)
![clip_image002[6]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0026_thumb.jpg)
You need to ensure that DC1 and DC2 can replicate immediately. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From DC1, restart the Netlogon service.
B. From DC2, run nltest.exe /sync.
C. From DC1, run ipconfig /flushdns.
D. From DC1, run repadmin /syncall.
E. From DC2, run ipconfig /registerdns.
F. From DC2, restart the Netlogon service.
Answer: DE
Explanation: The DC2 name/alias is not available in DNS.
First we register the DC2 name from DC with the ipconfig /registerdns. (E) Then we synchronizes a specified domain controller DC1 (DC2 would also work) with all of its replication partners with repadmin /syncall. (D)
Q226. Your network contains two Active Directory forests named contoso.com and fabrikam.com. A two- way forest trust exists between the forests.
The contoso.com forest contains an enterprise certification authority (CA) named CA1. You implement cross-forest certificate enrollment between the contoso.com forest and the fabrikam.com forest. On CA1, you create a new certificate template named Template1.
You need to ensure that users in the fabrikam.com forest can request certificates that are based on Template1.
Which tool should you use?
A. Sync-ADObject
B. Get-ADObject
C. Set-ADObject
D. Rename-ADObject
ANSWER: A. Sync-ADObject (TestKing)
Q227. Your network contains two Active Directory forests named contoso.com and fabrikam.com. A two- way forest trust exists between the forests.
The contoso.com forest contains an enterprise certification authority (CA) named CA1. You implement cross-forest certificate enrollment between the contoso.com forest and the fabrikam.com forest. On CA1, you create a new certificate template named Template1. You need to ensure that users in the fabrikam.com forest can request certificates that are based on Template1. Which tool should you use?
A. Sync-ADObject
B. Pkiview.msc
C. CertificateServices.ps1
D. Certutil
E. PKISync.ps1
Answer: E.
Explanation: PKISync.ps1 copies objects in the source forest to the target forest.
In cross-forest AD CS deployments, use PKISync.ps1 during initial deployment and to keep resource and account forest PKI objects synchronized.
Q228. Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 contains a file server role named FS1 and a generic service role named SVC1. Server1 is the preferred node for FS1. Server2 is the preferred node for SVC1.
You plan to run a disk maintenance tool on the physical disk used by FS1. You need to ensure that running the disk maintenance tool does not cause a failover to occur.
What should you do before you run the tool?
A. Run cluster.exe and specify the pause parameter.
B. Run cluster.exe and specify the offline parameter.
C. Run Suspend-ClusterResource
D. Run Suspend-ClusterNode.
ANSWER: B
Explanation: (http://technet.microsoft.com/en-us/library/ee460986.aspx)
Suspend-ClusterResource
Turn on maintenance for a disk resource or Cluster Shared Volume so that you can run a disk maintenance tool without triggering failover.
You have configured a server, which has the File and Storage Services Server role installed to automatically acquire an IP address.The server is named Server3. You then create a filter on SERVER1.
Which of the following is a reason for this configuration?
A. To make sure that SERVER1 issues Server3 an IP address.
B. To make sure that SERVER1 does not issue SERVER3 an IP address
C. To make sure that SERVER3 acquires a constant IP address from SERVER2 only.
D. To make sure that SERVER3 is configured with a static IP address
ANSWER: B. To make sure that SERVER1 does not issue SERVER3 an IP address.
Q230. You are employed as a senior network administrator at contoso.com. Contoso.com has a single Active Directory Domain named contoso.com. All servers on the contoso.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior network administrator.
You are currently discussing the Dnslint.exe tool.
Which of the following should this tool be used for ? (Choose all that apply)
A. To help diagnose common DNS name resolution issues
B. For developing scripts for configuring a DNS server
C. To administer the DNS server Service.
D. To look for specific DNS record set and sure that they are consistent across multiple DNS servers.
E. To verify that DNS records used specifially for Active Directory replication are correct
F. To Create and delete zones and resource records.
Answer: ADE
![clip_image002[14]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00214_thumb.jpg)
You have a DHCP server named Server1. Server1 has one network adapter. Server1 is
located on a subnet named Subnet1. Server1 has scope named Scope1. Scope1 contains
IP addresses for the 192.168.1.0/24 network. Your company is migrating the IP addresses
on Subnet1 to use a network ID of 10.10.0.0/16. On Server11 you create a scope named
Scope2. Scope2 contains IP addresses for the 10.10.0.0/16 network.
You need to ensure
that clients on Subnet1 can receive IP addresses from either scope.
What should you
create on Server1?
A. A multicast scope
B. A scope
C. A superscope
D. A split-scope
Answer: C. A superscope.
Your network contains an Active Directory domain named adatum.com. The domain
contains a domain controller named DC1 that runs Windows Server 2012. On Dc1, you
open DNS Manager as shown in the exhibit. (Click the Exhibit button.)
You need to change the zone type of the contoso.com zone from an Active Directoryintegrated
zone to a standard primary zone. What should you do before you change the
zone type?
A. Unsign the zone.
B. Modify the Zone Signing Key (ZSK).
C. Modify the Key Signing Key (KSK).
D. Change the Key Master.
Answer: A. Unsign the zone
Your network contains an Active Directory domain named contoso.com. The domain
contains two servers named Server1 and Server2 that run Windows Server 2012. Server1
has the DHCP Server server role installed. Server2 has the Hyper-V server role installed.
Server2 has an IP address of 192.168.10.50. Server1 has a scope named Scope1 for the
192.168.10.0/24 network. You plan to deploy 20 virtual machines on Server2 that will be
connected to the external network. The MAC addresses for the virtual machines will
begin with 00-15-SD-83-03. You need to configure Server1 to offer the virtual machines
IP addresses from 192.168.10.200 to 192.168.10.21g. Physical computers on the network
must be offered IP addresses outside this range. You want to achieve this goal by using
the minimum amount of administrative effort.
What should you do from the DHCP
console?
A. Create reservations.
B. Create a policy.
C. Delete Scope1 and create two new scopes.
D. Configure Allow filters and Deny filters.
Answer: B





















![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00210_thumb.jpg)








































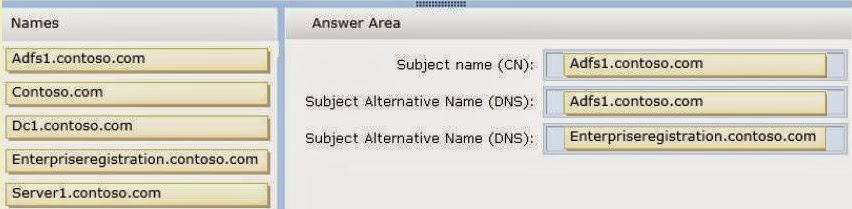













































































































































No hay comentarios:
Publicar un comentario